A perceptual study of Ozisa FM We the people program on the Unknown Gunmen issue in Owerri municipal
DOI:
https://doi.org/10.12928/commicast.v5i3.11697Keywords:
Insecurity, Unknown, Municipal, MediaAbstract
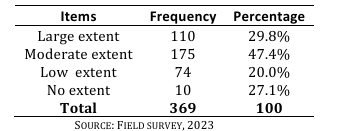
The risk associated with insecurity is alarming as such people need to be security conscious in order to stay safe. The aim of the study was to investigate the public perception of Ozisa FM We the people programme on the Unknown gunmen issue in Owerri municipal council. The study was framed around the agenda setting theory. The study adopted a survey research approach with the use of questionnaire as the instrument for data collection. The population is 171,102, of which 384 were derived using Survey Monkey's online sample size calculator. The non-proportionate quota sampling and purposive sampling approaches were used. The data was analysed using simple percentages. Results revealed that 47.4% of the respondents confirmed that they are exposed to Ozisa FM's We the People Programme on the issue of the Unknown Gunmen to a moderate extent. Findings also showed that 55.0% of the respondents had the perception that the We the people programme has been effective in joining hands with the authority to curtail the Unknown Gunmen's activities. It was concluded that audience are moderately exposed to the Ozisa FM We the people programme. Despite their level of exposure to the programme they still perceive it in a positive light, due to its role in helping curtail the menace of the Unknown gunmen in Owerri, Imo State. It was recommended that they need to sustain their efforts in joining hands with the appropriate stakeholders with the goal of ending the issue of the Unknown gunmen, especially in Imo State.
References
Achumba, I. C., Ighomereho, O. S., & Akpor-Robaro, M. O. M. (2013). Security challenges in Nigeria and the implications for business activities and sustainable development. In Journal of economics and Sustainable Development. academia.edu. https://www.academia.edu/download/30633214/Security_Challenges_in_Nigeria_and_the_Implications_for_Business_Activities_and_Sustainable_Development.pdf
Adeline, N.-U., Ugboma, E. J., Chike, N. M., A., E. I., & Williams, E. E. (2024). Public Perception of Radio Programmes on Parental Sexual Abuse on Children: A Study of Residents of Owerri Metropolis. Asian Journal of Advanced Research and Reports, 18(8), 191–202. https://doi.org/10.9734/ajarr/2024/v18i8721
Adeyemi, O. G. (2011). Appraising the place of the media in combating the Boko Haram terrorism in Nigeria. In Journal of Terrorism studies.
Aka, S. M. (2011). Media coverage of the Niger Delta crisis. In Journal of Media and Conflict Studies.
Asemah, E. S., Gujbawu, M., Ekhareafo, D. O., & Okpanachi, R. A. (2012). Research methods and procedures in mass communication. Jos: Great Future Press, Nigeria.
Asemah, E. S., Nwammuo, A. N., & Nkwam-Uwaoma, A. O. A. (2017). Theories and models of communication. Jos: University Press.
Austin-Egole, I. S., Iheriohanma, E. B. J., Iheanacho, J. I., Ezeji, N. R., Okafor, H. I., & Wokoma, C. U. (2022). Insecurity And The Pauperization Of Residents Of Owerri In Imo State, Nigeria: An Empirical Assessment. European Journal of Social Sciences Studies, 7(3). https://doi.org/10.46827/ejsss.v7i3.1232
Ayitogo, N. (2021). How gunmen attacked Owerri prison, freed 1,844 inmates–Official. In Premium Times.
Christenson, B. L. (2010). The effect of grade-level retention on student success as defined by the Student Success Initiative of Texas. search.proquest.com. https://search.proquest.com/openview/a64cd1b36bdf161fcc8fb6a9748edae2/1?pq-origsite=gscholar&cbl=18750
Elliot, I. J., Ifeoma, O. U., & Etumnu, E. W. (2024). The role of the media in security strategies (on the example of Bayelsa State, Nigeria). Skhid. https://skhid.kubg.edu.ua/article/view/303052
Ewetan, O. O., & Urhie, E. (2014). Insecurity and socio-economic development in Nigeria. Journal of Sustainable Development Studies. https://www.scienta.asia/index.php/jsds/article/view/531
Ezeobi, C., Isiguzo, C., Arinze, G, Eleke, D.C, Ugwu-Nwogo, E, Nworie, B & Uneze, A. (2021). As Insecurity Tears across the South-east. https://www.thisdaylive.com/index.php/2021/07/26/as-insecurity-tears-across-the-south-east/
Fissi, S., Gori, E., Marchi, V., & Romolini, A. (2022). Social media, brand communication and customer engagement in Michelin-starred restaurants during a time of crisis. British Food Journal, 125(13). https://doi.org/10.1108/BFJ-04-2022-0363
Gonina, S. S., & Ngantem, L. M. (2019). Mass media, terrorism and national security: Defining the threats. In Cross-Cultural Communication. academia.edu. https://www.academia.edu/download/106428888/11336.pdf
Jumbo, C. N., Asemah, E. S., Anyanwu, B. J. C., Onyebuhi, A. C., Etumnu, E. W., & Anyi, O. S. A. (2023). Utilisation of new media in communicating insecurity in Southeast Nigeria. COMMICAST, 4(1), 25–36.
