Analisis Bukti Digital pada Storage Secure Digital Card Menggunakan Metode Static Forensic
DOI:
https://doi.org/10.12928/mf.v1i2.1217Abstract
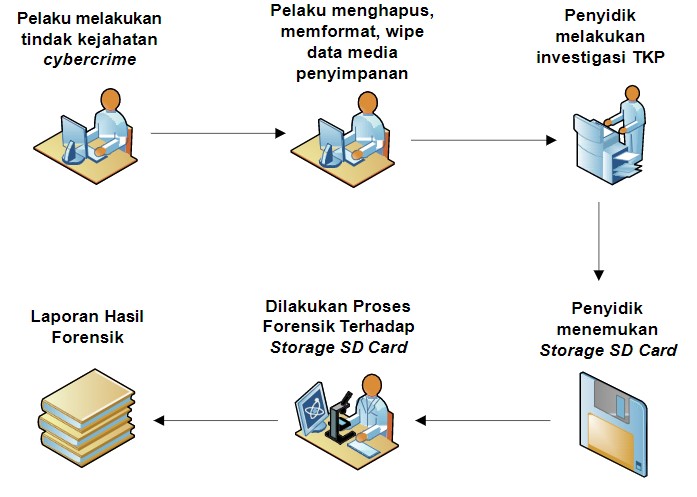
Secure Digital Card (SD Card) merupakan salah satu media untuk mendapatkan bukti digital dalam proses penyelidikan suatu kasus cybercrime. Oleh kerena itu, perlu adanya penelitian tentang analisa bukti digital pada media penyimpanan SD Card. Penelitian ini membahas tentang proses eksaminasi dan analisis bukti digital yang terdapat pada media penyimpanan SD Card yang bertujuan untuk membantu proses penyelidikan kasus cybercrime. Proses penelitian menggunakan tools forensic FTK Imager dan Autopsy serta menggunakan metode forensic static dimana barang bukti eletronik diproses secara bit-by-bit image dalam melakukan proses forensik. Hasil dari penelitian ini adalah barang bukti yang berupa SD Card dilakukan proses examinasi dan recovery data yang hilang, data yang berhasil di recovery dibedakan berdasarkan cara pelaku menghapus datanya. Data yang didapatkan pada SD Card dapat dijadikan sebagai barang bukti pada proses persidangan kasus cybercrime.
References
Al Anhar, A., Satrya, G. B., & Yulianto, F. A. (2014). Analisis Perbandingan Keamanan Teknik Penghapusan Data pada Hardisk dengan Metode DoD 5220 . 22 dan Gutmann Comparative Analysis of Data Deletion Technique Security on Hard disk with DoD 5220 . 22 and Gutmann Method. 1(1), 607-613.
Faiz, M. N., Umar, R., & Yudhana, A. (2017). Implementasi Live Forensics untuk Perbandingan Browser pada Keamanan Email. JISKA (Jurnal Informatika Sunan Kalijaga), 1(3), 108. https://doi.org/10.14421/jiska.2017.13-02
Fauzan, A., Riadi, I., & Fadlil, A. (2017). Analisis Forensik Digital Pada Line Messenger Untuk Penanganan Cybercrime. Annual Research Seminar (ARS), 2(1), 159-163. Retrieved from http:// seminar.ilkom.unsri.ac.id/ index.php/ars/article/view/832/752
Hartono, R. (2013). Perancangan Sistem Data Logger Temperatur Baterai Berbasis Arduino Duemilanove. Retrieved from http:// chemistrahmah.com/ caramenulisdaftarpustaka.%5Cnhtml
Institute of Justice, N. (2001). Special REPORT Electronic Crime Scene Investigation: A Guide for First Responders, Second Edition. Retrieved from www.ojp.usdoj.gov/nij
Khalifa, H. R., Yulianto, F. A., Jadied, E. M., Informatika, S. T., Informatika, F., & Telkom, U. (2016). Implementasi Teknik Penghapusan Data Dengan Metode DoD 5220 . 22M Pada Sistem Operasi Android Implementation Of Data Deletion Using DoD 5220 . 22M method On Android Operating System. 3(1), 897-913.
Kunang, Y. N., & Khristian, A. (2016). Implementasi Prosedur Forensik untuk Analisis Artefak Whatsapp pada Ponsel Android. 2(1), 59-68. Retrieved from http://ars.ilkom.unsri.ac.id
Kurniawan, H. (2011). Keamanan jaringan dengan komputer forensik. Computer Science Research and Its Development Journal, Vol.3(3), 175-184.
Ramadhan, R. A., Prayudi, Y., & Sugiantoro, B. (2017). Implementasi dan Analisis Forensika Digital Pada Fitur Trim Solid State Drive (SSD). Teknomatika, 9(2), 1-13. Retrieved from http:// teknomatika.stmikayani.ac.id/wp-content/uploads/2017/07/1.pdf
