GandCrab Ransomware Analysis on Windows Using Static Method
DOI:
https://doi.org/10.12928/biste.v3i2.4884Keywords:
GandCrab, Malware, Ransomware, Analisis StatisAbstract
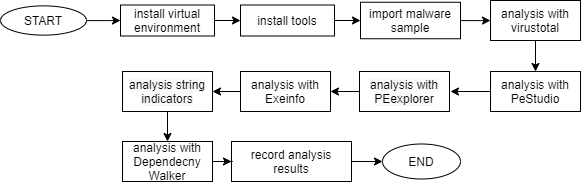
Malware-infected operating systems may experience system damage, files or loss of important data. Ransomware is a type of malware that works by attacking the internet network and then encrypting the victim's computer. So that the victim can access his computer again, the victim is asked to redeem (ransom) with some money in the form of Bitcoin. One of them is GandCrab. Gandcrab is a very powerful ransomware and only the creators of Gandcrab know the description of the encrypted files.Static analysis is done by importing malware samples into Virustotal, Dependency walker, PEStudio, Exeinfo PE, and PEexplorer tools to get the strings function, which will then be analyzed to find out how the GandCrab Ransomware works.This study analyzes the gandcrab ransomware malware using a static method. In the Virustotal tool, it was found that the malware sample file was detected as malware with a ratio of 60 out of 70 antimalware. Furthermore, it was found that GandCrab is in PE (portable executable) format, compiled using Microsoft Visual C++ and GndCrab accesses some DLL (dynamic link-library) functions.
Sistem operasi yang terinfeksi malware dapat mengalami kerusakan sistem, file atau kehilangan data-data penting. Ransomware merupakan salah satu jenis malware yang bekerja dengan cara menyerang jaringan internet kemudian mengenkripsi komputer korban. Agar korban dapat mengakses komputernya lagi, korban diminta unutk menebus (ransom) dengan sejumlah uang dalam bentuk Bitcoin. Salah satunya yaitu GandCrab. Gandcrab merupakan ransomware yang sangat kuat dan hanya pembuat gandcrab yang mengetahui deskripsi dari file yang terenkripsi. Analisis statis dilakukan dengan mengimpor sample malware kedalam tools Virustotal, Dependency walker, PEStudio, Exeinfo PE, dan PEexplorer untuk mendapatkan fungsi strings yang kemudian strings tersebut akan dianalisa untuk mengetahui cara kerja dari GandCrab Ransomware. Penelitian ini melakukan analisis terhadap malware gandcrab ransomware dengan menggunakan metode statis. Pada tool Virustotal, didapatkan bahwa file sample malware terdeteksi sebagai malware dengan rasio 60 dari 70 antimalware. Selanjutnya ditemukan bahwa GandCrab berformat PE (portable executable), dikompilasi menggunakan Microsoft Visual C++ dan GandCrab mengakses beberapa fungsi DLL (dynamic link-library).
References
I. Hariman and A. Syams, “Analisis Malware Dengan Teknik Static Analysis,” 2015.
Chebyshev Victor, “IT threat evolution Q3 2020 Mobile statistics | Securelist.” 2020, [Online]. Available: https://securelist.com/it-threat-evolution-q3-2020-mobile-statistics/99461
S. C. Hsiao and D. Y. Kao, “The static analysis of WannaCry ransomware,” Int. Conf. Adv. Commun. Technol. ICACT, vol. 2018-Febru, pp. 153–158, 2018. https://doi.org/10.23919/ICACT.2018.8323680
S. Usharani, P. Manju Bala, and M. Martina Jose Mary, “Dynamic Analysis on Crypto-ransomware by using Machine Learning: GandCrab Ransomware,” J. Phys. Conf. Ser., vol. 1717, p. 012024, 2021. https://doi.org/10.1088/1742-6596/1717/1/012024
S. Talukder and Z. Talukder, “A Survey on Malware Detection and Analysis Tools,” Int. J. Netw. Secur. Its Appl., vol. 12, no. 2, pp. 37–57, 2020. https://doi.org/10.5121/ijnsa.2020.12203
Malwarebytes, “GandCrab Ransomware - Removal and Prevention Guide | Malwarebytes.” 2019, [Online]. Available: https://www.malwarebytes.com/gandcrab
S. Gadhiya, K. Bhavsar, and P. D. Student, “Techniques for Malware Analysis,” Int. J. Adv. Res. Comput. Sci. Softw. Eng., vol. 3, no. 4, pp. 2277–128, 2013.
D. Uppal, V. Mehra, and V. Verma, “Basic survey on Malware Analysis, Tools and Techniques,” Int. J. Comput. Sci. Appl., vol. 4, no. 1, pp. 103–112, 2014. https://doi.org/10.5121/ijcsa.2014.4110
P. Nunes, I. Medeiros, J. C. Fonseca, N. Neves, M. Correia, and M. Vieira, “Benchmarking Static Analysis Tools for Web Security,” IEEE Trans. Reliab., vol. 67, no. 3, pp. 1159–1175, 2018. https://doi.org/10.1109/TR.2018.2839339
A. Braga, R. Dahab, N. Antunes, N. Laranjeiro, and M. Vieira, “Understanding How to Use Static Analysis Tools for Detecting Cryptography Misuse in Software,” IEEE Trans. Reliab., vol. 68, no. 4, pp. 1384–1403, 2019. https://doi.org/10.1109/TR.2019.2937214
Downloads
Published
How to Cite
Issue
Section
License
Copyright (c) 2021 Anisa Oktaviani

This work is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License.
Authors who publish with this journal agree to the following terms:
- Authors retain copyright and grant the journal right of first publication with the work simultaneously licensed under a Creative Commons Attribution License that allows others to share the work with an acknowledgment of the work's authorship and initial publication in this journal.
- Authors are able to enter into separate, additional contractual arrangements for the non-exclusive distribution of the journal's published version of the work (e.g., post it to an institutional repository or publish it in a book), with an acknowledgment of its initial publication in this journal.
- Authors are permitted and encouraged to post their work online (e.g., in institutional repositories or on their website) prior to and during the submission process, as it can lead to productive exchanges, as well as earlier and greater citation of published work (See The Effect of Open Access).
This journal is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License.


