Digital Forensic Analysis of Telegram Messenger App in Android Virtual Environment
DOI:
https://doi.org/10.12928/mf.v4i1.5537Keywords:
Telegram, Android, Digital ForensicsAbstract
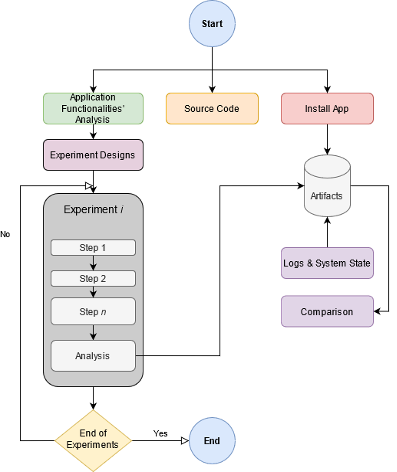
The paper provides an in-depth analysis of the artifacts generated by the Telegram Messenger application on Android OS which provides secure communications between individuals, groups, and channels. Since the past few years, the application went through major changes and updates and the latest version’s artifacts varied from the previous ones. Our methodology is based on the set of experiments designed to generate the artifacts from various use cases on the virtualized environment. The acquired artifacts such as messages, their location, and data structure how they relate to one another were studied and were then compared to the older versions. By correlating the artifacts of newer version with the older ones, it shows how the application have been upgraded behind the scenes and by incorporating those results can provide investigators better understanding and insight for the certain evidence in a potential cybercrime case.
References
M. Landwehr, A. Borning, and V. Wulf, ‘The High Cost of Free Services: Problems with Surveillance Capitalism and Possible Alternatives for IT Infrastructure’, in Proceedings of the Fifth Workshop on Computing within Limits, Lappeenranta Finland, Jun. 2019, pp. 1–10. doi: 10.1145/3338103.3338106.
C. Q. Lau, A. Cronberg, L. Marks, and A. Amaya, ‘In Search of the Optimal Mode for Mobile Phone Surveys in Developing Countries. A Comparison of IVR, SMS, and CATI in Nigeria’, Survey Research Methods, pp. 305-318 Pages, Dec. 2019, doi: 10.18148/SRM/2019.V13I3.7375.
T. text provides general information S. assumes no liability for the information given being complete or correct D. to varying update cycles and S. C. D. M. up-to-D. D. T. R. in the Text, ‘Topic: Internet usage worldwide’, Statista. https://www.statista.com/topics/1145/internet-usage-worldwide/ (accessed Mar. 07, 2022).
C. Ruiz-Mafe, E. Bigné-Alcañiz, and R. Currás-Pérez, ‘The effect of emotions, eWOM quality and online review sequence on consumer intention to follow advice obtained from digital services’, JOSM, vol. 31, no. 3, pp. 465–487, Jun. 2020, doi: 10.1108/JOSM-11-2018-0349.
Department of IT Convergence Engineering, School of Electronic Engineering, Kumoh National Institute of Technology, Gumi, South Korea, G. B. Satrya, and S. Y. Shin, ‘Optimizing Rule on Open Source Firewall Using Content and PCRE Combination’, JACN, vol. 3, no. 4, pp. 308–314, 2015, doi: 10.18178/JACN.2015.3.4.188.
G. B. Satrya, N. D. W. Cahyani, and R. F. Andreta, ‘The Detection of 8 Type Malware botnet using Hybrid Malware Analysis in Executable File Windows Operating Systems’, in Proceedings of the 17th International Conference on Electronic Commerce 2015 - ICEC ’15, Seoul, Republic of Korea, 2015, pp. 1–4. doi: 10.1145/2781562.2781567.
G. B. Satrya, P. T. Daely, and S. Y. Shin, ‘Android forensics analysis: Private chat on social messenger’, in 2016 Eighth International Conference on Ubiquitous and Future Networks (ICUFN), Vienna, Austria, Jul. 2016, pp. 430–435. doi: 10.1109/ICUFN.2016.7537064.
S. C. Sathe and N. M. Dongre, ‘Data acquisition techniques in mobile forensics’, in 2018 2nd International Conference on Inventive Systems and Control (ICISC), Coimbatore, Jan. 2018, pp. 280–286. doi: 10.1109/ICISC.2018.8399079.
L. D. Turner et al., ‘Evidence to support common application switching behaviour on smartphones’, R. Soc. open sci., vol. 6, no. 3, p. 190018, Mar. 2019, doi: 10.1098/rsos.190018.
