Security Analysis of Two-Factor Authentication Applications: Vulnerabilities in Data Storage and Management
DOI:
https://doi.org/10.12928/mf.v7i2.13312Keywords:
Application Security, Security Analysis, Encryption, OTP bypass, Two-Factor AuthenticationAbstract
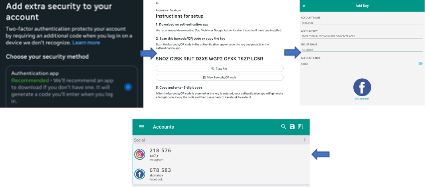
In the digital era, two-factor authentication (2FA) is used as an additional security measure to protect user access to digital services. However, the storage methods of authentication data in 2FA applications have potential security vulnerabilities that can be exploited. This study analyzes five popular 2FA applications, namely Google Authenticator, 2FAS, Aegis Authenticator, Okta Verify, and TOTP Authenticator, focusing on how secret keys are stored and the potential exploitation risks. The experiment was conducted in a virtual Android environment using rooted BlueStacks 5. Data acquisition was performed using Media Manager and X-Plore File Manager, followed by data analysis with SQLite Browser and bypass with PyOTP. The results indicate that some applications store secret keys in plaintext or weak encryption, making authentication bypass possible by manually generating OTP codes. This study concludes that strengthening data storage security in 2FA applications is crucial to prevent unauthorized exploitation by malicious actors.
References
T. Mehra, “The Critical Role of Two-Factor Authentication (2FA) in Mitigating Ransomware and Securing Backup, Recovery, and Storage Systems,” Int. J. Sci. Res. Arch., vol. 14, no. 1, pp. 274–277, 2025. https://doi.org/10.30574/ijsra.2025.14.1.0019
F. P. E. Putra, A. Zulfikri, G. Arifin, R. M. Ilhamsyah, and others, “Analysis of phishing attack trends, impacts and prevention methods: literature study,” Brill. Res. Artif. Intell., vol. 4, no. 1, pp. 413–421, 2024. https://doi.org/10.47709/briliance.v4i1.4357
D. Patel, D. Trivedi, U. Raval, and A. Dennisan, “2F-Authsys: A hyperlocal two-factor authentication system using Near Sound Data Transfer,” J. Appl. Res. Technol., vol. 22, no. 2, pp. 197–205, 2024. https://doi.org/10.22201/icat.24486736e.2024.22.2.2244
M. R. Suresh, K. Balachander, S. L. Varman, and K. S. S. Faris, “Two Factor Authentication by Using Decentralized File Storage System,” 2024. https://doi.org/10.21203/rs.3.rs-4316141/v1
T. Taffese, F. Chavez, A. Fernandez-Reyes, and M. Byrne, “Redesigning and evaluating interfaces for two-factor authentication: performance of younger and older adults,” 2025, doi: 10.31234/osf.io/vtx7u_v1.
M. Az, S. F. Pane, and R. M. Awangga, “Cryptography: Perancangan Middleware Web Service Encryptor menggunakan Triple Key MD5. Base64, dan AES,” J. Tekno Insentif, vol. 15, no. 2, pp. 65–75, 2021. https://doi.org/10.36787/jti.v15i1.497
K. Liu et al., “A robust and effective two-factor authentication (2FA) protocol based on ECC for mobile computing,” Appl. Sci., vol. 13, no. 7, p. 4425, 2023.
https://doi.org/10.3390/app13074425
M. D. Tomić and O. M. Radojević, “Implementation of two-factor user authentication in computer systems,” Vojnoteh. Glas. Tech. Cour., vol. 72, no. 1, pp. 170–191, 2024.
https://doi.org/10.5937/vojtehg72-48081
C. Cornelius and T. Simon, “Investigate and Evaluate the Security Measures Commonly Used in Electronic Banking Transactions in Zambia and Possible Solutions,” Int. Res. J. Mod. Eng. Technol. Sci., vol. 5, pp. 9077–9082, 2023.
https://www.doi.org/10.56726/IRJMETS41115
B. D. Kurniawan, M. A. Rosid, I. A. Kautsar, and N. E. Pratama, “Rancang Bangun Library Web Token untuk Enkripsi HTTP Data Menggunakan Eksklusif-OR (XOR),” Phys. Sci. Life Sci. Eng., vol. 1, no. 1, p. 14, 2023. https://doi.org/10.47134/pslse.v1i1.164
