Vulnerability Analysis and Prevention on Software as a Service (SaaS) of Archive Websites
DOI:
https://doi.org/10.12928/biste.v5i3.7719Keywords:
Cyber Security, Penetration Testing, Software as a Service, Vulnerability Assessment, Archive WebsiteAbstract
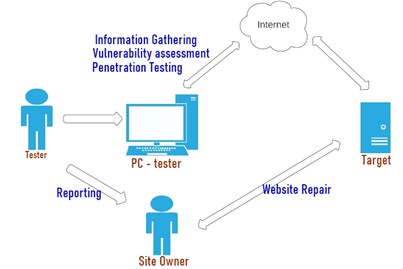
Web Archive is a SaaS service that has an important role in providing better document storage and management. Good document management has a positive impact on optimizing business operations, increasing collaboration, reducing costs, and protecting sensitive information. Cybercrime, which has an increasingly high intensity, is a serious threat to the security of data stored in web archives. This research aims to improve data security on web archives by conducting ongoing testing. Testing was carried out on a server with a Linux operating system and web archives managed by a file manager system. This study tests the attack using the OWASP application method, and an XSS attack on a web archive with a Linux server and using a file management application. The testing phase includes Information Gathering, Vulnerability Assessment, Exploiting, and Reporting. Based on the results of the research, it was obtained that the first vulnerability test contained 9 vulnerabilities in 9 categories. The second vulnerability test obtained 7 vulnerabilities and the third test found no vulnerabilities. At the end of each test, recommendations for improvements to the web archive are made to the web archive manager and a re-testing process for vulnerabilities is carried out. This process is carried out repeatedly with continuous improvement. Testing the attack and repair of the web archive was carried out repeatedly and managed to get a vulnerability level of Level 0.1-3.9 points with Low status.
References
S. Aheleroff, N. Mostashiri, X. Xu, and R. Y. Zhong, “Mass personalisation as a service in industry 4.0: A resilient response case study,” Advanced Engineering Informatics, vol. 50, p. 101438, 2021, https://doi.org/10.1016/j.aei.2021.101438.
N. Bruno and R. Roncella, “HBIM for conservation: A new proposal for information modeling,” Remote Sensing, vol. 11, no. 15, p. 1751, 2019, https://doi.org/10.3390/rs11151751.
V. K. Malviya, S. Rai, and A. Gupta, “Development of web browser prototype with embedded classification capability for mitigating Cross-Site Scripting attacks,” Applied Soft Computing, vol. 102, p. 106873, 2021, https://doi.org/10.1016/j.asoc.2020.106873.
S. Kumar, P. Tiwari, and M. Zymbler, “Internet of Things is a revolutionary approach for future technology enhancement: a review,” Journal of Big data, vol. 6, no. 1, pp. 1-21, 2019, https://doi.org/10.1186/s40537-019-0268-2.
A. Ghasempour, “Internet of things in smart grid: Architecture, applications, services, key technologies, and challenges,” Inventions, vol. 4, no. 1, p. 22, 2019, https://doi.org/10.3390/inventions4010022.
R. Huang, A. Tlili, T. W. Chang, X. Zhang, F. Nascimbeni, and D. Burgos, “Disrupted classes, undisrupted learning during COVID-19 outbreak in China: application of open educational practices and resources,” Smart Learning Environments, vol. 7, pp. 1-15, 2020, https://doi.org/10.1186/s40561-020-00125-8.
M. Agreindra Helmiawan, E. Firmansyah, I. Fadil, Y. Sofivan, F. Mahardika, and A. Guntara, "Analysis of Web Security Using Open Web Application Security Project 10," 2020 8th International Conference on Cyber and IT Service Management (CITSM), pp. 1-5, 2020, https://doi.org/10.1109/CITSM50537.2020.9268856.
M. Singh, P. Singh, and P. Kumar, "An Analytical Study on Cross-Site Scripting," 2020 International Conference on Computer Science, Engineering and Applications (ICCSEA), pp. 1-6, 2020, https://doi.org/10.1109/ICCSEA49143.2020.9132894.
A. A. R. Farea, C. Wang, E. Farea, and A. Ba Alawi, "Cross-Site Scripting (XSS) and SQL Injection Attacks Multi-classification Using Bidirectional LSTM Recurrent Neural Network," 2021 IEEE International Conference on Progress in Informatics and Computing (PIC), pp. 358-363, 2021, https://doi.org/10.1109/PIC53636.2021.9687064.