Riadi, I., Umar, R., & Nasrulloh, I. M. (2018). Analisis Forensik Digital Pada Frozen Solid State Drive Dengan Metode National Institute of Justice (Nij). 3(1), 70-82. https://doi.org/10.21831/elinvo.v3i1.19308
Riadi, I., Umar, R., & Sukarno, W. (2016). Analisis Forensik Serangan Sql Injection Menggunakan Metode Statis Forensik. Prosiding Interdisciplinary Postgraduate Student Conference 1st, I(I), 102-103.
Rosalina, V., Suhendarsah, A., & Natsir, M. (2016). Analisis Data Recovery Menggunakan Software Forensic : Winhex and X-Ways Forensic. Jurnal Pengembangan Riset Dan Observasi Sistem Komputer, 3(1), 51-55.
Ruci Meiyanti, & Ismaniah. (2015). Perkembangan Digital Forensik. Jurnal Kajian Ilmial UBJ, 15(September 2015).
Ruuhwan, R., Riadi, I., & Prayudi, Y. (2016a). Analisis Kelayakan Integrated Digital Forensics Investigation Framework Untuk Investigasi Smartphone. Jurnal Buana Informatika, 7(4). https://doi.org/10.24002/jbi.v7i4.767
Ruuhwan, R., Riadi, I., & Prayudi, Y. (2016b). Penerapan Integrated Digital Forensic Investigation Framework v2 (IDFIF) pada Proses Investigasi Smartphone. Jurnal Edukasi Dan Penelitian Informatika (JEPIN), 2(1). https://doi.org/10.26418/jp.v2i1.14369
Umar, R., Yudhana, A., & Faiz, M. N. (2018). Experimental analysis of web browser sessions using live forensics method. International Journal of Electrical and Computer Engineering, 8(5), 2951-2958. https://doi.org/10.11591/ijece.v8i5.pp.2951-2958
Yudhana, A., Riadi, I., & Ridho, F. (2018). DDoS classification using neural network and naive bayes methods for network forensics. International Journal of Advanced Computer Science and Applications, 9(11), 177-183. https://doi.org/10.14569/ijacsa.2018.091125
Downloads
Additional Files
Published
Issue
Section
License
Copyright (c) 2019 Muh Fadli Hasa, Anton Yudhana, Abdul Fadlil

This work is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License.
Start from 2019 issues, authors who publish with JURNAL MOBILE AND FORENSICS agree to the following terms:
- Authors retain copyright and grant the journal right of first publication with the work simultaneously licensed under a Creative Commons Attribution License (CC BY-SA 4.0) that allows others to share the work with an acknowledgment of the work's authorship and initial publication in this journal.
- Authors are able to enter into separate, additional contractual arrangements for the non-exclusive distribution of the journal's published version of the work (e.g., post it to an institutional repository or publish it in a book), with an acknowledgment of its initial publication in this journal.
- Authors are permitted and encouraged to post their work online (e.g., in institutional repositories or on their website) prior to and during the submission process, as it can lead to productive exchanges, as well as earlier and greater citation of published work.

This work is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License.












 Mobile and Forensics (MF)
Mobile and Forensics (MF)