Framing analysis of the hacking of Bank Syariah Indonesia by LockBit Ransomware on Republika.co.id and Idntimes.com
DOI:
https://doi.org/10.12928/commicast.v5i3.11663Keywords:
Framing Analysis , Robert N. Entman , Hacking , LockBit , Bank Syariah IndonesiaAbstract
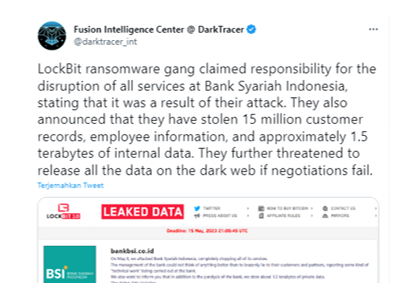
This research aims to analyze the framing of news by Republika.co.id and Idntimes.com regarding the phenomenon of hacking Bank Syariah Indonesia by LockBit 3.0 Ransomware. This research was conducted because the hacking issue of Bank Syariah Indonesia became the major topic of public interest and impacted the perceived security of data and funds. The sensitive issue of security hacking certainly has economic relevance for both the public and investors of Bank Syariah Indonesia. The contribution of this study is to provide a nuanced understanding of how different online media outlets frame the same cybersecurity incident, thereby offering insights into the role of media narratives in shaping public perceptions and trust in the banking sector in the digital era. The research method used is a qualitative approach with Robert N. Entman’s framing analysis model, which has four major elements to interpret the news: define problem, diagnose causes, make moral judgement, and treatment recommendation. The result showed that Republika.co.id sharply criticized Bank Syariah Indonesia in its reporting, but did not emphasize the ransom demand made by LockBit. The criticism in its reporting humanistically and in favor of the community. Meanwhile, Idntimes.com attempted to downplay the inevitability of cyberattacks in the IT world, and framed the news of Bank Syariah Indonesia hacking by LockBit by playing on public emotions using clickbait, rather than highlighting the mitigation steps taken by Bank Syariah Indonesia.
References
Aggarwal, M. (2023). Ransomware Attack: An Evolving Targeted Threat. 2023 14th International Conference on Computing Communication and Networking Technologies, ICCCNT 2023, 1–7. https://doi.org/10.1109/ICCCNT56998.2023.10308249
Aslam, M. (2021). Analisis Sikap dan Posisi Tribun Timur dalam Wacana Polemik Kasus KPK Vs Polri. Jurnal Communio : Jurnal Jurusan Ilmu Komunikasi, 10. No. 1(1), 107–122. https://doi.org/https://doi.org/10.35508/jikom.v10i1.3677
Enomoto, S., Kuzuno, H., Yamada, H., Shiraishi, Y., & Morii, M. (2024). Early mitigation of CPU-optimized ransomware using monitoring encryption instructions. International Journal of Information Security, 23, 3393–3413. https://doi.org/10.1007/s10207-024-00892-2
Eriyanto. (2002). Analisis Framing: Konstruksi, Ideologi, dan Politik Media. LKiS. https://books.google.co.id/books?id=wGwj0CPSjlQC
Eriyanto. (2012). Analisis Framing: Konstruksi, Ideologi, dan Politik Media. LKiS. https://books.google.co.id/books?id=wGwj0CPSjlQC
Fakhruzzaman, M. N., Jannah, S. Z., Ningrum, R. A., & Fahmiyah, I. (2023). Flagging clickbait in Indonesian online news websites using fine-tuned transformers. International Journal of Electrical and Computer Engineering, 13(3), 2921–2930. https://doi.org/10.11591/ijece.v13i3.pp2921-2930
Gulo, A. S., Lasmadi, S., & Nawawi, K. (2021). Cyber Crime dalam Bentuk Phising Berdasarkan Undang-Undang Informasi dan Transaksi Elektronik. PAMPAS: Journal of Criminal Law, 1(2), 68–81. https://doi.org/10.22437/pampas.v1i2.9574
