Cybersecurity and Privacy Governance in IoT-Enabled Social Work: A Systematic Review and Risk Framework
DOI:
https://doi.org/10.12928/biste.v7i4.14589Keywords:
Internet of Things (IoT), Social Work, Cybersecurity, Vulnerable Populations, Governance FrameworkAbstract
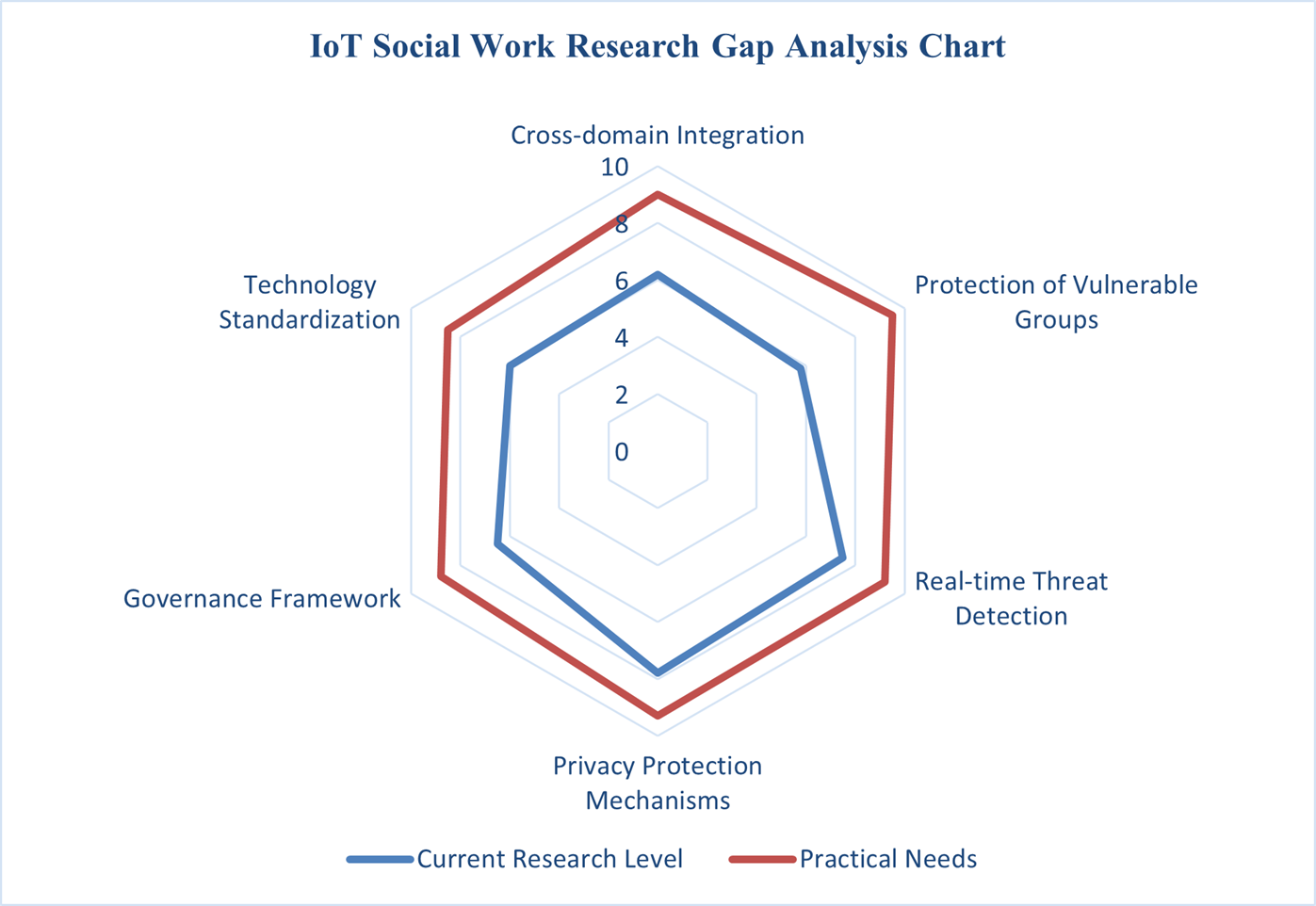
Social work practice is rapidly integrating Internet of Things (IoT) technologies to expand service delivery, yet this integration introduces significant cybersecurity and privacy vulnerabilities that disproportionately threaten vulnerable populations. Existing literature predominantly emphasizes technical security solutions while neglecting the ethical considerations, protective needs of vulnerable groups, and governance frameworks specific to social work contexts. Research Contribution: This study develops the first systematic multidimensional framework integrating engineering and social science perspectives to evaluate IoT cybersecurity, privacy risks, and governance requirements in social work applications. Using a Systematic Literature Review following PRISMA guidelines, we searched five major databases from January 2020 to September 2024. We employed qualitative thematic analysis combined with an innovative quantitative assessment algorithm to score technologies, threats, and governance components across 55 primary studies. Key Findings: Mental health services and vulnerable population support face “very high” privacy risks (PRS > 8.0), primarily from systemic infrastructure weaknesses in consumer-grade devices rather than sophisticated cyberattacks. Homomorphic encryption achieves the highest security score (9.8/10) but exhibits the highest implementation complexity (9.0/10). Federated learning provides an optimal balance (security 8.5, complexity 8.0, cost 6.0). Ethical guidelines demonstrate the highest implementation difficulty (8.2/10), reflecting challenges in translating abstract principles into technical specifications. Quantitative gap analysis identifies vulnerable population protection as the highest research priority (gap score 3.7/10). This study offers an evidence-driven agenda for practitioners and policymakers, proposing context-specific technology selection criteria and adaptive governance models that prioritize interdisciplinary collaboration, ensuring IoT advancements effectively promote social welfare while protecting at-risk individuals.
References
K. Hjelm and L. Hedlund, “Internet-of-Things (IoT) in healthcare and social services – experiences of a sensor system for notifications of deviant behaviours in the home from the users’ perspective,” Health Informatics Journal, vol. 28, no. 1, 2022, https://doi.org/10.1177/14604582221075562.
H. Wan and K. Chin, “Exploring internet of healthcare things for establishing an integrated care link system in the healthcare industry,” International Journal of Engineering Business Management, vol. 13, 2021, https://doi.org/10.1177/18479790211019526.
L.-P. Hung, N.-C. Hsieh, L.-J. Lin, and Z.-J. Wu, “Using Internet of things technology to construct an integrated intelligent sensing environment for long-term care service,” International Journal of Distributed Sensor Networks, vol. 17, 2021, https://doi.org/10.1177/15501477211059392.
Liyakathunisa, A. Alsaeedi, S. Jabeen, and H. Kolivand, “Ambient Assisted Living Framework for Elderly Care Using Internet of Medical Things, Smart Sensors, and GRU Deep Learning Techniques,” Journal of Ambient Intelligence and Smart Environments, vol. 14, no. 1, pp. 5-23, 2021, https://doi.org/10.3233/AIS-210162.
