Live Forensics on GPS inactive Smartphone
DOI:
https://doi.org/10.12928/mf.v3i1.3847Keywords:
Live Forensic, Location History, Activity Google, Mobile Forensic, SmartphoneAbstract
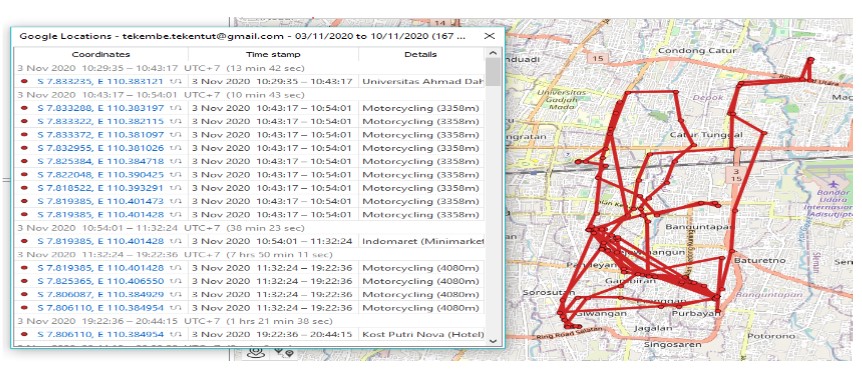
Google is known to still track the user's location despite the GPS settings and location history in smartphone settings has been turned off by the user. This requires special handling to prove the location on smartphones with inactive GPS and view its Location History previously used by user. The research investigates if Google is still recording its user data location. Live Forensic requires data from the running system or volatile data which is usually found in Random Access Memory (RAM) or transit on the network. Investigations are carried out using a Google account with a method used by live forensics to obtain results from the location history. Smartphones have been checked manually through data backup through custom recovery that has been installed. When checking the backup filesystem, turned out that no location data is stored. Therefore, researchers conducted an analysis on the Google Account which was analyzed using a forensic tool to analyze cloud services to obtain location data results. The results of the analysis carried out obtained a similarity in location from 8-days investigations. Google can still find the location of smartphones with GPS disabled, but the location results are not accurate. Google can store user location data via cellular networks, Wi-Fi, and sensors to help estimate the user's location. The process of extracting the results from the google maps log using a Google account will be analyzed using the Elcomsoft Cloud eXplorer and Oxygen Forensic Cloud Extractor so that the log location results are still available by Google.
References
A. Camero and E. Alba, ‘Smart City and information technology: A review’, Cities, vol. 93, pp. 84–94, Oct. 2019, doi: 10.1016/j.cities.2019.04.014.
A. J. Gray, K. Shorter, C. Cummins, A. Murphy, and M. Waldron, ‘Modelling Movement Energetics Using Global Positioning System Devices in Contact Team Sports: Limitations and Solutions’, Sports Med, vol. 48, no. 6, pp. 1357–1368, Jun. 2018, doi: 10.1007/s40279-018-0899-z.
D. Plikynas, A. Žvironas, A. Budrionis, and M. Gudauskis, ‘Indoor Navigation Systems for Visually Impaired Persons: Mapping the Features of Existing Technologies to User Needs’, Sensors, vol. 20, no. 3, p. 636, Jan. 2020, doi: 10.3390/s20030636.
F. Sergio, A. Tanferna, J. Blas, G. Blanco, and F. Hiraldo, ‘Reliable methods for identifying animal deaths in GPS- and satellite-tracking data: Review, testing, and calibration’, J Appl Ecol, vol. 56, no. 3, pp. 562–572, Mar. 2019, doi: 10.1111/1365-2664.13294.
K. Rajalakshmi and M. Goyal, ‘Location-Based Services: Current State of The Art and Future Prospects’, in Optical and Wireless Technologies, vol. 472, V. Janyani, M. Tiwari, G. Singh, and P. Minzioni, Eds. Singapore: Springer Singapore, 2018, pp. 625–632. doi: 10.1007/978-981-10-7395-3_69.
S. Alfeno and R. E. C. Devi, ‘Implementasi Global Positioning System (GPS) dan Location Based Service (LSB) pada Sistem Informasi Kereta Api untuk Wilayah Jabodetabek’, Jurnal Sisfotek Global, vol. 7, no. 2, p. 7, 2017, doi: 10.38101/sisfotek.v7i2.146.
T.-W. Chien, H.-Y. Wang, Y. Chang, and W.-C. Kan, ‘Using Google Maps to display the pattern of coauthor collaborations on the topic of schizophrenia: A systematic review between 1937 and 2017’, Schizophrenia Research, vol. 204, pp. 206–213, Feb. 2019, doi: 10.1016/j.schres.2018.09.015.
E. Budiman, ‘Pemanfaatan Teknologi Location Based Service Dalam Pengembangan Aplikasi Profil Kampus Universitas Mulawarman Berbasis Mobile’, Ilk. J. Ilm., vol. 8, no. 3, pp. 137–144, Dec. 2016, doi: 10.33096/ilkom.v8i3.81.137-144.
