Malware Static Analysis on Microsoft Macro Attack
DOI:
https://doi.org/10.12928/mf.v3i1.3764Keywords:
Malware Analysis, Static Analysis, Dynamic Analysis, Cyber-attack, Macro MalwareAbstract
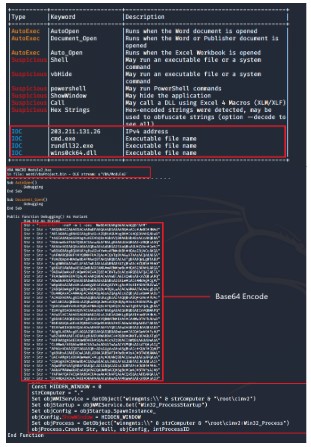
In the 21st century, technology is increasing rapidly, the increase in technology is the potential for cyber attacks on today's technological infrastructure. Malware that is designed to damage computer systems without the owner's knowledge at a considerable cost becomes a cyber crime. This macro malware analysis is to study the code and behavior of malware when run on an operating system. To analyze this malware, this study uses a static analysis method by analyzing malware without running the program.References
S. Saad, W. Briguglio, and H. Elmiligi, ‘The Curious Case of Machine Learning In Malware Detection’, arXiv:1905.07573 [cs], May 2019, Accessed: Feb. 11, 2022. [Online]. Available: http://arxiv.org/abs/1905.07573
J. C. Sapalo Sicato, P. K. Sharma, V. Loia, and J. H. Park, ‘VPNFilter Malware Analysis on Cyber Threat in Smart Home Network’, Applied Sciences, vol. 9, no. 13, p. 2763, Jul. 2019, doi: 10.3390/app9132763.
H. F. Atlam, E. El-Din Hemdan, A. Alenezi, M. O. Alassafi, and G. B. Wills, ‘Internet of Things Forensics: A Review’, Internet of Things, vol. 11, p. 100220, Sep. 2020, doi: 10.1016/j.iot.2020.100220.
B. Yu, Y. Fang, Q. Yang, Y. Tang, and L. Liu, ‘A survey of malware behavior description and analysis’, Frontiers Inf Technol Electronic Eng, vol. 19, no. 5, pp. 583–603, May 2018, doi: 10.1631/FITEE.1601745.
P. Singh, S. Tapaswi, and S. Gupta, ‘Malware Detection in PDF and Office Documents: A survey’, Information Security Journal: A Global Perspective, vol. 29, no. 3, pp. 134–153, May 2020, doi: 10.1080/19393555.2020.1723747.
M. Elingiusti, L. Aniello, L. Querzoni, and R. Baldoni, ‘PDF-Malware Detection: A Survey and Taxonomy of Current Techniques’, in Cyber Threat Intelligence, vol. 70, A. Dehghantanha, M. Conti, and T. Dargahi, Eds. Cham: Springer International Publishing, 2018, pp. 169–191. doi: 10.1007/978-3-319-73951-9_9.
E. G. Dada, J. S. Bassi, H. Chiroma, S. M. Abdulhamid, A. O. Adetunmbi, and O. E. Ajibuwa, ‘Machine learning for email spam filtering: review, approaches and open research problems’, Heliyon, vol. 5, no. 6, p. e01802, Jun. 2019, doi: 10.1016/j.heliyon.2019.e01802.
A. Karim, S. Azam, B. Shanmugam, K. Kannoorpatti, and M. Alazab, ‘A Comprehensive Survey for Intelligent Spam Email Detection’, IEEE Access, vol. 7, pp. 168261–168295, 2019, doi: 10.1109/ACCESS.2019.2954791.
L. Jaeger, ‘Information Security Awareness: Literature Review and Integrative Framework’, presented at the Hawaii International Conference on System Sciences, 2018. doi: 10.24251/HICSS.2018.593.
J. G. Drever, B. Third, and C. Sampson, ‘The use of static analysis to detect malware in embedded systems’, in 8th IET International System Safety Conference incorporating the Cyber Security Conference 2013, Cardiff, UK, 2013, p. 6.2-6.2. doi: 10.1049/cp.2013.1722.
U. Mishra, ‘Detecting Macro Viruses- A TRIZ Based Analysis’, SSRN Journal, 2012, doi: 10.2139/ssrn.1981892.
