Digital Forensics on APK Files: A Combined Approach Using MobSF and GHIDRA
DOI:
https://doi.org/10.12928/mf.v7i2.14088Keywords:
Forensics, MobSF, GHIDRA, Reverse Engineering, AnalysisAbstract
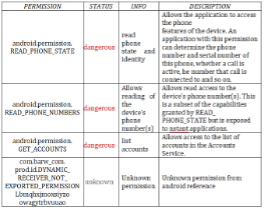
The rapid growth of Android smartphones has increased user convenience but also elevated the risk of cybercrime, especially malware attacks using complex obfuscation techniques that hinder detection and analysis. Traditional methods are often insufficient to address these evolving threats. This study integrates automated and manual analysis on APK files using Mobile Security Framework (MobSF) and GHIDRA through reverse engineering. MobSF performs automated static analysis to identify vulnerabilities and security indicators, while GHIDRA is used to decompile binary code into pseudocode for in-depth manual verification. The analysis of the “Pencairan Hadiah” (Prize Disbursement) application revealed dangerous permissions such as RECEIVE_SMS, READ_PHONE_STATE, and SYSTEM_ALERT_WINDOW. Manual inspection with GHIDRA confirmed API calls like getImei() and access to the Telegram API for automated data transmission. Although the bot token was inactive, the findings indicate an intent to exfiltrate sensitive data. The integration of MobSF and GHIDRA provides a deeper understanding and concrete evidence of malicious behavior in APK files, demonstrating the effectiveness of combining automated and manual approaches in digital forensic analysis.
References
C. A. Teodorescu, A.-N. Ciucu Durnoi, and V. M. Vargas, “The Rise of the Mobile Internet: Tracing the Evolution of Portable Devices,” Proc. Int. Conf. Bus. Excell., vol. 17, no. 1, pp. 1645–1654, July 2023, doi: 10.2478/picbe-2023-0147.
S. L. Sanna, D. Soi, D. Maiorca, G. Fumera, and G. Giacinto, “A risk estimation study of native code vulnerabilities in Android applications,” J. Cybersecurity, vol. 10, no. 1, p. tyae015, Jan. 2024, doi: 10.1093/cybsec/tyae015.
Nurul Qomariah, Erick Irawadi Alwi, and Muhammad Arfah Asis, “Analisis Malware Hummingbad Dan Copycat Pada Android Menggunakan Metode Hybrid,” Cyber Secur. Dan Forensik Digit., vol. 6, no. 2, pp. 39–47, Feb. 2024, doi: 10.14421/csecurity.2023.6.2.4180.
M. W. A. Prastya et al., “Analisis Ancaman Pishing melalui Aplikasi WhatsApp: Review Metode Studi Literatur,” J. Nas. Komputasi Dan Teknol. Inf. JNKTI, vol. 7, no. 3, pp. 190–197, June 2024, doi: 10.32672/jnkti.v7i3.7551.
K. Ibrahim, F. Dewanta, and N. D. W. Cahyani, “Analisis Perilaku Malware Malware Menggunakan Metode Analisis Dinamis,” EProceedings Eng., vol. 10, no. 5, 2023.
I. Himawan, K. Septianzah, and I. Setiadi, “Analisa Resiko Malware dengan Static MobSF Terhadap Aplikasi Android APK,” Technol. J. Ilm., vol. 14, no. 4, p. 364, Oct. 2023, doi: 10.31602/tji.v14i4.11460.
A. R. Damanik, H. B. Seta, and T. Theresiawati, “Analisis Trojan dan Spyware Menggunakan Metode Hybrid Analysis,” J. Ilm. Matrik, vol. 25, no. 1, pp. 89–97, May 2023, doi: 10.33557/jurnalmatrik.v25i1.2327.
R. N. Yasa and A. C. F. Nugraha, “Perbandingan Keamanan Aplikasi Pesan Instan Android Menggunakan MobSF (Mobile Security Framework) Berdasarkan Beberapa Standar,” Info Kripto, vol. 18, no. 1, pp. 9–14, May 2024, doi: 10.56706/ik.v18i1.88.
W. K. Wong et al., “DecLLM: LLM-Augmented Recompilable Decompilation for Enabling Programmatic Use of Decompiled Code,” Proc. ACM Softw. Eng., vol. 2, no. ISSTA, pp. 1841–1864, June 2025, doi: 10.1145/3728958.
R. Almohaini, I. Almomani, and A. AlKhayer, “Hybrid-Based Analysis Impact on Ransomware Detection for Android Systems,” Appl. Sci., vol. 11, no. 22, p. 10976, Nov. 2021, doi: 10.3390/app112210976.
Y. Agman and D. Hendler, “BPFroid: Robust Real Time Android Malware Detection Framework,” 2021, arXiv. doi: 10.48550/ARXIV.2105.14344.
X. Zhang, F. Breitinger, E. Luechinger, and S. O’Shaughnessy, “Android application forensics: A survey of obfuscation, obfuscation detection and deobfuscation techniques and their impact on investigations,” Forensic Sci. Int. Digit. Investig., vol. 39, p. 301285, Dec. 2021, doi: 10.1016/j.fsidi.2021.301285.