Hamad, I. (2004). Konstruksi Realitas Politik dalam Media Massa: Sebuah Studi Critical Discourse Analysis Terhadap Berita-berita Politik. Granit. https://books.google.co.id/books?id=BkEB7gJQMLQC
Hariyanto, D. (2021). Buku Ajar Pengantar Ilmu Komunikasi. In Pengantar Ilmu Komunikasi. Umsida Press. https://doi.org/https://doi.org/10.21070/2021/978-623-6081-32-7
Hariyanto, D., & Kharina, A. D. (2018). Pemberitaan Pidato Pribumi Anies Baswedan Pada Media Indonesia.Com dan Okezone.Com. Kanal: Jurnal Ilmu Komunikasi, 7(1), 10–16. https://doi.org/10.21070/kanal.v
Hariyanto, D., & Pritituesdina, F. (2018). Analisis Framing Berita Kasus Ahok dalam Polemik Surat Al-Maidah pada Kompas.com dan Republika.co.id. Jurnal Ilmu Komunikasi MEDIAKOM, 2(1), 74–88. https://doi.org/https://doi.org/10.32528/mdk.v2i1.1837
IDNTimes. (2022). Profil Winston Utomo, Kisah Inspiratif di Balik Kesuksesan IDN Media. IDN Times. https://www.idntimes.com/news/indonesia/syifa-putri-naomi/inspiratif-kegigihan-winston-utomo-di-balik-kesuksesan-idn-media
IDNTimes. (2023a). Bareskrim dan BSSN Gelar Penyelidikan Dugaan Peretasan Layanan BSI. IDN Times. https://www.idntimes.com/news/indonesia/irfanfathurohman/bareskrim-dan-bssn-gelar-penyelidikan-dugaan-peretasan-layanan-bsi
IDNTimes. (2023b). Imbas Layanan Error, Dua Direktur BSI Dicopot! IDN Times. https://www.idntimes.com/business/economy/ridwan-aji-pitoko-1/imbas-layanan-error-dua-direktur-bsi-dicopot
IDNTimes. (2023c). Irjen Kemenag Sebut Pelunasan Biaya Haji Terdampak Sistem BSI Eror. IDN Times. https://www.idntimes.com/news/indonesia/muhammad-ilman-nafian-2/irjen-kemenag-sebut-pelunasan-biaya-haji-terdampak-sistem-bsi-eror
IDNTimes. (2023d). Kelompok Hacker LockBit Klaim Sebar Data Nasabah, BSI Buka Suara. IDN Times. https://www.idntimes.com/business/finance/vadhia-lidyana-1/kelompok-hacker-lockbit-klaim-sebar-data-nasabah-bsi-buka-suara
IDNTimes. (2023e). Mobile Banking BSI Eror, Erick Thohir Akui Ada Serangan Siber. IDN Times. https://www.idntimes.com/business/finance/vadhia-lidyana-1/mobile-banking-bsi-eror-erick-thohir-akui-ada-serangan-siber
Irawan, H., Dianita, I., & Salsabila Mulya, A. D. (2021). Peran Bank Syariah Indonesia Dalam Pembangunan Ekonomi Nasional. Jurnal Asy-Syarikah: Jurnal Lembaga Keuangan, Ekonomi Dan Bisnis Islam, 3(2), 147–158. https://doi.org/10.47435/asy-syarikah.v3i2.686
Kompas. (2023). Mengenal Ransomware LockBit 3.0 yang Diduga Serang BSI dan Cara Kerjanya. Kompas.Com. https://tekno.kompas.com/read/2023/05/15/12450037/mengenal-ransomware-lockbit-30-yang-diduga-serang-bsi-dan-cara-kerjanya
Li, X., Zhou, J., Xiang, H., & Cao, J. (2024). Attention Grabbing through Forward Reference: An ERP Study on Clickbait and Top News Stories. International Journal of Human-Computer Interaction, 40(11), 3014–3029. https://doi.org/10.1080/10447318.2022.2158262
Lindgren, B. M., Lundman, B., & Graneheim, U. H. (2020). Abstraction and interpretation during the qualitative content analysis process. International Journal of Nursing Studies, 108, 103632. https://doi.org/10.1016/j.ijnurstu.2020.103632
Maulana, N., Laurens, T., Faiz, H. A., & Patrianti, T. (2024). Manajemen Krisis PT. BSI Tbk Pasca Peretasan Data Nasabah. INNOVATIVE: Journal Of Social Science Research, 4(1), 8244–8258. https://doi.org/https://doi.org/10.31004/innovative.v4i1.8620