Loveth, O., C., A. K., M., O. K., W., E. E., Okodogbe, P., & Odionyenma, C. U. (2022). Effectiveness of Mass Media in the Fight against Drug Abuse among Undergraduates of Tertiary Institutions in Imo State. South Asian Journal of Social Studies and Economics, 1–10. https://doi.org/10.9734/sajsse/2022/v14i330380
Macaulay, S. U., Etumnu, E. W., & Akwari, C. (2021). Perception on the Use of Social Media in Propagating Security Issues in the Post COVID- 19 Era: A Study of Owerri Residents, Imo State. 8, 113–126.
Maxwell, O. J. (2010). Mass media and national security. In Journal of Communications Studies.
Mosharafa, E. (2015). All you need to know about: The cultivation theory. academia.edu. https://www.academia.edu/download/39949289/3-All-you-Need-to-Know.pdf
Nwabueze, C., & Ebeze, E. (2013). Mass media relevance in combating insecurity in Nigeria. In International journal of development and Sustainability. isdsnet.com. https://isdsnet.com/ijds-v2n2-31.pdf
Nwafor, N. K. (2010). Mass media and Nigeria’s quest for national security. In Journal of Communication and Defence Studies.
Nwodu, G. B., Ezeoke, C. B., & Ezeaka, N. B. (2021). Audience Perception of Social Media Messages on Security Challenges in the South East, Nigeria: Implication for Audience Gate Keeping. In World Journal of Innovative Research. researchgate.net. https://www.researchgate.net/profile/Gloria-Eberechukwu-Nwodu/publication/358089643_Audience_perception_of_social_media_messages_on_security_challenges_in_the_Southeast_Nigeria_Implications_for_Audience_Gatekeeping/links/6599a65c0bb2c7472b3764fd/Audience-perception-of-social-media-messages-on-security-challenges-in-the-Southeast-Nigeria-Implications-for-Audience-Gatekeeping.pdf
Nwoga, C., & Taiwo, I. (2021). Assessment Of Southeast Residents’ Perception Of Broadcast Media Coverage Of “Unknown” Gun Men Attacks In Southeast Nigeria. 5, 32–39.
Okolisah, C. P. (2022). The Question of Insecurity and Sustained Socio-Economic Development in Nigeria. Nigerian Journal of Philosophical Studies. https://acjol.org/index.php/njps/article/view/3331
Okoro, N. M., & Chukwuma, O. (2012). Reporting Violent Insurgencies in Postcolonial Nigeria: An Analysis of Audience Assessment of Nigerian Broadcast Media Reportage of the Boko Haram Insurgence. Global Media Journal: Pakistan Edition. https://search.ebscohost.com/login.aspx?direct=true&profile=ehost&scope=site&authtype=crawler&jrnl=20702469&AN=86824474&h=nkEe8SBigq%2FbSeEkm1nAV6MGJwCC4iCPy9AsAnzMP8qRKDuzFjoSSglWw9X9QSox4RN%2Fx%2BKj2kdotgqZgIhGUA%3D%3D&crl=c
Omede, A. J. (2011). Nigeria: Analysing the security challenges of the Goodluck Jonathan administration. In Canadian social science. academia.edu. https://www.academia.edu/download/107539312/2002.pdf
Ottah, I., & Okpoko, C. C. (2024). Mass Media, Communication Policy and National Security. Esut Journal Of Social Sciences. https://www.esutjss.com/index.php/ESUTJSS/article/view/187
Pate, U. A. (2012). Practices and challenges of media performance in conflict-prone multicultural Nigeria. In The companion to communication and development.
Reporters, S. (2021). Timeline: 10 INEC offices attacked by unknown gunmen in May. In Sahara Reporters.
Seimo, S. S. (2010). Media coverage of the Niger Delta crisis. In Journal of Development Studies.
