Embedded response technology and service cloud platform for vehicle information tracking
DOI:
https://doi.org/10.12928/ijio.v4i1.6928Keywords:
Cloud, Criminal, Vehicle, QRcode, GovernmentAbstract
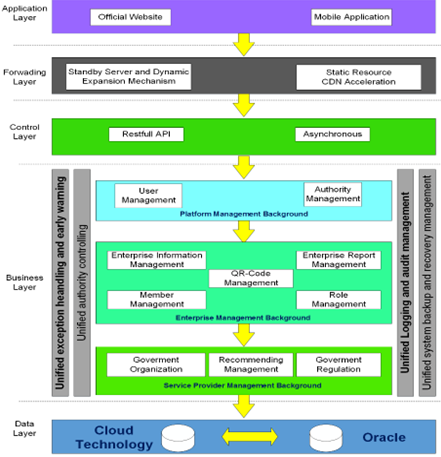
Based on the Indonesia national police crime database, it is reported that vehicle theft cases have increased during the Covid-19 pandemic. The database reported an increasing trend of vehicle theft, 4,065 cases from January 2019 to January 2020 in the province and regency region. Therefore, to help police officers work and minimize the criminal cases of vehicle theft, an effective strategy is needed to reduce these threats. This study proposes implementing SMS and QRcode technology embedded in the vehicle for validation information. Cloud computing capabilities can offer real-time network access to technology resources that can be physically located anywhere geographically based on business needs. This technology can rapidly search and show detailed information regarding the specific vehicle, including the vehicle owner, the vehicle registration number, and the validation of the driver's license. To implement and examine the effectiveness of the proposed technology, this study was conducted an experimental study in a real-world setting from January 2021 until April 2021 in Makassar city, Indonesia. This study concluded that the proposed technology could successfully be implemented and effectively show detailed information regarding the specific vehicle based on the experimental results. This study concluded the potential use of the proposed technology in the real world as an alternative solution to minimize the criminal cases of vehicle theft. It can be used as an alternative solution to reduce the increase in criminal cases of inter-island private vehicle theft syndicates.
References
F. Martinelli, F. Mercaldo, A. Orlando, V. Nardone, A. Santone, and A. K. Sangaiah, “Human behavior characterization for driving style recognition in vehicle system,” Comput. Electr. Eng., vol. 83, 2020, doi: 10.1016/j.compeleceng.2017.12.050.
M. A. M’hand, A. Boulmakoul, H. Badir, and A. Lbath, “A scalable real-time tracking and monitoring architecture for logistics and transport in RoRo terminals,” Procedia Comput. Sci., vol. 151, pp. 218–225, 2019, doi: 10.1016/j.procs.2019.04.032.
Q. Al-Maatouk, M. S. Bin Othman, M. E. Rana, and W. M. Al-Rahmi, “A cloud based framework for e-government implementation in developing countries,” Int. J. Eng. Technol., vol. 7, no. 4, pp. 3018–3021, 2018, doi: 10.14419/ijet.v7i4.14740.
T. Yuan, Y. Wang, K. Xu, R. R. Martin, and S.-M. Hu, “Two-Layer QR Codes,” IEEE Trans. Image Process., vol. 28, no. 9, pp. 4413–4428, Sep. 2019, doi: 10.1109/TIP.2019.2908490.
I. Tkachenko, W. Puech, C. Destruel, O. Strauss, J.-M. Gaudin, and C. Guichard, “Two-Level QR Code for Private Message Sharing and Document Authentication,” IEEE Trans. Inf. Forensics Secur., vol. 11, no. 3, pp. 571–583, Mar. 2016, doi: 10.1109/TIFS.2015.2506546.
S. C. Chen, S. H. Li, S. C. Liu, D. C. Yen, and A. Ruangkanjanases, “Assessing determinants of continuance intention towards personal cloud services: Extending utaut2 with technology readiness,” Symmetry (Basel)., vol. 13, no. 3, 2021, doi: 10.3390/sym13030467.
M. Bousselham, N. Benamar, and A. Addaim, “A new Security Mechanism for Vehicular Cloud Computing Using Fog Computing System,” 2019 Int. Conf. Wirel. Technol. Embed. Intell. Syst. WITS 2019, 2019, doi: 10.1109/WITS.2019.8723723.
R. R. Kanchi, D. Palle, and V. P. Sreeramula, “Design and Development of IoT-Cloud-based Lightning/Storm Detection System with an SMS Alert on Android Mobile,” in 2018 International Conference on Recent Innovations in Electrical, Electronics & Communication Engineering (ICRIEECE), Jul. 2018, pp. 2301–2305, doi: 10.1109/ICRIEECE44171.2018.9008617.