P. Kourtesis, “A Comprehensive Review of Multimodal XR Applications, Risks, and Ethical Challenges in the Metaverse,” Multimodal Technologies and Interaction, vol. 8, no. 11, p. 98, 2024, https://doi.org/10.3390/mti8110098.
M. Adil, H. Song, S. Mastorakis, H. Abulkasim, A. Farouk, and Z. Jin, “UAV-Assisted IoT Applications, Cybersecurity Threats, AI-Enabled Solutions, Open Challenges With Future Research Directions,” IEEE Transactions on Intelligent Vehicles, vol. 9, no. 4, pp. 4583-4605, 2024, https://doi.org/10.1109/TIV.2023.3309548.
V. Bentotahewa, M. Yousif, C. Hewage, L. Nawaf, and J. Williams, “Privacy and Security Challenges and Opportunities for IoT Technologies During and Beyond COVID-19,” in Privacy, Security And Forensics in The Internet of Things (IoT), pp. 51-76, 2022, https://doi.org/10.1007/978-3-030-91218-5_3.
M. V. K. Reddy, P. Chithaluru, P. Narsimhulu, and M. Kumar, “Security, privacy, and trust management of IoT and machine learning-based smart healthcare systems,” Advances in Computers, vol. 137, pp. 141-174, 2025, https://doi.org/10.1016/bs.adcom.2024.06.006.
A. Ullah, M. Azeem, H. Ashraf, A. A. Alaboudi, M. Humayun, and N. Jhanjhi, “Secure Healthcare Data Aggregation and Transmission in IoT — A Survey,” IEEE Access, vol. 9, pp. 16849-16865, 2021, https://doi.org/10.1109/ACCESS.2021.3052850.
S. Datta Burton, L. M. Tanczer, S. Vasudevan, S. Hailes, and M. Carr, “The UK code of practice for consumer IoT cybersecurity: where we are and what next,” The PETRAS National Centre of Excellence for IoT Systems Cybersecurity, 2022, https://doi.org/10.14324/000.rp.10117734.
L. Das, D. Singh, S. Vats, K. Taliyan, D. Bhargava, and D. Bhatnagar, “Smart Healthcare in Improving the Quality of Life: Revolutionizing with Application of IoT and Block Chain Technology,” in 2024 International Conference on Communication, Computer Sciences and Engineering (IC3SE), pp. 1-7, 2024, https://doi.org/10.1109/IC3SE62002.2024.10593009.
T. Poleto, T. C. C. Nepomuceno, V. D. H. de Carvalho, L. C. B. d. O. Friaes, R. C. P. de Oliveira, and C. J. J. Figueiredo, “Information Security Applications in Smart Cities: A Bibliometric Analysis of Emerging Research,” Future Internet, vol. 15, no. 12, p. 393, 2023, https://doi.org/10.3390/fi15120393.
H. Lee, Y. Park, H. Kim, N. Kang, G. Oh, I. Jang, and E. Lee, “Discrepancies in Demand of Internet of Things Services Among Older People and People With Disabilities, Their Caregivers, and Health Care Providers: Face-to-Face Survey Study,” Journal of Medical Internet Research, vol. 22, no. 4, p. e16614, 2020, https://doi.org/10.2196/16614.
K. Assa-Agyei, F. Olajide, and A. Lotfi, “Security and Privacy Issues in IoT Healthcare Application for Disabled Users in Developing Economies,” Journal of Internet Technology and Secured Transactions, vol. 10, no. 1, pp. 770-779, 2022, https://doi.org/10.20533/jitst.2046.3723.2022.0095.
A. Zanella, F. Mason, P. Pluchino, G. Cisotto, V. Orso, and L. Gamberini, “Internet of things for elderly and fragile people,” arXiv preprint arXiv:2006.05709, 2020, https://doi.org/10.48550/arXiv.2006.05709.
E. Blasioli and E. Hassini, “e-Health Technological Ecosystems: Advanced Solutions to Support Informal Caregivers and Vulnerable Populations During the COVID-19 Outbreak,” Telemedicine and e-Health, vol. 28, no. 2, pp. 138-149, 2021, https://doi.org/10.1089/tmj.2020.0522.
S. Piasecki and J. Chen, “Complying with the GDPR when vulnerable people use smart devices,” International Data Privacy Law, vol. 12, no. 2, pp. 113-131, 2022, https://doi.org/10.1093/idpl/ipac001
S. Arisdakessian, O. A. Wahab, A. Mourad, H. Otrok, and M. Guizani, “A Survey on IoT Intrusion Detection: Federated Learning, Game Theory, Social Psychology, and Explainable AI as Future Directions,” IEEE Internet of Things Journal, vol. 10, no. 5, pp. 4059-4092, 2023, https://doi.org/10.1109/JIOT.2022.3203249.
M. Carr and F. Lesniewska, “Internet of Things, Cybersecurity and Governing Wicked Problems: Learning from Climate Change Governance,” International Relations, vol. 34, no. 3, pp. 391-412, 2020, https://doi.org/10.1177/0047117820948247.
M. J. Carey and M. Taylor, “The impact of interprofessional practice models on health service inequity: an integrative systematic review,” Journal of Health Organization and Management, vol. 35, pp. 682-700, 2021, https://doi.org/10.1108/JHOM-04-2020-0165.
J. L. K. Murray, V. Hernandez-Santiago, F. Sullivan, et al., “Interprofessional Collaborative Practice in Health and Social Care for People Living with Multimorbidity: A Scoping Review Protocol,” Systematic Reviews, vol. 14, p. 3, 2025, https://doi.org/10.1186/s13643-024-02730-x.
D. J. Mallinson and S. Shafi, “Smart Home Technology: Challenges and Opportunities for Collaborative Governance and Policy Research,” Review of Policy Research, vol. 39, no. 3, pp. 330-352, 2022, https://doi.org/10.1111/ropr.12470.
K. Klode, A. Ringer, and B. Hølge-Hazelton, “Interprofessional and intersectoral collaboration in the care of vulnerable pregnant women: An interpretive study,” Journal of Interprofessional Care, vol. 39, no. 4, pp. 599-608, 2020, https://doi.org/10.1080/13561820.2020.1761306.
N. Tiffin, A. George, and A. E. LeFevre, “How to use relevant data for maximal benefit with minimal risk: digital health data governance to protect vulnerable populations in low-income and middle-income countries,” BMJ Global Health, vol. 4, p. e001395, 2019, https://doi.org/10.1136/bmjgh-2019-001395.
P. H. Cheong and P. Nyaupane, “Smart campus communication, Internet of Things, and data governance: Understanding student tensions and imaginaries,” Big Data & Society, vol. 9, no. 1, 2022, https://doi.org/10.1177/20539517221092656.
T. Hanjahanja-Phiri, M. Lotto, A. Oetomo, J. Borger, Z. Butt, and P. P. Morita, “Ethical considerations of public health surveillance in the age of the internet of things technologies: A perspective,” Digital Health, vol. 10, 2024, https://doi.org/10.1177/20552076241296578.
J. A. Martínez, J. L. Hernández-Ramos, V. Beltrán, A. Skarmeta, and P. M. Ruiz, “A user-centric Internet of Things platform to empower users for managing security and privacy concerns in the Internet of Energy,” International Journal of Distributed Sensor Networks, vol. 13, no. 8, 2017, https://doi.org/10.1177/1550147717727974.