E. Anggraini, ‘Cara “Melarikan Diri” dari Pengintaian Google’, teknologi, 2018. https://www.cnnindonesia.com/teknologi/20180815104301-185-322404/cara-melarikan-diri-dari-pengintaian-google (accessed Feb. 11, 2022).
S. Sack, K. Kröger, and R. Creutzburg, ‘Location tracking forensics on mobile devices’, Burlingame, California, USA, Mar. 2013, p. 866712. doi: 10.1117/12.2003952.
S. Sukriadi and Y. Prayudi, ‘Analisis Bukti Digital Global Positioning System (GPS) Pada Smartphone Android’, Konferensi Nasional Sistem dan Informatika, p. 7, Nov. 2014.
K. Sansurooah and B. Keane, ‘The spy in your pocket: Smartphones and geo-location data’, 13th Australian Digital Forensics Conference, vol. held from the 30 November – 2 December, p. Western Australia., 2015, doi: 10.4225/75/57B3FB68FB88E.
B. Rindiatmodjo, F. Megantara, and M. I. Pratama, ‘Pelacakan Keberadaan Ponsel Berbasis Android dengan Menggunakan Teknologi Short Message Service (SMS) dan Global Positioning System (GPS)’.
J. Moore, I. Baggili, and F. Breitinger, ‘Find Me If You Can: Mobile GPS Mapping Applications Forensic Analysis & SNAVP the Open Source, Modular, Extensible Parser’, JDFSL, 2017, doi: 10.15394/jdfsl.2017.1414.
K. K. Çevi̇K, F. S. Berber, and E. U. Küçüksi̇Lle, ‘Mapping location of a suspect by using forensic images taken with their own mobile phone’, International Conference on Engineering Technologies, p. 5, 2018.
E. Williams and J. Yerby, ‘Google and Facebook Data Retention and Location Tracking through Forensic Cloud Analysis’, p. 7, 2019.
A. Sah, I. Riadi, and Y. Prayudi, ‘Deteksi Bukti Digital Online Gambling Menggunakan Live Forensik Pada Smartphone Berbasis Android’, csecurity, vol. 1, no. 1, pp. 14–19, Jul. 2018, doi: 10.14421/csecurity.2018.1.1.1237.
R. A. K. N. Bintang, R. Umar, and A. Yudhana, ‘Perancangan Perbandingan Live Forensics Pada Keamanan Media Sosial Instagram, Facebook Dan Twitter Di Windows 10’, Prosiding SNST, vol. 9, 2018.
H. Zhang, D. She, and Z. Qian, ‘Android Root and its Providers: A Double-Edged Sword’, in Proceedings of the 22nd ACM SIGSAC Conference on Computer and Communications Security, Denver Colorado USA, Oct. 2015, pp. 1093–1104. doi: 10.1145/2810103.2813714.
Z. Zhang, Y. Wang, J. Jing, Q. Wang, and L. Lei, ‘Once Root Always a Threat: Analyzing the Security Threats of Android Permission System’, in Information Security and Privacy, vol. 8544, W. Susilo and Y. Mu, Eds. Cham: Springer International Publishing, 2014, pp. 354–369. doi: 10.1007/978-3-319-08344-5_23.
Downloads
Published
Issue
Section
License
Copyright (c) 2021 Nuril Anwar, Murein Miksa Mardhia, Luthfi Ryanto

This work is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License.
Start from 2019 issues, authors who publish with JURNAL MOBILE AND FORENSICS agree to the following terms:
- Authors retain copyright and grant the journal right of first publication with the work simultaneously licensed under a Creative Commons Attribution License (CC BY-SA 4.0) that allows others to share the work with an acknowledgment of the work's authorship and initial publication in this journal.
- Authors are able to enter into separate, additional contractual arrangements for the non-exclusive distribution of the journal's published version of the work (e.g., post it to an institutional repository or publish it in a book), with an acknowledgment of its initial publication in this journal.
- Authors are permitted and encouraged to post their work online (e.g., in institutional repositories or on their website) prior to and during the submission process, as it can lead to productive exchanges, as well as earlier and greater citation of published work.

This work is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License.












 Mobile and Forensics (MF)
Mobile and Forensics (MF)