D. Ucci, L. Aniello, and R. Baldoni, ‘Survey of machine learning techniques for malware analysis’, Computers & Security, vol. 81, pp. 123–147, Mar. 2019, doi: 10.1016/j.cose.2018.11.001.
S. Sibi Chakkaravarthy, D. Sangeetha, and V. Vaidehi, ‘A Survey on malware analysis and mitigation techniques’, Computer Science Review, vol. 32, pp. 1–23, May 2019, doi: 10.1016/j.cosrev.2019.01.002.
Q.-D. Ngo, H.-T. Nguyen, V.-H. Le, and D.-H. Nguyen, ‘A survey of IoT malware and detection methods based on static features’, ICT Express, vol. 6, no. 4, pp. 280–286, Dec. 2020, doi: 10.1016/j.icte.2020.04.005.
S. K. Nayak and A. C. Ojha, ‘Data Leakage Detection and Prevention: Review and Research Directions’, in Machine Learning and Information Processing, vol. 1101, D. Swain, P. K. Pattnaik, and P. K. Gupta, Eds. Singapore: Springer Singapore, 2020, pp. 203–212. doi: 10.1007/978-981-15-1884-3_19.
M. N. Alenezi, H. Alabdulrazzaq, A. A. Alshaher, and M. M. Alkharang, ‘Evolution of Malware Threats and Techniques: A Review’, vol. 12, no. 3, p. 12, 2020.
A. Kumar, M. Gupta, G. Kumar, A. Handa, N. Kumar, and S. K. Shukla, ‘A Review: Malware Analysis Work at IIT Kanpur’, in Cyber Security in India, vol. 4, S. K. Shukla and M. Agrawal, Eds. Singapore: Springer Singapore, 2020, pp. 39–48. doi: 10.1007/978-981-15-1675-7_5.
D. Maimon and E. R. Louderback, ‘Cyber-Dependent Crimes: An Interdisciplinary Review’, Annu. Rev. Criminol., vol. 2, no. 1, pp. 191–216, Jan. 2019, doi: 10.1146/annurev-criminol-032317-092057.
Md. F. Sohan and A. Basalamah, ‘A Systematic Literature Review and Quality Analysis of Javascript Malware Detection’, IEEE Access, vol. 8, pp. 190539–190552, 2020, doi: 10.1109/ACCESS.2020.3031690.
P. Romaniuk, ‘Crime and Criminal Justice’, in The Oxford Handbook on the United Nations, T. G. Weiss and S. Daws, Eds. Oxford University Press, 2018, pp. 514–527. doi: 10.1093/oxfordhb/9780198803164.013.28.
Downloads
Published
Issue
Section
License
Copyright (c) 2021 Redho Maland Aresta, Ero Wahyu Pratomo, Vicky Geraldino, Achmad Fauzi, Joko Dwi Santoso

This work is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License.
Start from 2019 issues, authors who publish with JURNAL MOBILE AND FORENSICS agree to the following terms:
- Authors retain copyright and grant the journal right of first publication with the work simultaneously licensed under a Creative Commons Attribution License (CC BY-SA 4.0) that allows others to share the work with an acknowledgment of the work's authorship and initial publication in this journal.
- Authors are able to enter into separate, additional contractual arrangements for the non-exclusive distribution of the journal's published version of the work (e.g., post it to an institutional repository or publish it in a book), with an acknowledgment of its initial publication in this journal.
- Authors are permitted and encouraged to post their work online (e.g., in institutional repositories or on their website) prior to and during the submission process, as it can lead to productive exchanges, as well as earlier and greater citation of published work.

This work is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License.












 Mobile and Forensics (MF)
Mobile and Forensics (MF)