A. Alexandru, M. Ianculescu, I. E. Giura, and F. Pop, “Managing Cybersecurity Threats for Seniors’ Digital Needs Using Age-Friendly Remote Healthcare Monitoring Model,” in 2022 E-Health and Bioengineering Conference (EHB), pp. 1-4, 2022, https://doi.org/10.1109/EHB55594.2022.9991316.
K. Nordesjö and G. Scaramuzzino, “Digitalization, stress, and social worker–client relationships during the COVID-19 pandemic,” Journal of Social Work, vol. 23, no. 6, pp. 1080-1098, 2023, https://doi.org/10.1177/14680173231180309.
D. Huang, Y. Luo, and J. Lu, “Towards Digital Adaption: An Exploration of Chinese Social Workers’ Experiences of Digital Service Challenges and Coping Strategies in the Context of COVID-19,” The British Journal of Social Work, vol. 55, no. 1, pp. 45–64, 2025, https://doi.org/10.1093/bjsw/bcae125.
L. Fiorini, E. Rovini, A. Sorrentino, O. Khalid, L. Coviello, L. Radi, L. Toccafondi, and F. Cavallo, “Can assistive technology support social services during Covid-19 emergency? Barriers and opportunities,” Int J Interact Des Manuf, vol. 16, pp. 359–370, 2022, https://doi.org/10.1007/s12008-021-00836-3.
A. Kumar and K. Sharma, “Digital Transformation and Emerging Technologies for COVID-19 Pandemic: Social, Global, and Industry Perspectives,” in Artificial Intelligence and Machine Learning for COVID-19, vol. 924, 2021. https://doi.org/10.1007/978-3-030-60188-1_4.
M. A. Habib et al., “Privacy-based medical data protection against internal security threats in heterogeneous Internet of Medical Things,” International Journal of Distributed Sensor Networks, vol. 15, no. 9, 2019, https://doi.org/10.1177/1550147719875653.
N. Shirvanian, M. Shams, A. M. Rahmani, J. Lansky, S. Mildeova, and M. Hosseinzadeh, “The Internet of Things in Elderly Healthcare Applications: A Systematic Review and Future Directions,” IEEE Access, vol. 13, pp. 71335-71373, 2025, https://doi.org/10.1109/ACCESS.2025.3562147.
S. Saeed, S. A. Altamimi, N. A. Alkayyal, E. Alshehri, and D. A. Alabbad, “Digital Transformation and Cybersecurity Challenges for Businesses Resilience: Issues and Recommendations,” Sensors, vol. 23, no. 15, p. 6666, 2023, https://doi.org/10.3390/s23156666.
L. J. Ramirez Lopez, P. A. Buitrago Pineda, J. M. Perez Rincon, and W. M. Rojas Reales, “A systematic review on blockchain in electronic prescriptions and electronic medical records using PRISMA methodology in databases,” Informatics in Medicine Unlocked, vol. 50, p. 101525, 2024, https://doi.org/10.1016/j.imu.2024.101525.
H. A. Long, D. P. French, and J. M. Brooks, “Optimising the value of the critical appraisal skills programme (CASP) tool for quality appraisal in qualitative evidence synthesis,” Research Methods in Medicine & Health Sciences, vol. 1, no. 1, pp. 31-42, 2020, https://doi.org/10.1177/2632084320947559.
H. El-Sofany, S. A. El-Seoud, O. H. Karam, et al., “Using machine learning algorithms to enhance IoT system security,” Scientific Reports, vol. 14, p. 12077, 2024, https://doi.org/10.1038/s41598-024-62861-y.
S. Ismail, H. Reza, H. K. Zadeh, and F. Vasefi, “A Blockchain-based IoT Security Solution Using Multichain,” in 2023 IEEE 13th Annual Computing and Communication Workshop and Conference (CCWC), pp. 1105-1111, 2023, https://doi.org/10.1109/CCWC57344.2023.10099128.
E. Korol and S. Korol, “Governing the Commons through Rule Hybridity: Interactions Between Formal Institutions and Informal Norms in CPR Management,” Journal of Business and Management Studies, vol. 7, pp. 88-102, 2025, https://doi.org/10.32996/jbms.2025.7.4.4.
H. Wang, W. Lu, J. Söderlund, and K. Chen, “The Interplay Between Formal and Informal Institutions in Projects: A Social Network Analysis,” Project Management Journal, vol. 49, no. 4, pp. 20-35, 2018, https://doi.org/10.1177/8756972818781629.
H. Ahmadi, G. Arji, L. Shahmoradi, R. Safdari, M. Nilashi, and M. Alizadeh, “The application of internet of things in healthcare: a systematic literature review and classification,” Universal Access in the Information Society, vol. 18, pp. 837–869, 2019, https://doi.org/10.1007/s10209-018-0618-4.
I. de la Torre Díez, S. G. Alonso, S. Hamrioui, E. M. Cruz, L. M. Nozaleda, and M. A. Franco, “IoT-Based Services and Applications for Mental Health in the Literature,” J Med Syst, vol. 43, no. 1, p. 11, 2018, https://doi.org/10.1007/s10916-018-1130-3.
S. Y. Y. Tun, S. Madanian, and F. Mirza, “Internet of things (IoT) applications for elderly care: a reflective review,” Aging Clin Exp Res, vol. 33, no. 4, pp. 855-867, 2021, https://doi.org/10.1007/s40520-020-01545-9.
A. Carboni, D. Russo, D. Moroni, and P. Barsocchi, “Privacy by Design in Systems for Assisted Living, Personalised Care, and Wellbeing: A Stakeholder Analysis,” Frontiers in Digital Health, vol. 4, p. 934609, 2023, https://doi.org/10.3389/fdgth.2022.934609.
Y. Yamout, T. S. Yeasar, S. Iqbal, and M. Zulkernine, “Beyond smart homes: An in-depth analysis of smart aging care system security,” ACM Computing Surveys, vol. 56, no. 2, pp. 1-35, 2023, https://doi.org/10.1145/3610225.
C. H. E. N. Mengxuan, “Privacy Protection and Robocare in Long Term Care,” Revista Facultății de Drept Oradea, vol. 1, no. 1, pp. 97-110, 2023, https://www.ceeol.com/search/article-detail?id=1327978.
V. Fiorentino, M. Romakkaniemi, T. Harrikari, S. Saraniemi, and L. Tiitinen, “Towards digitally mediated social work - the impact of the COVID-19 pandemic on encountering clients in social work,” Qualitative Social Work, vol. 22, no. 3, pp. 448-464, 2023, https://doi.org/10.1177/14733250221075603.
M. Elhoseny, N. N. Thilakarathne, M. I. Alghamdi, R. K. Mahendran, A. A. Gardezi, H. Weerasinghe, and A. Welhenge, “Security and Privacy Issues in Medical Internet of Things: Overview, Countermeasures, Challenges and Future Directions,” Sustainability, vol. 13, no. 21, p. 11645, 2021, https://doi.org/10.3390/su132111645.