B. Anwar, R. Kustini, and I. Zulkarnain, “Penerapan Algoritma RSA (Rivest Shamir Adelman) Untuk Mengamankan Nilai Siswa SMP HKBP P. Bulan,” J. Teknol. Sist. Inf. dan Sist. Komput. TGD, vol. 4, no. 1, pp. 88–91, 2021. https://doi.org/10.53513/jsk.v4i1.2623
Y. Sun, S. Zhu, Y. Zhao, and P. Sun, “Let Your Camera See for You: A Novel Two-Factor Authentication Method against Real-Time Phishing Attacks,” arXiv Prepr. arXiv2109.00132, 2021. https://doi.org/10.48550/arXiv.2109.00132
J. Haddad, N. Pitropakis, C. Chrysoulas, M. Lemoudden, and W. J. Buchanan, “Attacking Windows Hello for Business: Is It What We Were Promised?,” Cryptography, vol. 7, no. 1, p. 9, 2023. https://doi.org/10.3390/cryptography7010009
A. Aldahmani, B. Ouni, T. Lestable, and M. Debbah, “Cyber-Security of Embedded IoTs in Smart Homes: Challenges, Requirements, Countermeasures, and Trends. IEEE Open Journal of Vehicular Technology, 4, 281-292.” 2023. https://doi.org/10.1109/OJVT.2023.3234069
S. J. Murdoch and A. Abadi, “A Forward-secure Efficient Two-factor Authentication Protocol,” arXiv Prepr. arXiv2208.02877, 2022. https://doi.org/10.48550/arXiv.2208.02877
E. Ahmadieh and N. El Madhoun, “Comparative E-Voting Security Evaluation: Multi-Modal Authentication Approaches,” in 2024 6th International Conference on Blockchain Computing and Applications (BCCA), 2024, pp. 250–254.
https://doi.org/10.1109/BCCA62388.2024.10844450
A. Sofian et al., “Enhancing authentication security: analyzing time-based one-time password systems,” Int. J. Comput. Technol. Sci., vol. 1, no. 3, pp. 56–70, 2024, doi: 10.62951/ijcts.v1i3.25. https://doi.org/10.62951/ijcts.v1i3.25
R. O. Okeke and S. O. Orimadike, “Enhanced Cloud Computing Security Using Application-Based Multi-Factor Authentication (MFA) for Communication Systems,” Eur. J. Electr. Eng. Comput. Sci., vol. 8, no. 2, pp. 1–8, 2024. https://doi.org/10.24018/ejece.2024.8.2.593
J. Berrios, E. Mosher, S. Benzo, C. Grajeda, and I. Baggili, “Factorizing 2FA: Forensic analysis of two-factor authentication applications,” Forensic Sci. Int. Digit. Investig., vol. 45, p. 301569, 2023, doi: 10.1016/j.fsidi.2023.301569.
S. Pane and D. J. W. Ikram, “Deteksi Spam Bot Pada Komentar Youtube: Tinjauan Literatur Sistematis,” Comput. Sci. Res. Its Dev. J., vol. 15, no. 2, pp. 103–123, 2023. https://www.doi.org/10.22303/csrid.15.2.2022.103-123
Downloads
Published
Issue
Section
License
Copyright (c) 2025 Syafrial Fachri Pane, Dzikri Izzatul Haq, M. Amran Hakim Siregar

This work is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License.
Start from 2019 issues, authors who publish with JURNAL MOBILE AND FORENSICS agree to the following terms:
- Authors retain copyright and grant the journal right of first publication with the work simultaneously licensed under a Creative Commons Attribution License (CC BY-SA 4.0) that allows others to share the work with an acknowledgment of the work's authorship and initial publication in this journal.
- Authors are able to enter into separate, additional contractual arrangements for the non-exclusive distribution of the journal's published version of the work (e.g., post it to an institutional repository or publish it in a book), with an acknowledgment of its initial publication in this journal.
- Authors are permitted and encouraged to post their work online (e.g., in institutional repositories or on their website) prior to and during the submission process, as it can lead to productive exchanges, as well as earlier and greater citation of published work.

This work is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License.












 Mobile and Forensics (MF)
Mobile and Forensics (MF)