Ekstraksi Logis Forensik Mobile pada Aplikasi E-Commerce Android
DOI:
https://doi.org/10.12928/mf.v2i1.1791Abstract
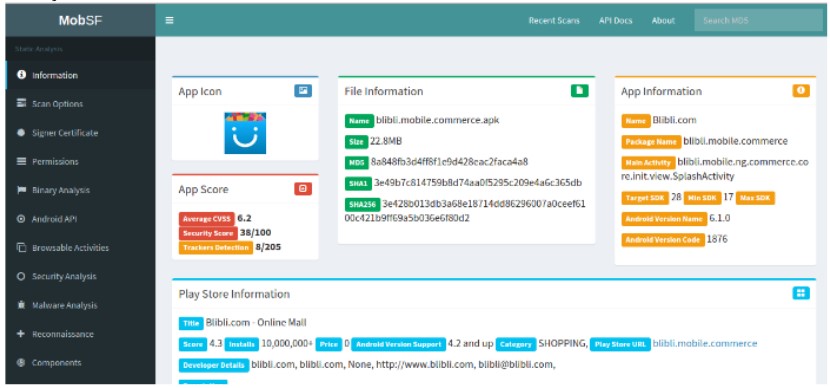
Pesatnya perkembangan aplikasi android, terutama aplikasi di bidang e-commerce dan transaksi jual beli online yang populer di Indonesia, memaksa pengguna untuk memberikan izin untuk menggunakan fitur dan layanan aplikasi selama pemasangan dan pasca pemasangan. Kurangnya pemahaman pengguna akan resiko dari izin akses yang diminta oleh aplikasi sebelum atau setelah melakukan instalasi menjadikan celah pada keamanan data pengguna untuk mengakses fitur pada perangkat smartphone seperti kamera, media penyimpanan, kontak, akun dan fitur lainnya. Logical Extraction Method menjadi metode yang digunakan untuk mendapatkan data aplikasi dengan mengakusisi seluruh data file sistem pada smartphone menggunakan bantuan tools MOBILedit Forensic, TWRP (Team Win Recovery Project), dan Aplikasi Migrate. Akusisi data dari masing-masing aplikasi akan diambil Android Package File (APK) yang digunakan untuk proses analisis secara statis dengan menggunakan Tools Forensic MobSF (Mobile Security Framework). Berdasarkan hasil analisis yang dilakukan pada tiga aplikasi teratas e-commerce terdapat 51 izin akses dan dari tiga aplikasi e-commerce terpopuler di Indonesia dengan tingkat keamanan paling berbahaya dengan 49 izin akses, 7 izin akses normal dan 1 izin akses tanda tangan. Aplikasi lazada terdapat 21 izin akses berbahaya yang tidak diketahui pengguna sedangkan aplikasi Tokopedia terdapat 4 izin akses berbahaya yang tidak diketahui pengguna dan aplikasi Blibli.com terdapat 1 izin akses berbahaya yang tidak diketahui pengguna. Berdasarkan temuan celah keamanan dapat disimpulkan bahwa aplikasi e-commerce yang digunakan oleh penggunanya memungkinkan pula disisipi sebuah malware atau virus sejenis yang berpeluang dalam penggambilan data pribadi penggunanya.
The rapid development of android applications, especially applications in the field of e-commerce and online buying and selling transactions that are popular in Indonesia, force users to give permission to use the features and services of the application during installation and post-installation. Lack of user understanding of the risk of access permissions requested by the application before or after installation creates a gap in the user's data security to access features on smartphone devices such as cameras, storage media, contacts, accounts, and other features. Logical Extraction Method is a method used to obtain application data by acquiring all system file data on smartphones using the help of MOBILedit Forensic tools, TWRP (Team Win Recovery Project), and Migrate Applications. Data acquisition from each application will be taken by Android Package File (APK) which is used for the static analysis process using Tools Forensic MobSF (Mobile Security Framework). Based on the results of an analysis conducted on the top three e-commerce applications there are 51 access permits and of the three most popular e-commerce applications in Indonesia with the most dangerous level of security with 49 access permits, 7 normal access permits, and 1 signature access permit. The Lazada application has 21 dangerous access permits that the user does not know while the Tokopedia application has 4 dangerous access permits that the user does not know and the Blibli.com application has 1 dangerous access permit that the user does not know about. Based on the findings of a security hole, it can be concluded that the e-commerce application used by its users also allows the insertion of a malware or virus that has the opportunity to capture the user's personal data.