A. Chacko and T. Hayajneh, “Security and Privacy Issues with IoT in Healthcare,” EAI Endorsed Transactions on Pervasive Health and Technology, vol. 4, no. 16, p. e4, 2018, https://doi.org/10.4108/eai.13-7-2018.155079.
O. I. Obaid and S. Salman, “Security and Privacy in IoT-based Healthcare Systems: A Review,” Mesopotamian Journal of Computer Science, pp. 46-55, 2022, https://doi.org/10.58496/MJCSC/2022/007.
W. Shafik, “Smart biomedical devices for smart healthcare,” in Machine Learning Models and Architectures for Biomedical Signal Processing, pp. 421-448, 2025, https://doi.org/10.1016/B978-0-443-22158-3.00017-X.
M. N. H. Zarkia and S. Usman, “IoT Data Breaches and Privacy Issues in Healthcare System”, OIJI, vol. 13, no. 1, pp. 41–55, 2025. https://doi.org/10.11113/oiji2025.13n1.327.
P. Harvey, O. Toutsop, K. Kornegay, E. Alale, and D. Reaves, “Security and Privacy of Medical Internet of Things Devices for Smart Homes,” in 2020 7th International Conference on Internet of Things: Systems, Management and Security (IOTSMS), pp. 1-6, 2020, https://doi.org/10.1109/IOTSMS52051.2020.9340231.
G. Nithyavani and G. Raja, “A Comprehensive Survey on Security and Privacy Challenges in Internet of Medical Things Applications: Deep Learning and Machine Learning Solutions, Obstacles, and Future Directions,” IEEE Access, pp. 1-1, 2025, https://doi.org/10.1109/ACCESS.2025.3588489.
J. B. Awotunde, R. G. Jimoh, S. O. Folorunso, E. A. Adeniyi, K. M. Abiodun, and O. O. Banjo, “Privacy and Security Concerns in IoT-Based Healthcare Systems,” in The Fusion of Internet of Things, Artificial Intelligence, and Cloud Computing in Health Care, pp. 101–122, 2021, https://doi.org/10.1007/978-3-030-75220-0_6
R. Katsuya and X. M. Liu, “Policy and Management Implications of Firmware Vulnerabilities in Medical IoT Devices: A Multi-Case Analysis,” Journal of Science and Technology Policy Management, 2025, https://doi.org/10.1108/JSTPM-09-2024-0346.
L. Jedrzejczyk, B. A. Price, A. K. Bandara, and B. Nuseibeh, “I Know What You Did Last Summer: Risks of Location Data Leakage in Mobile and Social Computing,” Technical Report, 2009, https://doi.org/10.21954/ou.ro.0001608c.
C. M. Mejía-Granda, J. L. Fernández-Alemán, J. M. Carrillo-de-Gea, and J. A. García-Berná, “Security vulnerabilities in healthcare: an analysis of medical devices and software,” Med Biol Eng Comput, vol. 62, no. 1, pp. 257-273, 2024, https://doi.org/10.1007/s11517-023-02912-0.
H. Li, H. Zhu, S. Du, X. Liang, and X. Shen, “Privacy Leakage of Location Sharing in Mobile Social Networks: Attacks and Defense,” IEEE Transactions on Dependable and Secure Computing, vol. 15, no. 4, pp. 646-660, 2018, https://doi.org/10.1109/TDSC.2016.2604383.
T. Bakhshi, B. Ghita, and I. Kuzminykh, “A Review of IoT Firmware Vulnerabilities and Auditing Techniques,” Sensors, vol. 24, no. 2, Art. no. 708, 2024, https://doi.org/10.3390/s24020708.
K. P. Tang, P. Keyani, J. Fogarty, and J. I. Hong, “Putting people in their place: an anonymous and privacy-sensitive approach to collecting sensed data in location-based applications,” in Proceedings of the SIGCHI Conference on Human Factors in Computing Systems (CHI ‘06), 2006, pp. 93-102, https://doi.org/10.1145/1124772.1124788.
S. Madanian, T. Chinbat, M. Subasinghage, D. Airehrour, F. Hassandoust, and S. Yongchareon, “Health IoT Threats: Survey of Risks and Vulnerabilities,” Future Internet, vol. 16, no. 11, p. 389, Nov. 2024, https://doi.org/10.3390/fi16110389.
A. Karanja, D. W. Engels, G. Zerouali, and A. Francisco, “Unintended Consequences of Location Information: Privacy Implications of Location Information Used in Advertising and Social Media,” SMU Data Science Review, vol. 1, no. 3, p. 13, 2018, https://scholar.smu.edu/datasciencereview/vol1/iss3/13/.
L. Baruh and M. Popescu, “Big data analytics and the limits of privacy self-management,” New Media & Society, vol. 19, no. 4, pp. 579-596, 2015, https://doi.org/10.1177/1461444815614001.
H. Jiang, J. Li, P. Zhao, F. Zeng, Z. Xiao, and A. Iyengar, “Location Privacy-preserving Mechanisms in Location-based Services: A Comprehensive Survey,” ACM Computing Surveys, vol. 54, no. 1, p. 4, 2022, https://doi.org/10.1145/3423165.
E. Toch, Y. Wang, and L. F. Cranor, “Personalization and privacy: a survey of privacy risks and remedies in personalization-based systems,” User Modeling and User-Adapted Interaction, vol. 22, pp. 203–220, 2012, https://doi.org/10.1007/s11257-011-9110-z.
L. J. Gutierrez, K. Rabbani, O. J. Ajayi, S. K. Gebresilassie, J. Rafferty, L. A. Castro, and O. Banos, “Internet of Things for Mental Health: Open Issues in Data Acquisition, Self-Organization, Service Level Agreement, and Identity Management,” Int J Environ Res Public Health, vol. 18, no. 3, p. 1327, 2021, https://doi.org/10.3390/ijerph18031327.
M. R. Abdmeziem and A. A. Nacer, “Leveraging IoT and LLM for Depression and Anxiety Disorders: A Privacy Preserving Perspective,” Security and Privacy, vol. 8, no. 4, 2025, https://doi.org/10.1002/spy2.70061.
E. S. N. Joshua, D. Bhattacharyya, and N. T. Rao, “Managing information security risk and Internet of Things (IoT) impact on challenges of medicinal problems with complex settings: a complete systematic approach,” in Multi-Chaos, Fractal and Multi-Fractional Artificial Intelligence of Different Complex Systems, pp. 291-310, 2022, https://doi.org/10.1016/B978-0-323-90032-4.00007-9.
C. Mehra and A. K. Sharma, “Safeguarding the Landscape of Mental Wellness: Analyzing Cyber Threats and Mitigation Strategies in Digital Healthcare,” Procedia Computer Science, vol. 260, pp. 22-31, 2025, https://doi.org/10.1016/j.procs.2025.03.173.
A. S. Malik, S. Acharya, and S. Humane, “Exploring the Impact of Security Technologies on Mental Health: A Comprehensive Review,” Cureus, vol. 16, no. 2, p. e53664, 2024, https://doi.org/10.7759/cureus.53664.