N. Datta, A. Malik, M. Agarwal, and A. Jhunjhunwala, “Real Time Tracking and Alert System for Laptop through Implementation of GPS, GSM, Motion Sensor and Cloud Services for Antitheft Purposes,” Proc. - 2019 4th Int. Conf. Internet Things Smart Innov. Usages, IoT-SIU 2019, 2019, doi: 10.1109/IoT-SIU.2019.8777477.
L. Gao, F. Li, X. Xu, and Y. Liu, “Intrusion detection system using SOEKS and deep learning for in-vehicle security,” Cluster Comput., vol. 22, no. S6, pp. 14721–14729, Nov. 2019, doi: 10.1007/s10586-018-2385-7.
G. Mithil Suhas, A. Venkata Jaswanth, C. Sai Bharath, and C. V. Ravi Kumar, “IoT based smart transport system uisng fingerprint,” Int. J. Electr. Eng. Technol., vol. 11, no. 3, pp. 203–209, Jun. 2020.
A. S. Ali, A. H. Hasan, and H. A. Lafta, “Antitheft vehicle tracking and control system based iot,” J. Crit. Rev., vol. 7, no. 9, pp. 88–92, 2020, doi: 10.31838/jcr.07.09.16.
V. Akila, K. Sriharshini, P. Sravani, D. Sravanthi, R. Gopi, and T. Sheela, “Intelligent Car Anti-Theft Face Recognition System,” Int. J. online Biomed. Eng., vol. 17, no. 1, pp. 120–128, 2021, doi: 10.3991/ijoe.v17i01.18583.
M. Faisal, Rahman, F. Shabir, and Ida, “Design and Implementation of Plantation Commodities Price Information Broadcaster via Autoreply Short Message Service on Smartphone,” Proc. - 2nd East Indones. Conf. Comput. Inf. Technol. Internet Things Ind. EIConCIT 2018, pp. 212–217, 2018, doi: 10.1109/EIConCIT.2018.8878575.
L. Kamelia, E. A. Zaki Hamidi, and A. Jazuli Baskara, “E-Key Prototype Implementation Based on Short Message Service (SMS) Technology,” in 2018 12th International Conference on Telecommunication Systems, Services, and Applications (TSSA), Oct. 2018, pp. 1–4, doi: 10.1109/TSSA.2018.8708768.
Savita, S. Shrivastava, A. Arora, and V. Varshney, “Overvoltage and Undervoltage Protection of Load using GSM modem SMS Alert,” in 2018 2nd IEEE International Conference on Power Electronics, Intelligent Control and Energy Systems (ICPEICES), Oct. 2018, pp. 249–252, doi: 10.1109/ICPEICES.2018.8897428.
B. Reaves et al., “Characterizing the security of the SMS ecosystem with public gateways,” ACM Trans. Priv. Secur., vol. 22, no. 1, 2018, doi: 10.1145/3268932.
B. Reaves, N. Scaife, D. Tian, L. Blue, P. Traynor, and K. R. B. Butler, “Sending Out an SMS: Characterizing the Security of the SMS Ecosystem with Public Gateways,” Proc. - 2016 IEEE Symp. Secur. Privacy, SP 2016, pp. 339–356, 2016, doi: 10.1109/SP.2016.28.
J. W. Betz, “The Navstar Global Positioning System,” in Position, Navigation, and Timing Technologies in the 21st Century, Wiley, 2020, pp. 65–85.
R. Kitchen and N. Thrift, “International Encyclopedia of Human Geography (2009),” Choice Rev. Online, vol. 48, no. 01, pp. 48-0052-48–0052, Sep. 2010, doi: 10.5860/CHOICE.48-0052.
B. A. Adaramola, A. O. Salau, F. O. Adetunji, O. G. Fadodun, and A. T. Ogundipe, “Development and Performance Analysis of a GPS-GSM Guided System for Vehicle Tracking,” Proc. Int. Conf. Comput. Autom. Knowl. Manag. ICCAKM 2020, pp. 286–290, 2020, doi: 10.1109/ICCAKM46823.2020.9051533.
A. N. Jafaar and B. M. Nema, “Geolocation android mobile phones using GSM/UMTS,” Baghdad Sci. J., vol. 16, no. 1, pp. 254–262, 2019, doi: 10.21123/bsj.2019.16.1(Suppl.).0254.
