Social Media Metadata Forensic Ontology Model
DOI:
https://doi.org/10.12928/mf.v5i2.8937Keywords:
Ontology, RDF, OWL, Social Media, Digital Forensics, SmartphoneAbstract
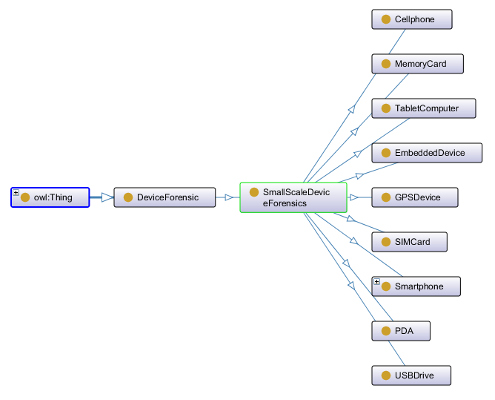
The escalating use of compact electronic gadgets like smartphones and smartwatches, along with social media platforms, has led to a new dimension of criminal activities. Advancements in digital forensics, which investigates digital evidence, have become noteworthy. Researchers David Christopher Harrill and Richard P. Mislan devised Small-Scale Digital Device Forensics (SSDDF) for examining miniature digital devices used in criminal undertakings. Edlira Kalemi and Sule Yildirim-Yayilgan demonstrated the application of ontology in social media forensics, deciphering Android system frameworks related to social media data extraction. However, their investigations mainly focused on social media, overlooking the role of gadgets used by criminals and victims. Extracting digital data from these devices remains pivotal for securing relevant evidence from social media. Notwithstanding, incorporating SSDDF and understanding Android system structures have significantly contributed to digital forensic methodologies. These enhancements can bolster the investigation process, capturing and analyzing critical digital evidence from compact electronic appliances and social media platforms. The advent of SSDDF and elucidating Android system structures have offered invaluable inputs to digital forensics, enhancing efficacy in amassing significant evidence from small electronic devices and social media platforms.
References
We Are Social, “Digital 2022: Indonesia - DataReportal - Global Digital Insights,” DateReportal, 2022. https://datareportal.com/reports/digital-2022-indonesia (accessed Sep. 15, 2022).
P. Qurrota Ayun, “Fenomena Remaja Menggunakan Media Sosial dalam Membentuk Identitas,” CHANNEL Jurnal Komunikasi, vol. 3, no. 2, pp. 1–16, Oct. 2015, doi: 10.12928/channel.v3i2.3270.
Mulawarman and A. D. Nurfitri, “Perilaku Pengguna Media Sosial beserta Implikasinya Ditinjau dari Perspektif Psikologi Sosial Terapan,” Buletin Psikologi, vol. 25, no. 1, pp. 36–44, Jun. 2017, doi: 10.22146/buletinpsikologi.22759.
A. Sagiyanto and N. Ardiyanti, “SELF DISCLOSURE MELALUI MEDIA SOSIAL INSTAGRAM (Studi Kasus Pada Anggota Galeri Quote),” Nyimak (Journal of Communication), vol. 2, no. 1, pp. 81–94, Aug. 2018, doi: 10.31000/nyimak.v2i1.687.
R. Aditia, “Fenomena Phubbing: Suatu Degradasi Relasi Sosial Sebagai Dampak Media Sosial,” KELUWIH: Jurnal Sosial dan Humaniora, vol. 2, no. 1, pp. 8–14, Apr. 2021, doi: 10.24123/soshum.v2i1.4034.
Y. N. Bulele and T. Wibowo, “ANALISIS FENOMENA SOSIAL MEDIA DAN KAUM MILENIAL: STUDI KASUS TIKTOK,” Conference on Business, Social Sciences and Innovation Technology, vol. 1, no. 1, pp. 565–572, 2020, [Online]. Available: http://journal.uib.ac.id/index.php/cbssit
M. Rifauddin, “Fenomena Cyberbullying pada Remaja,” Khizanah al-Hikmah : Jurnal Ilmu Perpustakaan, Informasi, dan Kearsipan, vol. 4, no. 1, pp. 35–44, Jun. 2016, doi: 10.24252/kah.v4i1a3.
R. Pakpahan, “ANALISIS FENOMENA HOAX DIBERBAGAI MEDIA SOSIAL DAN CARA MENANGGULANGI HOAX,” Konferensi Nasional Ilmu Sosial & Teknologi (KNiST), vol. 1, no. 1, pp. 479–484, Mar. 2017, Accessed: Sep. 17, 2022. [Online]. Available: http://seminar.bsi.ac.id/knist/index.php/UnivBSI/article/view/184