References
N. Viet Duc, P. Thanh Giang, and P. Minh Vi, "Permission Analysis for Android Malware," no. February 2012, pp. 207-216, 2017.
H. Dong, N. Q. He, G. Hu, Q. Li, and M. Zhang, "Malware detection method of android application based on simplification instructions," J. China Univ. Posts Telecommun., vol. 21, no. SUPPL. 1, pp. 94-100, 2014.
S. H. Mohtasebi and A. Dehghantanha, "Towards a Unified Forensic Investigation Framework of Smartphones," Int. J. Comput. Theory Eng., vol. 5, no. 2, pp. 351-355, 2013.
W. Wang, X. Wang, D. Feng, J. Liu, Z. Han, and X. Zhang, "Exploring Permission-Induced Risk in Android Applications for Malicious Application Detection," vol. 9, no. 11, pp. 1869-1882, 2014.
A. P. Heriyanto, Mobile Phone Forensics: Theory: Mobile Phone Forensics dan Security Series. Yogyakarta: Perpustakaan Nasional, 2016.
R. Tammaics and D. Tindall, "Learning Android Forensics," 2015.
N. V. Duc, P. T. Giang, and P. M. Vi, "Permission Analysis for Android Malware," Proc. 7th VAST - AIST Work. "RESEARCH Collab. Rev. Perspect.," no. November 2015, pp. 207-216, 2016.
N. Y. P. Lukito, F. A. Yulianto, and E. Jadied, "Comparison of data acquisition technique using logical extraction method on Unrooted Android Device," 2016 4th Int. Conf. Inf. Commun. Technol. ICoICT 2016, vol. 4, no. c, 2016.
X. Lin, T. Chen, T. Zhu, K. Yang, and F. Wei, "Automated forensic analysis of mobile applications on android devices," Proc. Digit. Forensic Res. Conf. DFRWS 2018 USA, vol. 26, pp. S59-S66, 2018.
D. Walnycky et al., "Network and device forensic analysis of Android social-messaging applications," 2015.
C. L. Liu, N. T. Hua, and A. B. Tucker, Software Engineering A Practitioner's Approach. .
M. Howard, A. Pfeffer, M. Dalai, and M. Reposa, "Predicting signatures of future malware variants," Proc. 2017 12th Int. Conf. Malicious Unwanted Software, MALWARE 2017, vol. 2018-January, pp. 126-132, 2018.
R. Ayers, W. Jansen, and S. Brothers, "Guidelines on mobile device forensics (NIST Special Publication 800-101 Revision 1)," NIST Spec. Publ., vol. 1, no. 1, p. 85, 2014.
" | Android Developers." [Online]. Available: https://developer.android.com/guide/topics/manifest/permission-element. [Accessed: 22-Apr-2020].
Downloads
Published
Issue
Section
License
Copyright (c) 2020 Nuril Anwar, Son Ali Akbar, Ahmad Azhari, Imam Suryanto

This work is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License.
Start from 2019 issues, authors who publish with JURNAL MOBILE AND FORENSICS agree to the following terms:
- Authors retain copyright and grant the journal right of first publication with the work simultaneously licensed under a Creative Commons Attribution License (CC BY-SA 4.0) that allows others to share the work with an acknowledgment of the work's authorship and initial publication in this journal.
- Authors are able to enter into separate, additional contractual arrangements for the non-exclusive distribution of the journal's published version of the work (e.g., post it to an institutional repository or publish it in a book), with an acknowledgment of its initial publication in this journal.
- Authors are permitted and encouraged to post their work online (e.g., in institutional repositories or on their website) prior to and during the submission process, as it can lead to productive exchanges, as well as earlier and greater citation of published work.

This work is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License.












 Mobile and Forensics (MF)
Mobile and Forensics (MF)