S. Sannon and A. Forte, “Privacy Research with Marginalized Groups: What We Know, What’s Needed, and What’s Next,” Proc. ACM Hum.-Comput. Interact., vol. 6, no. CSCW2, p. 455, 2022, https://doi.org/10.1145/3555556.
N. Warford, T. Matthews, K. Yang, O. Akgul, S. Consolvo, and P. G. Kelley, “SoK: A Framework for Unifying At-Risk User Research,” in 2022 IEEE Symposium on Security and Privacy (SP), 2022, pp. 2344-2360, https://doi.org/10.1109/SP46214.2022.9833643.
T. Wilson, “The Unintended Harm of IoT Devices in Assistive Technology Distribution Programs,” in 2024 IEEE European Symposium on Security and Privacy Workshops (EuroS&PW), pp. 658-665, 2024, https://doi.org/10.1109/EuroSPW61312.2024.00080.
Y. Zou, K. Sun, T. Afnan, R. Abu-Salma, R. Brewer, and F. Schaub, “Cross-Contextual Examination of Older Adults’ Privacy Concerns, Behaviors, and Vulnerabilities,” Proceedings on Privacy Enhancing Technologies, vol. 2024, no. 1, pp. 133–150, 2024, https://doi.org/10.56553/popets-2024-0009.
M. Pérez-Escolar and F. Canet, “Research on vulnerable people and digital inclusion: toward a consolidated taxonomical framework,” Universal Access in the Information Society, vol. 22, pp. 1059–1072, 2023, https://doi.org/10.1007/s10209-022-00867-x.
P. Phiayura, F. Hassandoust, and A. Liew, “Digital Safety and Vulnerable Groups: A Systematic Review of Barriers, Enablers, and Multi-Level Interventions,” The University of Auckland Business School Research Paper, 2025, https://doi.org/10.2139/ssrn.5414835.
K. Renaud and L. Coles-Kemp, “Accessible and Inclusive Cyber Security: A Nuanced and Complex Challenge,” SN Computer Science, vol. 3, no. 346, 2022, https://doi.org/10.1007/s42979-022-01239-1.
C. K. Sanders and E. Scanlon, “The Digital Divide Is a Human Rights Issue: Advancing Social Inclusion Through Social Work Advocacy,” Journal of Human Rights and Social Work, vol. 6, no. 2, pp. 130–143, 2021, https://doi.org/10.1007/s41134-020-00147-9.
U. Chibunna, O. Hamza, A. Collins, J. Onoja, A. Eweje, A. Daraojimba, and A. Pub, “Building Digital Literacy and Cybersecurity Awareness to Empower Underrepresented Groups in the Tech Industry,” International Journal of Multidisciplinary Research and Growth Evaluation, vol. 1, no. 1, pp. 125-138, 2020, https://doi.org/10.54660/.IJMRGE.2020.1.1.125-138.
P. N. Rambharak, “Managing Technology Risk among Senior Citizens and People Living with Disabilities in Guyana,” Texila International Journal of Management, vol. 11, no. 2, p. ART039, 2025, https://doi.org/10.21522/TIJMG.2015.11.02.ART039.
B. Duc Manh, C.-H. Nguyen, D. Thai Hoang, D. N. Nguyen, M. Zeng, and Q.-V. Pham, “Privacy-Preserving Cyberattack Detection in Blockchain-Based IoT Systems Using AI and Homomorphic Encryption,” IEEE Internet of Things Journal, vol. 12, no. 11, pp. 16478-16492, 2025, https://doi.org/10.1109/JIOT.2025.3535792.
F. Fang, L. Feng, J. Xie, J. Liu, Z. Yuan, and X. Deng, “BCFL: A Trustworthy and Efficient Federated Learning Framework Based on Blockchain In IoT,” in 2024 27th International Conference on Computer Supported Cooperative Work in Design (CSCWD), pp. 2394-2399, 2024,https://doi.org/10.1109/CSCWD61410.2024.10580415.
S. Ullah, J. Li, J. Chen, I. Ali, S. Khan, and M. T. Hussain, “Homomorphic Encryption Applications for IoT and Light-Weighted Environments: A Review,” IEEE Internet of Things Journal, vol. 12, no. 2, pp. 1222-1246, 2025, https://doi.org/10.1109/JIOT.2024.3472029.
R. Hamza, A. Hassan, A. Ali, M. B. Bashir, S. M. Alqhtani, T. M. Tawfeeg, and A. Yousif, “Towards Secure Big Data Analysis via Fully Homomorphic Encryption Algorithms,” Entropy, vol. 24, no. 4, p. 519, 2022, https://doi.org/10.3390/e24040519.
A. Eleyan, H. Ahmed, and T. Bejaoui, “Leveraging A Deep Learning-Based Privacy Compliance Framework For IoT Applications,” in 2025 5th IEEE Middle East and North Africa Communications Conference (MENACOMM), pp. 1-6, 2025, https://doi.org/10.1109/MENACOMM62946.2025.10911034.
A. Acar, H. Aksu, A. S. Uluagac, and M. Conti, “A Survey on Homomorphic Encryption Schemes: Theory and Implementation,” ACM Computing Surveys, vol. 51, no. 4, 2019, https://doi.org/10.1145/3214303.
M. El-Hajj, A. E. Attar, A. Fadllallah, and R. Khatoun, “Securing Fault Diagnosis in IoT-Enabled Industrial Systems Using Homomorphic Encryption,” in 2025 12th IFIP International Conference on New Technologies, Mobility and Security (NTMS), pp. 280-287, 2025, https://doi.org/10.1109/NTMS65597.2025.11076966.
J. H. Cheon, D. Kim, and D. Kim, “Efficient Homomorphic Comparison Methods with Optimal Complexity,” in Advances in Cryptology – ASIACRYPT 2020, pp. 241–270, 2020, https://doi.org/10.1007/978-3-030-64834-3_8.
A. Szczegielniak-Rekiel, K. Kanciak, and J. M. Kelner, “Zero-Knowledge Proof in 5G and Beyond Technologies: State of the Arts, Practical Aspects, Applications, Security Issues, Open Challenges, and Future Trends,” IEEE Access, vol. 13, pp. 138352-138380, 2025, https://doi.org/10.1109/ACCESS.2025.3596122.
A. D. Dwivedi, R. Singh, U. Ghosh, and C. S. Rathore, “Privacy preserving authentication system based on non-interactive zero knowledge proof suitable for Internet of Things,” Journal of Ambient Intelligence and Humanized Computing, vol. 13, pp. 4639–4649, 2022, https://doi.org/10.1007/s12652-021-03459-4.
A. Khamesra, P. Selvaraj, and I. Singh, “Data Encryption in 6G Networks: A Zero- Knowledge Proof Model,” in 2024 8th International Conference on I-SMAC (IoT in Social, Mobile, Analytics and Cloud) (I-SMAC), pp. 577-585, 2024, https://doi.org/10.1109/I-SMAC61858.2024.10714853.