A. M. Luthfi, N. Karna, and R. Mayasari, “Google Maps API Implementation On IOT Platform For Tracking an Object Using GPS,” in 2019 IEEE Asia Pacific Conference on Wireless and Mobile (APWiMob), Nov. 2019, pp. 126–131, doi: 10.1109/APWiMob48441.2019.8964139.
J. Ribeiro, T. Fontes, C. Soares, and J. L. Borges, “Process discovery on geolocation data,” Transp. Res. Procedia, vol. 47, pp. 139–146, 2020, doi: 10.1016/j.trpro.2020.03.086.
S. Z. Khan, M. Mohsin, and W. Iqbal, “On GPS Spoofing of Aerial Platforms: A Review of Threats, Challenges, Methodologies, and Future Research Directions,” PeerJ Comput. Sci., vol. 7, pp. 1–35, 2021, doi: 10.7717/PEERJ-CS.507.
L. Sun, J. Ma, H. Wang, Y. Zhang, and J. Yong, “Cloud Service Description Model: An Extension of USDL for Cloud Services,” IEEE Trans. Serv. Comput., vol. 11, no. 2, pp. 354–368, 2018, doi: 10.1109/TSC.2015.2474386.
J. Huang, Q. Duan, S. Guo, Y. Yan, and S. Yu, “Converged Network-Cloud Service Composition with End-to-End Performance Guarantee,” IEEE Trans. Cloud Comput., vol. 6, no. 2, pp. 545–557, 2018, doi: 10.1109/TCC.2015.2491939.
S. Wang, A. Zhou, F. Yang, and R. N. Chang, “Towards Network-Aware Service Composition in the Cloud,” IEEE Trans. Cloud Comput., vol. 8, no. 4, pp. 1122–1134, 2020, doi: 10.1109/TCC.2016.2603504.
J. Brier and lia dwi jayanti, “Vehicle Anti-Theft Tracking System Based on Internet of Thing(IoT),” vol. 21, no. 1, pp. 1–9, 2020, doi: 10.51201/JUSST/21/0514.
A. T. Apasiba, J. B. Hayfron-Acquah, J. K. Panford, and M. Asante, “Enhancing the Security of Vehicles and the Work of the DVLA Using GSM/SMS Technologies,” Int. J. Sci. Eng. Appl., vol. 4, no. 5, pp. 261–268, Sep. 2015, doi: 10.7753/IJSEA0405.1006.
Y. Mao, S. Dai, J. Ding, W. Zhu, C. Wang, and X. Ye, “Space–Time Analysis of Vehicle Theft Patterns in Shanghai, China,” ISPRS Int. J. Geo-Information, vol. 7, no. 9, p. 357, Aug. 2018, doi: 10.3390/ijgi7090357.
M. J. Nelson and R. N. Keswani, “Inadequate colonoscopy preparation: Is it time to send out an SMS?,” Gastrointest. Endosc., vol. 89, no. 3, pp. 514–517, Mar. 2019, doi: 10.1016/j.gie.2018.10.007.
Downloads
Published
How to Cite
Issue
Section
License
Copyright (c) 2023 Muhammad Faisal, Ida Ida, Darniati Darniati, Irmawati Irmawati, Muh Khayyir

This work is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License.
License and Copyright Agreement
In submitting the manuscript to the journal, the authors certify that:
- They are authorized by their co-authors to enter into these arrangements.
- The work described has not been formally published before, except in the form of an abstract or as part of a published lecture, review, thesis, or overlay journal. Please also carefully read the International Journal of Industrial Optimization (IJIO) Author Guidelines at http://journal2.uad.ac.id/index.php/ijio/about/submissions#onlineSubmissions
- That it is not under consideration for publication elsewhere,
- That its publication has been approved by all the author(s) and by the responsible authorities tacitly or explicitly of the institutes where the work has been carried out.
- They secure the right to reproduce any material that has already been published or copyrighted elsewhere.
- They agree to the following license and copyright agreement.
Copyright
Authors who publish with the International Journal of Industrial Optimization (IJIO) agree to the following terms:
- Authors retain copyright and grant the journal right of first publication with the work simultaneously licensed under a Creative Commons Attribution License (CC BY-SA 4.0) that allows others to share the work with an acknowledgment of the work's authorship and initial publication in this journal.
- Authors are able to enter into separate, additional contractual arrangements for the non-exclusive distribution of the journal's published version of the work (e.g., post it to an institutional repository or publish it in a book), with an acknowledgment of its initial publication in this journal.
- Authors are permitted and encouraged to post their work online (e.g., in institutional repositories or on their website) prior to and during the submission process, as it can lead to productive exchanges, as well as earlier and greater citation of published work.

1.png)