Frenvol De Santonario Magno Moises and Joko Dwi Santoso, “Analisis Malware Android Menggunakan Metode Reverse Engineering,” J. Ilm. Dan Karya Mhs., vol. 1, no. 2, pp. 41–53, Apr. 2023, doi: 10.54066/jikma-itb.v1i2.169.
R. T. Amdani, H. Hafidudin, and M. Iqbal, “Analisis Dan Deteksi Malware Poison Ivy Dengan Metode Malware Analisis Dinamis Dan Malware Analisis Statis,” EProceedings Appl. Sci., vol. 7, no. 2, Apr. 2021, Accessed: Aug. 12, 2025. [Online]. Available: https://openlibrarypublications.telkomuniversity.ac.id/index.php/appliedscience/article/view/14423
G. S. Agung, “Analisis Malware Trojan Dalam File Undangan Pernikahan.Apk Pada Smartphone Android Dengan Metode Hybrid Analysis,” EProceedings Eng., vol. 12, no. 2, pp. 1–6, May 2025.
G. Nenz, T. Kleb, and R. Müller, “Reverse Engineering Labs (Folgearbeit),” other, OST Ostschweizer Fachhochschule, 2023. Accessed: Aug. 12, 2025. [Online]. Available: https://eprints.ost.ch/id/eprint/1140/
T. Sutter, T. Kehrer, M. Rennhard, B. Tellenbach, and J. Klein, “Dynamic Security Analysis on Android: A Systematic Literature Review,” IEEE Access, vol. 12, pp. 57261–57287, 2024, doi: 10.1109/ACCESS.2024.3390612.
S. A. Khan et al., “An Android Applications Vulnerability Analysis Using MobSF,” in 2024 International Conference on Engineering & Computing Technologies (ICECT), Islamabad, Pakistan: IEEE, May 2024, pp. 1–7. doi: 10.1109/ICECT61618.2024.10581312.
A. Basak and D. Tiwari, “API security risk and resilience in financial institutions.” Accessed: Aug. 12, 2025. [Online]. Available: http://www.theseus.fi/handle/10024/883344
S. U. Kusreynada and A. S. Barkah, “Android Apps Vulnerability Detection with Static and Dynamic Analysis Approach using MOBSF,” J. Comput. Sci. Eng. JCSE, vol. 5, no. 1, pp. 46–63, Apr. 2024, doi: 10.36596/jcse.v5i1.789.
A. Iftikhar et al., “Quality Assurance in Digital Forensic Investigations: Optimal Strategies and Emerging Innovations,” Austin J. Forensic Sci. Criminol., vol. 10, no. 2, Oct. 2023, doi: 10.26420/AustinJForensicSciCriminol.2023.1097.
A. R. AlMhanawi and B. M. Nema, “Instant Messaging Security: A Comprehensive Review of Behavior Patterns, Methodologies, and Security Protocols,” J. Al-Qadisiyah Comput. Sci. Math., vol. 16, no. 1, Mar. 2024, doi: 10.29304/jqcsm.2024.16.11440.
A. D. Putra, J. D. Santoso, and I. Ardiansyah, “Analisis Malicious Software Trojan Downloader Pada Android Menggunakan Teknik Reverse Engineering (Studi Kasus: Kamus Kesehatan v2.apk),” Build. Inform. Technol. Sci. BITS, vol. 4, no. 1, pp. 69–79, June 2022, doi: 10.47065/bits.v4i1.1515.
Downloads
Published
Issue
Section
License
Copyright (c) 2025 Fariz Maulana Rizki, Mukhlis Prasetyo Aji, Ermadi Satriya Wijaya, Harjono

This work is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License.
Start from 2019 issues, authors who publish with JURNAL MOBILE AND FORENSICS agree to the following terms:
- Authors retain copyright and grant the journal right of first publication with the work simultaneously licensed under a Creative Commons Attribution License (CC BY-SA 4.0) that allows others to share the work with an acknowledgment of the work's authorship and initial publication in this journal.
- Authors are able to enter into separate, additional contractual arrangements for the non-exclusive distribution of the journal's published version of the work (e.g., post it to an institutional repository or publish it in a book), with an acknowledgment of its initial publication in this journal.
- Authors are permitted and encouraged to post their work online (e.g., in institutional repositories or on their website) prior to and during the submission process, as it can lead to productive exchanges, as well as earlier and greater citation of published work.

This work is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License.












 Mobile and Forensics (MF)
Mobile and Forensics (MF)