C. Anglano, M. Canonico, and M. Guazzone, ‘Forensic analysis of Telegram Messenger on Android smartphones’, Digital Investigation, vol. 23, pp. 31–49, Dec. 2017, doi: 10.1016/j.diin.2017.09.002.
A. Mahajan, M. S. Dahiya, and H. P. Sanghvi, ‘Forensic Analysis of Instant Messenger Applications on Android Devices’, IJCA, vol. 68, no. 8, pp. 38–44, Apr. 2013, doi: 10.5120/11602-6965.
A. K. Agrawal, A. Sharma, and P. Khatri, ‘Digital Forensic Analysis of Facebook App in Virtual Environment’, 2019 6th International Conference on Computing for Sustainable Global Development (INDIACom), Mar. 2019.
M. R. Arshad, M. Hussain, H. Tahir, S. Qadir, F. I. Ahmed Memon, and Y. Javed, ‘Forensic Analysis of Tor Browser on Windows 10 and Android 10 Operating Systems’, IEEE Access, vol. 9, pp. 141273–141294, 2021, doi: 10.1109/ACCESS.2021.3119724.
A. Afzal, M. Hussain, S. Saleem, M. K. Shahzad, A. T. S. Ho, and K.-H. Jung, ‘Encrypted Network Traffic Analysis of Secure Instant Messaging Application: A Case Study of Signal Messenger App’, Applied Sciences, vol. 11, no. 17, p. 7789, Aug. 2021, doi: 10.3390/app11177789.
N. Anwar, M. M. Mardhia, and L. Ryanto, ‘Live Forensics on GPS inactive Smartphone’, mob.forensics.j, vol. 3, no. 1, pp. 32–44, Mar. 2021, doi: 10.12928/mf.v3i1.3847.
N. Al Mutawa, J. Bryce, V. N. L. Franqueira, A. Marrington, and J. C. Read, ‘Behavioural Digital Forensics Model: Embedding Behavioural Evidence Analysis into the Investigation of Digital Crimes’, Digital Investigation, vol. 28, pp. 70–82, Mar. 2019, doi: 10.1016/j.diin.2018.12.003.
B. O. Gardner, S. Kelley, D. C. Murrie, and I. E. Dror, ‘What do forensic analysts consider relevant to their decision making?’, Science & Justice, vol. 59, no. 5, pp. 516–523, Sep. 2019, doi: 10.1016/j.scijus.2019.04.005.
T. Hermawan, Y. Suryanto, F. Alief, and L. Roselina, ‘Android Forensic Tools Analysis for Unsend Chat on Social Media’, in 2020 3rd International Seminar on Research of Information Technology and Intelligent Systems (ISRITI), Yogyakarta, Indonesia, Dec. 2020, pp. 233–238. doi: 10.1109/ISRITI51436.2020.9315364.
‘Schema’. https://core.telegram.org/schema (accessed Mar. 07, 2022).
DrKLO, DrKLO/Telegram. 2022. Accessed: Jan. 07, 2022. [Online]. Available: https://github.com/DrKLO/Telegram
Downloads
Published
Issue
Section
License
Copyright (c) 2022 Ahmed Raza, Muhammad Bilal Hassan

This work is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License.
Start from 2019 issues, authors who publish with JURNAL MOBILE AND FORENSICS agree to the following terms:
- Authors retain copyright and grant the journal right of first publication with the work simultaneously licensed under a Creative Commons Attribution License (CC BY-SA 4.0) that allows others to share the work with an acknowledgment of the work's authorship and initial publication in this journal.
- Authors are able to enter into separate, additional contractual arrangements for the non-exclusive distribution of the journal's published version of the work (e.g., post it to an institutional repository or publish it in a book), with an acknowledgment of its initial publication in this journal.
- Authors are permitted and encouraged to post their work online (e.g., in institutional repositories or on their website) prior to and during the submission process, as it can lead to productive exchanges, as well as earlier and greater citation of published work.

This work is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License.












 Mobile and Forensics (MF)
Mobile and Forensics (MF)