Michael, & Susilo, D. (2023). The Effect Of The #AwasModus Campaign At @bankbca Tiktok On Community Financial Literacy. Jurnal Media Dan Komunikasi, 4(1), 18–32. https://doi.org/10.20473/medkom.v4i1.47194
Mohammad Yusuf, & Reza Nurul Ichsan. (2021). Analysis of Banking Performance in The Aftermath of The Merger of Bank Syariah Indonesia in Covid 19. International Journal of Science, Technology & Management, 2(2), 472–478. https://doi.org/10.46729/ijstm.v2i2.182
Mundotiya, R. K., & Yadav, N. (2021). Forward Context-Aware Clickbait Tweet Identification System. International Journal of Ambient Computing and Intelligence, 12(2), 21–32. https://doi.org/10.4018/IJACI.2021040102
Najaf, K., Mostafiz, M. I., & Najaf, R. (2021). Fintech firms and banks sustainability: Why cybersecurity risk matters? International Journal of Financial Engineering, 08(02), 2150019. https://doi.org/10.1142/s2424786321500195
Republika. (2023a). Bila Terkena Ransomware, Proteksi BSI Dinilai Sangat Rentan. Sharia Republika. https://sharia.republika.co.id/berita/rukwil457/bila-terkena-ransomware-proteksi-bsi-dinilai-sangat-rentan
Republika. (2023b). BSI Gangguan, Waketum MUI Minta BSI Serius Hadapi Serangan Siber. Sharia Republika. https://sharia.republika.co.id/berita/ruhbb2370/bsi-gangguan-waketum-mui-minta-bsi-serius-hadapi-serangan-siber
Republika. (2023c). BSI Perkuat Sinergi dengan BSSN Tangani Dugaan Serangan Siber. News Republika. https://news.republika.co.id/berita/rur8h9451/bsi-perkuat-sinergi-dengan-bssn-tangani-dugaan-serangan-siber
Republika. (2023d). Data Nasabah Bocor, Saham BSI Langsung ARB. Sharia Republika. https://sharia.republika.co.id/berita/ruqi9p457/data-nasabah-bocor-saham-bsi-langsung-arb
Republika. (2023e). Layanan BSI Diganggu, LockBit Ransomware Klaim Bertanggung Jawab. Sharia Republika. https://sharia.republika.co.id/berita/ruknti377/layanan-bsi-diganggu-lockbit-ransomware-klaim-bertanggung-jawab
Republika. (2023f). LockBit Klaim Serang BSI, Siapa Saja yang Pernah Jadi Korban? News Republika. https://news.republika.co.id/berita/rukuyj425/lockbit-klaim-serang-bsi-siapa-saja-yang-pernah-jadi-korban
Ridha risma yunita, R. R. Y., Suanti tunggala, S. T., & Ken amasita, K. A. S. (2022). Framing analysis on Luwuk Post on the news of regional head election campaign (Pilkada) Banggai Regency in 2020. Commicast, 3(3), 221–236. https://doi.org/10.12928/commicast.v3i2.5959
Santoso, T. (2022). Metodologi Penelitian Kualitatif. Pustaka Saga. https://repository.petra.ac.id/id/eprint/19963
Simatupang, R. (2021). Analisis Framing Pemberitaan Kompas.Com Tentang Covid-19 Di DKI Jakarta. Jurnal Pustaka Komunikasi, 4(1), 39–52. https://doi.org/10.32509/pustakom.v4i1.1315
Sin, L. A. I. W., & Zolkipli, M. F. (2024). Evolution of Ransomware Tactics and Defenses. Borneo International Journal EISSN 2636-9626, 7(3), 11–25. https://majmuah.com/journal/index.php/bij/article/view/647
Sitohan, G. (2021). Humanitarian news frame in Harian Republika and Kompas on Wamena ferugees (framing analysis on Republika news and Kompas edition 24 – 30 September 2019 on the tragedy of the riots in Wamena). Commicast, 2(2), 98. https://doi.org/10.12928/commicast.v2i2.3351
Sobur, A. (2006). Analisis Teks Media: Suatu Pengantar Untuk Analisis Wacana, Analisis Semiotik, dan Analisis Framing. PT Remaja Rosdakarya.