F. A. Mereani and J. M. Howe, “Detecting cross-site scripting attacks using machine learning,” In International conference on advanced machine learning technologies and applications, pp. 200-210, 2018, https://doi.org/10.1007/978-3-319-74690-6_20.
G. E. Rodríguez, J. G. Torres, P. Flores, and D. E. Benavides, “Cross-site scripting (XSS) attacks and mitigation: A survey,” Computer Networks, vol. 166, p. 106960, 2020, https://doi.org/10.1016/j.comnet.2019.106960.
D. Korać, B. Damjanović, D. Simić, and K. K. R. Choo, “A hybrid XSS attack (HYXSSA) based on fusion approach: Challenges, threats and implications in cybersecurity,” Journal of King Saud University-Computer and Information Sciences, vol. 34, no. 10, pp. 9284-9300, 2022, https://doi.org/10.1016/j.jksuci.2022.09.008.
S. Siboni et al., "Security Testbed for Internet-of-Things Devices," in IEEE Transactions on Reliability, vol. 68, no. 1, pp. 23-44, 2019, https://doi.org/10.1109/TR.2018.2864536.
A. Arora, P. M. Furlong, R. Fitch, S. Sukkarieh, and T. Fong, “Multi-modal active perception for information gathering in science missions,” Autonomous Robots, vol. 43, pp. 1827-1853, 2019, https://doi.org/10.1007/s10514-019-09836-5.
Y. Cheng, Y. Liu, G. Piao, Z. Zhang, N. Li, and M. Qiu, "Disclosing Features and Characteristics of. COM Registrars' WHOIS Servers," 2022 2nd Asia-Pacific Conference on Communications Technology and Computer Science (ACCTCS), pp. 52-56, 2022, https://doi.org/10.1109/ACCTCS53867.2022.00018.
W. Zhang, J. Chen, Y. Kuo, and Y. Zhou, "Transmit Beamforming for Layered Physical Layer Security," in IEEE Transactions on Vehicular Technology, vol. 68, no. 10, pp. 9747-9760, 2019, https://doi.org/10.1109/TVT.2019.2932753.
P. Ranade, A. Piplai, S. Mittal, A. Joshi, and T. Finin, "Generating Fake Cyber Threat Intelligence Using Transformer-Based Models," 2021 International Joint Conference on Neural Networks (IJCNN), pp. 1-9, 2021, https://doi.org/10.1109/IJCNN52387.2021.9534192.
B. A. Mozzaquatro, C. Agostinho, D. Goncalves, J. Martins, and R. Jardim-Goncalves, “An ontology-based cybersecurity framework for the internet of things,” Sensors, vol. 18, no, 9, p. 3053, 2018, https://doi.org/10.3390/s18093053.
G. J. Blinowski and P. Piotrowski, “CVE based classification of vulnerable IoT systems,” In Theory and Applications of Dependable Computer Systems: Proceedings of the Fifteenth International Conference on Dependability of Computer Systems DepCoS-RELCOMEX, June 29–July 3, 2020, Brunów, Poland 15, pp. 82-93, 2020, https://doi.org/10.1007/978-3-030-48256-5_9.
S. S. Malladi and H. C. Subramanian, "Bug Bounty Programs for Cybersecurity: Practices, Issues, and Recommendations," in IEEE Software, vol. 37, no. 1, pp. 31-39, 2020, https://doi.org/10.1109/MS.2018.2880508.
Published
How to Cite
Issue
Section
License
Copyright (c) 2023 Mushlihudin Mushlihudin, Danis Faisal

This work is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License.
Authors who publish with this journal agree to the following terms:
- Authors retain copyright and grant the journal right of first publication with the work simultaneously licensed under a Creative Commons Attribution License that allows others to share the work with an acknowledgment of the work's authorship and initial publication in this journal.
- Authors are able to enter into separate, additional contractual arrangements for the non-exclusive distribution of the journal's published version of the work (e.g., post it to an institutional repository or publish it in a book), with an acknowledgment of its initial publication in this journal.
- Authors are permitted and encouraged to post their work online (e.g., in institutional repositories or on their website) prior to and during the submission process, as it can lead to productive exchanges, as well as earlier and greater citation of published work (See The Effect of Open Access).
This journal is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License.