A. T. Kudiwahove, “Authentication Model for KYC Optimization in Zimbabwean Businesses Implementing Zero Knowledge Proof for Enhanced Privacy and Secure Customer Onboarding,” International Journal of Computer Science and Mobile Computing (IJCSMC), vol. 14, no. 6, pp. 155-163, 2025, https://doi.org/10.47760/IJCSMC.2025.V14I06.016.
S. Prabowo, A. G. Putrada, I. D. Oktaviani, M. Abdurohman, M. Janssen, and H. H. Nuha, “Privacy-Preserving Tools and Technologies: Government Adoption and Challenges,” IEEE Access, vol. 13, pp. 33904-33934, 2025, https://doi.org/10.1109/ACCESS.2025.3540878.
Y. Chen, X. Lin, G. Li, L. Chen, J. Wang, and S. Liao, “Trading Trust for Privacy: Socially-Motivated Personalized Privacy-Preserving Collaborative Learning in IoT,” in 2024 27th International Conference on Computer Supported Cooperative Work in Design (CSCWD), pp. 935-940, 2024, https://doi.org/10.1109/CSCWD61410.2024.10580732.
T. Z. Sana, S. Abdulla, A. Nag, A. Das, M. M. Hassan, and Z. Z. Fiza, “Advancing Federated Learning: A Systematic Literature Review of Methods, Challenges, and Applications,” IEEE Access, vol. 13, pp. 153817-153844, 2025, https://doi.org/10.1109/ACCESS.2025.3605165.
R. Haripriya, N. Khare, and M. Pandey, “Privacy-preserving federated learning for collaborative medical data mining in multi-institutional settings,” Scientific Reports, vol. 15, p. 12482, 2025, https://doi.org/10.1038/s41598-025-97565-4.
Y. S. Narule and K. S. Thakre, “Privacy preservation using optimized Federated Learning: A critical survey,” Intelligent Decision Technologies, vol. 18, no. 1, pp. 135-149, 2024, https://doi.org/10.3233/IDT-230104.
S. S. Matta and M. Bolli, “Federated Learning for Privacy-Preserving Healthcare Data Sharing: Enabling Global AI Collaboration,” American Journal of Scholarly Research and Innovation, vol. 04, pp. 320-351, 2025, https://doi.org/10.63125/jga18304.
E. Nowell and S. Gallus, “Advancing Privacy-Preserving AI: A Survey on Federated Learning and Its Applications,” Preprints, 2025, https://doi.org/10.20944/preprints202501.0685.v1.
S. Pati et al., “Privacy Preservation for Federated Learning in Health Care,” Patterns (N Y), vol. 5, no. 7, p. 100974, 2024, https://doi.org/10.1016/j.patter.2024.100974.
F. EL-Husseini, H. N. Noura, and F. Vernier, “Security and privacy-preserving for machine learning models: attacks, countermeasures, and future directions,” Annals of Telecommunications, 2025, https://doi.org/10.1007/s12243-025-01107-y.
R. Haripriya, N. Khare, M. Pandey, and S. Biswas, “Navigating the fusion of federated learning and big data: a systematic review for the AI landscape,” Cluster Comput., vol. 28, no. 1, p. 303, 2025, https://doi.org/10.1007/s10586-024-05070-6.
A. Syaefudin, N. A. Setiawan, and M. N. Rizal, “Blockchain Technology to Maintain Data Integrity: A Systematic Literature Review,” in 2024 International Conference on Smart Computing, IoT and Machine Learning (SIML), 2024, pp. 303-308, https://doi.org/10.1109/SIML61815.2024.10578276.
S. S. Sefati, R. Craciunescu, B. Arasteh, S. Halunga, O. Fratu, and I. Tal, “Cybersecurity in a Scalable Smart City Framework Using Blockchain and Federated Learning for Internet of Things (IoT),” Smart Cities, vol. 7, no. 5, pp. 2802-2841, 2024, https://doi.org/10.3390/smartcities7050109.
H. Alshahrani, N. Islam, D. Syed, A. Sulaiman, M. S. Al Reshan, K. Rajab, A. Shaikh, J. Shuja-Uddin, and A. Soomro, “Sustainability in Blockchain: A Systematic Literature Review on Scalability and Power Consumption Issues,” Energies, vol. 16, no. 3, p. 1510, 2023, https://doi.org/10.3390/en16031510.
M. Hussain, M. Khairul, I. Bhuiyan, S. A. Sumon, S. Akter, M. Hossain, and A. Akther, “Enhancing Data Integrity and Traceability in Industry Cyber Physical Systems (ICPS) through Blockchain Technology: A Comprehensive Approach,” Advances in Artificial Intelligence and Machine Learning, vol. 4, no. 4, p. 2883, 2024, https://doi.org/10.54364/AAIML.2024.44168.
I. S. Rao, M. L. Mat Kiah, M. M. Hameed, and Z. A. Memon, “Scalability of blockchain: a comprehensive review and future research direction,” Cluster Comput, vol. 27, pp. 5547–5570, 2024, https://doi.org/10.1007/s10586-023-04257-7.
B. L. Y. Quan, N. H. A. Wahab, A. Al-Dhaqm, A. Alshammari, A. Aqarni, and S. A. Razak, “Recent Advances in Sharding Techniques for Scalable Blockchain Networks: A Review,” IEEE Access, vol. 13, pp. 21335-21366, 2025, https://doi.org/10.1109/ACCESS.2024.3523256.
H. Lakhlef, T. Lerner, A. Kebir, N. El Atia, X. Du, and V. Ingardin, “Blockchain-Enabled SDN Solutions for IoT: Advancements, Discussions, and Strategic Insights,” in 2024 IEEE Symposium on Computers and Communications (ISCC), pp. 1-6, 2024, https://doi.org/10.1109/ISCC61673.2024.10733649.
E. U. Haque, A. Shah, J. Iqbal, M. Al-Rakhami, A. Al-Qarni, and A. Gumaei, “A scalable blockchain based framework for efficient IoT data management using lightweight consensus,” Scientific Reports, vol. 14, p. 7841, 2024, https://doi.org/10.1038/s41598-024-58578-7.
T. Fernández-Caramés and P. Fraga-Lamas, “A Comprehensive Survey on Green Blockchain: Developing the Next Generation of Energy Efficient and Sustainable Blockchain Systems,” arXiv preprint arXiv:2410.20581, 2024, https://doi.org/10.48550/arXiv.2410.20581.
N. Khan, R. Mir, and M. A. Chishti, “BEFF-SIGS: blockchain-enhanced fog framework- securing IoT data integrity and green sustainability through scalable authentication-authorization,” International Journal of Computers and Applications, vol. 47, pp. 1-19, 2024, https://doi.org/10.1080/1206212X.2024.2380654.
T. A. Alghamdi, R. Khalid, and N. Javaid, “A Survey of Blockchain Based Systems: Scalability Issues and Solutions, Applications and Future Challenges,” IEEE Access, vol. 12, pp. 79626-79651, 2024, https://doi.org/10.1109/ACCESS.2024.3408868.
Z. Chen, X. Chen, and Y. Li, “Performance and Security Analysis of Distributed Ledger Under the Internet of Things Environments With Network Instability,” IEEE Internet of Things Journal, vol. 10, no. 5, pp. 4213-4225, 2023, https://doi.org/10.1109/JIOT.2022.3216586.