Sudibyo, A. (2004). Ekonomi Politik Media Penyiaran. LKiS. https://books.google.co.id/books?id=4AIdDg2uBccC
Sugiyono. (2013). Metode Penelitian Kuantitatif, Kualitatif Dan R&D. Alfabeta. https://www.academia.edu/118903676/Metode_Penelitian_Kuantitatif_Kualitatif_dan_R_and_D_Prof_Sugiono
Syam, H. M., Anisah, N., Saleh, R., & Lingga, M. A. (2021). Ideology and media framing: Stigmatisation of LGBT in media coverage in Indonesia. Jurnal Komunikasi: Malaysian Journal of Communication, 37(1), 59–73. https://doi.org/10.17576/JKMJC-2021-3701-04
Tirto. (2023). Serangan Ransomware & Upaya Perbankan Minimalisasi Ancaman Siber. Tirto. https://tirto.id/serangan-ransomware-upaya-perbankan-minimalisasi-ancaman-siber
Ulfa, A. (2021). Dampak Penggabungan Tiga Bank Syariah di Indonesia. Jurnal Ilmiah Ekonomi Islam, 7(2), 1101–1106. https://doi.org/10.29040/jiei.v7i2.2680
West, R., & Turner, L. H. (2017). Pengantar Teori Komunikasi: Analisis dan Aplikasi Buku 2. Salemba Humanika.
Yanuar Rahmadan, S. S. (2021). A Framing Analysis of Indonesian Newspaper Coverage on the Issue of Palm Oil Discrimination Between Indonesia and the European Union. Journal of International Studies, 17, 27–52. https://doi.org/https://doi.org/10.32890/jis2021.17.2
Yurita, I., Kevin Ramadhan, M., Candra, M., & Muhammadiyah Kotabumi, U. (2023). Pengaruh Kemajuan Teknologi Terhadap Perkembangan Tindak Pidana Cybercrime. Jurnal Hukum Legalita, 144–155. https://doi.org/https://doi.org/10.47637/legalita.v5i2.995
Downloads
Published
How to Cite
Issue
Section
License
Copyright (c) 2024 Indah Nurjanah, Didik Hariyanto

This work is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License.
License and Copyright Agreement
In submitting the manuscript to the journal, the authors certify that:
- They are authorized by their co-authors to enter into these arrangements.
- The work described has not been formally published before, except in the form of an abstract or as part of a published lecture, review, thesis, or overlay journal. Please also carefully read Commicast's Posting Your Article Policy at http://journal2.uad.ac.id/index.php/commicast/about/editorialPolicies#custom-5
- That it is not under consideration for publication elsewhere,
- That its publication has been approved by all the author(s) and by the responsible authorities – tacitly or explicitly – of the institutes where the work has been carried out.
- They secure the right to reproduce any material that has already been published or copyrighted elsewhere.
- They agree to the following license and copyright agreement.
Copyright
Authors who publish with Commicast agree to the following terms:
- Authors retain copyright and grant the journal right of first publication with the work simultaneously licensed under a Creative Commons Attribution License (CC BY-SA 4.0) that allows others to share the work with an acknowledgment of the work's authorship and initial publication in this journal.Â
- Authors are able to enter into separate, additional contractual arrangements for the non-exclusive distribution of the journal's published version of the work (e.g., post it to an institutional repository or publish it in a book), with an acknowledgment of its initial publication in this journal.
- Authors are permitted and encouraged to post their work online (e.g., in institutional repositories or on their website) prior to and during the submission process, as it can lead to productive exchanges, as well as earlier and greater citation of published work.
Licensing for Data Publication
Commicast use a variety of waivers and licenses, that are specifically designed for and appropriate for the treatment of data:
Open Data Commons Attribution License, http://www.opendatacommons.org/licenses/by/1.0/ (default)
Creative Commons CC-Zero Waiver, http://creativecommons.org/publicdomain/zero/1.0/
Open Data Commons Public Domain Dedication and Licence, http://www.opendatacommons.org/licenses/pddl/1-0/
Other data publishing licenses may be allowed as exceptions (subject to approval by the editor on a case-by-case basis) and should be justified with a written statement from the author, which will be published with the article.
Open Data and Software Publishing and Sharing
The journal strives to maximize the replicability of the research published in it. Authors are thus required to share all data, code or protocols underlying the research reported in their articles. Exceptions are permitted but have to be justified in a written public statement accompanying the article.
Datasets and software should be deposited and permanently archived inappropriate, trusted, general, or domain-specific repositories (please consult http://service.re3data.org and/or software repositories such as GitHub, GitLab, Bioinformatics.org, or equivalent). The associated persistent identifiers (e.g. DOI, or others) of the dataset(s) must be included in the data or software resources section of the article. Reference(s) to datasets and software should also be included in the reference list of the article with DOIs (where available). Where no domain-specific data repository exists, authors should deposit their datasets in a general repository such as ZENODO, Dryad, Dataverse, or others.
Small data may also be published as data files or packages supplementary to a research article, however, the authors should prefer in all cases a deposition in data repositories.