Sylvan, S., Christenson, B., & Ardung, B. (2010). Three-year surveillance of community-acquired and health care-associated Methicillin-Resistant staphylococcus aureus infections in Uppsala County, Sweden. International Journal of Infectious Diseases. https://www.ijidonline.com/article/S1201-9712(10)01974-0/abstract
Television, C. (2021). Interview on security issues in the East with Governor David Umahi unknown gunmen are not unknown. Youtube. https://m.youtube.com
Udeze, S. E., & Chukwuma, O. (2013). Audience assessment of broadcast media surveillance and national security in Nigeria. Covenant. https://journals.covenantuniversity.edu.ng/index.php/cjoc/article/view/22
Ugochukwu, C. C., Joel, N. O., & Nnabuife, C. O. (2021). Social media use in propagating fake news and its influence on security challenges in Nigeria: Study of unknown gunmen. In International Journal of Innovative Science and Research Technology.
Vambe, J. T. (2016). Poverty, insecurity and national development in Nigeria: An overview. In Global Journal of Applied, Management and Social. academia.edu. https://www.academia.edu/download/61822708/POVERTY__INSECURITY_AND_NATIONAL_DEVELOPMENT_IN_NIGERIA-_AN_OVERVIEW20200118-24090-1vpwcrp.pdf
Williams, E. E., Grace, O., Inioluwa, O. V, & Nseobong, U. E. (2024). Tackling Hate Speech on Refugees and Migrants in Nigeria: What can the Media do? Scope. https://hal.science/hal-04562196/
Downloads
Published
How to Cite
Issue
Section
License
Copyright (c) 2024 Chieme Azubuike, Isaac Uche Dorathy

This work is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License.
License and Copyright Agreement
In submitting the manuscript to the journal, the authors certify that:
- They are authorized by their co-authors to enter into these arrangements.
- The work described has not been formally published before, except in the form of an abstract or as part of a published lecture, review, thesis, or overlay journal. Please also carefully read Commicast's Posting Your Article Policy at http://journal2.uad.ac.id/index.php/commicast/about/editorialPolicies#custom-5
- That it is not under consideration for publication elsewhere,
- That its publication has been approved by all the author(s) and by the responsible authorities – tacitly or explicitly – of the institutes where the work has been carried out.
- They secure the right to reproduce any material that has already been published or copyrighted elsewhere.
- They agree to the following license and copyright agreement.
Copyright
Authors who publish with Commicast agree to the following terms:
- Authors retain copyright and grant the journal right of first publication with the work simultaneously licensed under a Creative Commons Attribution License (CC BY-SA 4.0) that allows others to share the work with an acknowledgment of the work's authorship and initial publication in this journal.Â
- Authors are able to enter into separate, additional contractual arrangements for the non-exclusive distribution of the journal's published version of the work (e.g., post it to an institutional repository or publish it in a book), with an acknowledgment of its initial publication in this journal.
- Authors are permitted and encouraged to post their work online (e.g., in institutional repositories or on their website) prior to and during the submission process, as it can lead to productive exchanges, as well as earlier and greater citation of published work.
Licensing for Data Publication
Commicast use a variety of waivers and licenses, that are specifically designed for and appropriate for the treatment of data:
Open Data Commons Attribution License, http://www.opendatacommons.org/licenses/by/1.0/ (default)
Creative Commons CC-Zero Waiver, http://creativecommons.org/publicdomain/zero/1.0/
Open Data Commons Public Domain Dedication and Licence, http://www.opendatacommons.org/licenses/pddl/1-0/
Other data publishing licenses may be allowed as exceptions (subject to approval by the editor on a case-by-case basis) and should be justified with a written statement from the author, which will be published with the article.
Open Data and Software Publishing and Sharing
The journal strives to maximize the replicability of the research published in it. Authors are thus required to share all data, code or protocols underlying the research reported in their articles. Exceptions are permitted but have to be justified in a written public statement accompanying the article.
Datasets and software should be deposited and permanently archived inappropriate, trusted, general, or domain-specific repositories (please consult http://service.re3data.org and/or software repositories such as GitHub, GitLab, Bioinformatics.org, or equivalent). The associated persistent identifiers (e.g. DOI, or others) of the dataset(s) must be included in the data or software resources section of the article. Reference(s) to datasets and software should also be included in the reference list of the article with DOIs (where available). Where no domain-specific data repository exists, authors should deposit their datasets in a general repository such as ZENODO, Dryad, Dataverse, or others.
Small data may also be published as data files or packages supplementary to a research article, however, the authors should prefer in all cases a deposition in data repositories.