T. Siddiqui and S. S. B. Alazzawi, “Comparative Analysis of Internet of Things (IoT) Security Models,” in Advanced Informatics for Computing Research. ICAICR 2020, pp. 177-188, 2021, https://doi.org/10.1007/978-981-16-3653-0_15.
F. Liu, “Generalized Gaussian Mechanism for Differential Privacy,” IEEE Transactions on Knowledge and Data Engineering, vol. 31, no. 4, pp. 747-756, 2019, https://doi.org/10.1109/TKDE.2018.2845388.
L. Zhang, T. Zhu, P. Xiong, W. Zhou, and P. S. Yu, “More than Privacy: Adopting Differential Privacy in Game-theoretic Mechanism Design,” ACM Computing Surveys, vol. 54, no. 7, p. 136, 2022, https://doi.org/10.1145/3460771.
M. A. Husnoo, A. Anwar, R. K. Chakrabortty, R. Doss, and M. J. Ryan, “Differential Privacy for IoT-Enabled Critical Infrastructure: A Comprehensive Survey,” IEEE Access, vol. 9, pp. 153276-153304, 2021, https://doi.org/10.1109/ACCESS.2021.3124309.
N. Phan, X. Wu, H. Hu, and D. Dou, “Adaptive Laplace Mechanism: Differential Privacy Preservation in Deep Learning,” in 2017 IEEE International Conference on Data Mining (ICDM), pp. 385-394, 2017, https://doi.org/10.1109/ICDM.2017.48.
H. Liu, Z. Wu, Y. Zhou, C. Peng, F. Tian, and L. Lu, “Privacy-Preserving Monotonicity of Differential Privacy Mechanisms,” Applied Sciences, vol. 8, no. 11, p. 2081, 2018, https://doi.org/10.3390/app8112081.
N. Holohan, S. Antonatos, S. Braghin, and P. M. Aonghusa, “The Bounded Laplace Mechanism in Differential Privacy,” Journal of Privacy and Confidentiality, vol. 10, no. 1, pp. 1-28, 2019, https://doi.org/10.29012/jpc.715.
A. Sedrati, A. Mezrioui, and A. Ouaddah, “IoT-Gov: A structured framework for internet of things governance,” Computer Networks, vol. 233, p. 109902, 2023, https://doi.org/10.1016/j.comnet.2023.109902.
S. Piasecki, “Expert perspectives on GDPR compliance in the context of smart homes and vulnerable persons,” Information & Communications Technology Law, vol. 32, no. 3, pp. 385-417, 2023, https://doi.org/10.1080/13600834.2023.2231326.
G. Malgieri and J. Niklas, “Vulnerable data subjects,” Computer Law & Security Review, vol. 37, 105415, 2020, https://doi.org/10.1016/j.clsr.2020.105415.
J. Breuer, R. Heyman, and R. van Brakel, “Data protection as privilege — Factors to increase meaning of GDPR in vulnerable groups,” Frontiers in Sustainable Cities, vol. 4, 2022, p. 977623, https://doi.org/10.3389/frsc.2022.977623.
Anupriya and K. D. Singh Chauhan, “Securing informational privacy in India’s IoT governance: Looking through the lens of FASTag,” Journal of Data Protection & Privacy, vol. 7, no. 2, 2025, https://doi.org/10.69554/UBZH7994.
G. Georgiadis and G. Poels, “Establishing a Comprehensive Data Protection Impact Assessment Methodology for Big Data Analytics in Compliance with the General Data Protection Regulation,” Research Square, 2025, https://doi.org/10.21203/rs.3.rs-5821174/v1.
M. Choroszewicz and B. Mäihäniemi, “Developing a Digital Welfare State: Data Protection and the Use of Automated Decision-Making in the Public Sector across Six EU Countries,” Global Perspectives, vol. 1, no. 1, p. 12910, Mar. 2020, https://doi.org/10.1525/gp.2020.12910.
Y.-C. Chen and C.-C. Lin, “The Role of Social Work in the Construction of Smart Cities: Practices and Prospects of Digital Services”, Digital Technol. Res. Appl., vol. 4, no. 2, pp. 109–124, 2025, https://doi.org/10.54963/dtra.v4i2.1301.
B. Mittelstadt, “Ethics of the health-related internet of things: a narrative review,” Ethics and Information Technology, vol. 19, no. 3, pp. 157–175, 2017, https://doi.org/10.1007/s10676-017-9426-4.
F. Reamer, “Artificial Intelligence in Social Work: Emerging Ethical Issues,” International Journal of Social Work Values and Ethics, vol. 20, pp. 52-71, 2023, https://doi.org/10.55521/10-020-205.
A. R. Garcia, “AI, IoT, Big Data, and Technologies in Digital Economy with Blockchain at Sustainable Work Satisfaction to Smart Mankind: Access to 6th Dimension of Human Rights,” in Smart Governance for Cities: Perspectives and Experiences, pp. 85–100, 2020, https://doi.org/10.1007/978-3-030-22070-9_6.
A. Shahraki and Ø. Haugen, “Social ethics in Internet of Things: An outline and review,” in 2018 IEEE Industrial Cyber-Physical Systems (ICPS), pp. 509-516, 2018, https://doi.org/10.1109/ICPHYS.2018.8390757.
R. P. Pradhan, A. K. Sarangi, and A. Sabat, “The effect of ICT development on innovation: evidence from G-20 countries,” Eurasian Econ Rev, vol. 12, pp. 361-371, 2022, https://doi.org/10.1007/s40822-021-00189-y.
H. Bangui, B. Buhnova, and M. Ge, “Social Internet of Things: Ethical AI Principles in Trust Management,” Procedia Computer Science, vol. 220, pp. 553-560, 2023, https://doi.org/10.1016/j.procs.2023.03.070.
S. Tzafestas, “Ethics and Law in the Internet of Things World,” Smart Cities, vol. 1, pp. 98-120, 2018, https://doi.org/10.3390/smartcities1010006.
F. G. Reamer, “Clinical Social Work in a Digital Environment: Ethical and Risk-Management Challenges,” Clinical Social Work Journal, vol. 43, pp. 120–132, 2015, https://doi.org/10.1007/s10615-014-0495-0.
F. G. Reamer, “Social Work in a Digital Age: Ethical and Risk Management Challenges,” Social Work, vol. 58, no. 2, pp. 163–172, 2013, https://doi.org/10.1093/sw/swt003.
A. Rodríguez-Martínez, M. T. Amezcua Aguilar, J. Cortés Moreno, and J. J. Jiménez-Delgado, “Ethical Issues Related to the Use of Technology in Social Work Practice. A Systematic Review,” SAGE Open, vol. 14, no. 3, 2024, https://doi.org/10.1177/21582440241274842.
A. M. L. Taylor-Beswick, “Digitalizing social work education: preparing students to engage with twenty-first century practice need,” Social Work Education, vol. 42, no. 1, pp. 44-64, 2023, https://doi.org/10.1080/02615479.2022.2049225.