R. Rustandi, “Analisis Framing Kontra Narasi Terorisme dan Radikalisme di Media Sosial (Studi Kasus pada Akun @dutadamaijabar),” Jurnal Komunikatif, vol. 9, no. 2, pp. 134–153, Dec. 2020, doi: 10.33508/jk.v9i2.2698.
M. Nur Faiz, W. Adi Prabowo, and M. Fajar Sidiq, “Journal of Informatics, Information System, Software Engineering and Applications Studi Komparasi Investigasi Digital Forensik pada Tindak Kriminal,” vol. 1, no. 1, pp. 63–70, 2018, doi: 10.20895/INISTA.V1I1.
D. Ranđelović and D. Stojković, “Possibilities of autopsy tool use for forensic purposes,” Nauka, bezbednost, policija, vol. 17, no. 3, pp. 19–33, 2012.
D. C. Harrill and R. P. Mislan, “A Small Scale Digital Device Forensics ontology,” Small Scale Digital Device Forensics Journal, vol. 1, no. 1, pp. 1–7, 2007.
N. M. Karie and H. S. Venter, “Toward a general ontology for digital forensic disciplines,” J Forensic Sci, vol. 59, no. 5, pp. 1231–1241, 2014, doi: 10.1111/1556-4029.12511.
E. Kalemi and S. Yildirim-yayilgan, “Ontologies for Social Media Digital Evidence,” no. January, 2016.
E. Kalemi, S. Yildirim-Yayilgan, E. Domnori, and O. Elezaj, “SMoNt: An ontology for crime solving through social media,” Int J Metadata Semant Ontol, vol. 12, no. 2–3, pp. 71–81, 2017, doi: 10.1504/IJMSO.2017.090756.
“Download Magisk Manager Latest Version 26.3 For Android 2023.” https://magiskmanager.com/ (accessed Sep. 18, 2023).
“GitHub - topjohnwu/Magisk: The Magic Mask for Android.” https://github.com/topjohnwu/Magisk (accessed Sep. 18, 2023).
M.-R. Boueiz, “Importance of rooting in an Android data acquisition,” in 2020 8th International Symposium on Digital Forensics and Security (ISDFS), IEEE, Jun. 2020, pp. 1–4. doi: 10.1109/ISDFS49300.2020.9116445.
H. H. Lwin, W. P. Aung, and K. K. Lin, “Comparative Analysis of Android Mobile Forensics Tools.”
“Android Debug Bridge (adb) | Android Studio | Android Developers.” https://developer.android.com/tools/adb (accessed Sep. 18, 2023).
T. Almehmadi and O. Batarfi, “Impact of Android Phone Rooting on User Data Integrity in Mobile Forensics,” in 2019 2nd International Conference on Computer Applications & Information Security (ICCAIS), IEEE, May 2019, pp. 1–6. doi: 10.1109/CAIS.2019.8769520.
“BusyBox.” https://www.busybox.net/ (accessed Sep. 18, 2023).
Downloads
Published
Issue
Section
License
Copyright (c) 2023 Ibnu Rohan Tuharea, Ahmad Luthfi, Erika Ramadani

This work is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License.
Start from 2019 issues, authors who publish with JURNAL MOBILE AND FORENSICS agree to the following terms:
- Authors retain copyright and grant the journal right of first publication with the work simultaneously licensed under a Creative Commons Attribution License (CC BY-SA 4.0) that allows others to share the work with an acknowledgment of the work's authorship and initial publication in this journal.
- Authors are able to enter into separate, additional contractual arrangements for the non-exclusive distribution of the journal's published version of the work (e.g., post it to an institutional repository or publish it in a book), with an acknowledgment of its initial publication in this journal.
- Authors are permitted and encouraged to post their work online (e.g., in institutional repositories or on their website) prior to and during the submission process, as it can lead to productive exchanges, as well as earlier and greater citation of published work.

This work is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License.












 Mobile and Forensics (MF)
Mobile and Forensics (MF)