E. Beaumont, P. Chester, and H. Rideout, “Navigating Ethical Challenges in Social Media: Social Work Student and Practitioner Perspectives,” Australian Social Work, vol. 70, no. 2, pp. 221–228, 2017, https://doi.org/10.1080/0312407X.2016.1274416.
F. Körner, “Current challenges of implementing ETSI EN 303 645 as a baseline security standard for consumer IoT security certification,” TechRxiv, 2023, https://doi.org/10.36227/techrxiv.24711672.
N. U. Prince, M. A. A. Mamun, A. Olajide, O. Khan, A. Akeem, and A. Sani, “IEEE Standards and Deep Learning Techniques for Securing Internet of Things (IoT) Devices Against Cyber Attacks”, Journal of Computational Analysis and Applications (JoCAAA), vol. 33, no. 07, pp. 1270–1289, 2024, https://eudoxuspress.com/index.php/pub/article/view/1210.
O. K. Greuter and D. K. Sarmah, “The Baseline of Global Consumer Cyber Security Standards for IoT: Quality Evaluation,” Journal of Cyber Security Technology, vol. 6, no. 4, pp. 175–200, 2022, https://doi.org/10.1080/23742917.2022.2105192.
F. Casarosa, “Cybersecurity of Internet of Things in the health sector: Understanding the applicable legal framework,” Computer Law & Security Review, vol. 53, 105982, 2024, https://doi.org/10.1016/j.clsr.2024.105982.
R. Kaksonen, K. Halunen, M. Laakso, and J. Röning, “Automating IoT Security Standard Testing by Common Security Tools,” in Proceedings of the 9th International Conference on Information Systems Security and Privacy, ICISSP, pp. 42-53, 2024, https://doi.org/10.5220/0012345900003648.
B. Sereda and J. Jaskolka, “An Evaluation of IoT Security Guidance Documents: A Shared Responsibility Perspective,” Procedia Computer Science, vol. 201, pp. 281-288, 2022, https://doi.org/10.1016/j.procs.2022.03.038.
E. M. Kalogeraki and N. Polemi, “A taxonomy for cybersecurity standards,” Journal of Surveillance, Security and Safety, vol. 5, pp. 95-115, 2024, https://doi.org/10.20517/jsss.2023.50.
H. Sebestyen, D. E. Popescu, and R. D. Zmaranda, “A Literature Review on Security in the Internet of Things: Identifying and Analysing Critical Categories,” Computers, vol. 14, no. 2, p. 61, 2025, https://doi.org/10.3390/computers14020061.
K. Bližnák, M. Munk, and A. Pilková, “A Systematic Review of Recent Literature on Data Governance (2017–2023),” IEEE Access, vol. 12, pp. 149875-149888, 2024, https://doi.org/10.1109/ACCESS.2024.3476373.
M. R. C. Santos and R. M. S. Laureano, “Developing a Vulnerability-Based Conceptual Model for Managing Risk in Non-Profit Projects: A Multicase Study in a European Country,” Public Management Review, vol. 25, no. 2, pp. 313-339, 2021, https://doi.org/10.1080/14719037.2021.1972685.
C. Oko-Odion and A. Omogbeme, “Risk management frameworks for financial institutions in a rapidly changing economic landscape,” International Journal of Science and Research Archive, vol. 14, no. 01, pp. 1182–1204, 2025, https://doi.org/10.30574/ijsra.2025.14.1.0155.
L. Dominelli, Social work practice during times of disaster: A transformative green social work model for theory, education and practice in disaster interventions. Routledge. 2023, https://doi.org/10.4324/9781003105824.
R. Napitupulu, R. Sukmana, and A. Rusydiana, “Governance of Islamic social finance: learnings from existing literature,” International Journal of Islamic and Middle Eastern Finance and Management, vol. 17, pp. 523-541, 2024, https://doi.org/10.1108/IMEFM-06-2023-0222.
T. Sim, M. He, and L. Dominelli, “Social Work Core Competencies in Disaster Management Practice: An Integrative Review,” Research on Social Work Practice, vol. 32, no. 3, pp. 310-321, 2022, https://doi.org/10.1177/10497315211055427.
P.-J. Schweizer and S. Juhola, “Navigating systemic risks: governance of and for systemic risks,” Global Sustainability, vol. 7, p. e38, 2024, https://doi.org/10.1017/sus.2024.30.
L. Brown and S. P. Osborne, “Risk and Innovation: Towards a framework for risk governance in public services,” Public Management Review, vol. 15, no. 2, pp. 186–208, 2012, https://doi.org/10.1080/14719037.2012.707681.
A. Brown, D. Harkin, and L. M. Tanczer, “Safeguarding the “Internet of Things” for Victim-Survivors of Domestic and Family Violence: Anticipating Exploitative Use and Encouraging Safety-by-Design,” Violence Against Women, vol. 31, no. 5, pp. 1039-1062, 2024, https://doi.org/10.1177/10778012231222486.
E. Giorgi, “How Technology Devices Can Help or Harm Vulnerable Communities in Technocene. Issues for Designers, Architects, and Policy Makers,” in Design for Vulnerable Communities. The Urban Book Series, pp. 15-28, 2022, https://doi.org/10.1007/978-3-030-96866-3_2.
G. Kołaczek, “Internet of Things (IoT) Technologies in Cybersecurity: Challenges and Opportunities,” Applied Sciences, vol. 15, no. 6, p. 2935, 2025, https://doi.org/10.3390/app15062935.
B. Friedman and D. G. Hendry, Value Sensitive Design: Shaping Technology with Moral Imagination. The MIT Press, 2019, https://doi.org/10.7551/mitpress/7585.001.0001.
J. Bae, S. Lee, and C. J. W. Choi, “Expansion of Digital Technology Use in the Korean Social Work Field,” Journal of Social Service Research, vol. 51, no. 3, pp. 663–677, 2024, https://doi.org/10.1080/01488376.2024.2402520.
J. A. Osian-Gabrie, “The impact of digital disruption on social inequality: Challenges and opportunities for social work practice”, AJBMR, vol. 11, no. 2, pp. 45–49, Dec. 2024.
Y. Liu, A. Sharma, S. Rani, and J. Yang, “Supply Chain Security, Resilience and Agility in IoT-driven Healthcare,” IEEE Internet of Things Journal, https://doi.org/10.1109/JIOT.2025.3545962.
Published
How to Cite
Issue
Section
License
Copyright (c) 2025 Yih-Chang Chen, Chia-Ching Lin

This work is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License.
Authors who publish with this journal agree to the following terms:
- Authors retain copyright and grant the journal right of first publication with the work simultaneously licensed under a Creative Commons Attribution License that allows others to share the work with an acknowledgment of the work's authorship and initial publication in this journal.
- Authors are able to enter into separate, additional contractual arrangements for the non-exclusive distribution of the journal's published version of the work (e.g., post it to an institutional repository or publish it in a book), with an acknowledgment of its initial publication in this journal.
- Authors are permitted and encouraged to post their work online (e.g., in institutional repositories or on their website) prior to and during the submission process, as it can lead to productive exchanges, as well as earlier and greater citation of published work (See The Effect of Open Access).
This journal is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License.


