Network Security Monitoring System via Android Mobile App With IDS
DOI:
https://doi.org/10.12928/mf.v6i1.10317Keywords:
Android, Intrusion Detection System , Network Security, Monitoring System, SnortAbstract
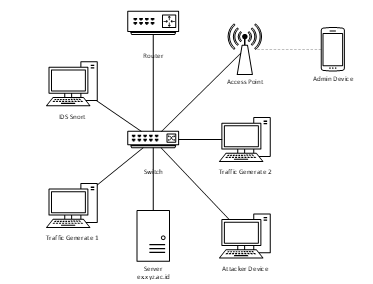
Network security is an important factor in securing data on a server, so a server needs to be kept safe from things that could threaten the validity and integrity of stored data. One way that can be used to detect threats on a server is implementing an Intrusion detection system on the server. A literature study conducted on research that implemented intrusion detection systems, found that there was a lack of intrusion detection system research that could detect one type of network security attack with a variety of attack variables and it was also found in research that had successfully implemented an intrusion detection system to detect network security attacks but still incorrectly identifying the type of attack. This research uses the Snort intrusion detection system method with an experimental model of an attack detection system and an Android application which is applied to monitor the statistics of attacks detected on the Xyz University network. The research results showed that the rules created on the IDS can detect network security attacks, especially DoS/DDoS and PortScan attacks. Then an IDS was created that can send application alert notifications and SMS with a response time that is quite responsive based on the NIST Cybersecurity reference with an average of 22 seconds for DoS/DDoS attacks and 21 seconds for Port Scanning attacks. For the percentage results from 3 times testing the rule by sending DoS/DDoS attack packets of 309,462 to 1,459,548, getting a high level of accuracy with an average of 92.1% on first test, 91.7% on the second test and 91.5% on the third test. In the results of testing the PortScan rule by sending 1,001 to 10,564 attack packets, a high level of accuracy was obtained with an average result of 92.2% in the first test, 94.2% in the second test and 93.4% in the third test.
References
M. Ardhiansyah, S. Noris, and R. Andrianto, Jaringan Komputer Jaringan Komputer, 1st ed. Banten: Unpam Press, 2020. [Online]. Available: http://eprints.unpam.ac.id/8869/1/TPL0183_JARINGAN KOMPUTER-ok.pdf
I. Sofana, “No Title,” Membangun Jaringan Komputer: Mudah membuat Jaringan Komputer (Wire & Wireless) untuk pengguna Windows dan Linux, 2013.
M. Wills, “Information Security Fundamentals,” in (ISC)2 SSCP Systems Security Certified Practitioner Official Study Guide, Wiley, 2019, pp. 25–49. doi: 10.1002/9781119547921.ch2.
A. Sadiqui, “Fundamentals of Network Security,” in Computer Network Security, Wiley, 2020, pp. 1–14. doi: 10.1002/9781119706762.ch1.
R. Widodo and I. Riadi, “Sistem Deteksi Penyusup Pada Jaringan Komputer Menggunakan Teknik Host Based Intrusion Detection System,” Buletin Ilmiah Sarjana Teknik Elektro, 2019.
J. Wang and Z. A. Kissel, “Intrusion Detections,” in Introduction to Network Security: Theory and Practice, Wiley, 2015, pp. 309–336. doi: 10.1002/9781119113102.ch9.
H. Yanto and F. Hadi, “Intruder Detection Monitoring System in Computer Networks Using Snort Based Sms Alert (Sistem Monitoring Deteksi Penyusup Dalam Jaringan Komputer Menggunakan Snort Berbasis Sms Alert),” Jurnal KomtekInfo, vol. 7, no. 2, pp. 159–170, 2020, doi: 10.35134/komtekinfo.v7i2.76.
N. Christianto and W. Sulistyo, “Model Pemantauan Keamanan Jaringan Melalui Aplikasi Telegram Dengan Snort,” Jurnal Teknik Informatika dan Sistem Informasi, vol. 7, pp. 2443–2229, 2021, doi: 10.28932/jutisi.v7i1.4088.
J. V. M. Edy Irwansyah, Pengantar teknologi informasi, 1st ed. Yogyakarta, 2014.
M. Irsan, T. Jl, H. Hadari, and N. Pontianak, “RANCANG BANGUN APLIKASI MOBILE NOTIFIKASI BERBASIS ANDROID UNTUK MENDUKUNG KINERJA DI INSTANSI PEMERINTAHAN.”
M. Dooley and T. Rooney, “Service Denial Attacks,” in DNS Security Management, 1st ed., Wiley, 2017, pp. 139–141. doi: 10.1002/9781119328292.ch7.
V. Trola, “Manual Network Exploration,” in Hunting Cyber Criminals, 1st ed., Wiley, 2020, pp. 45–65. doi: 10.1002/9781119541004.ch3.
W. W. Purba and R. Efendi, “Perancangan dan analisis sistem keamanan jaringan komputer menggunakan SNORT,” AITI: Jurnal Teknologi Informasi, vol. 17, no. Agustus, pp. 143–158, 2020.
A. F. Mutaqin, “Rancang Bangung Sistem Monitoring Jaringan Prodi Teknik Informatika Melalui SMS Alert dengan Snort,” Jurnal Sistem dan Teknologi Informasi (JUSTIN), vol. 1, No. 1, 2016.
Downloads
Published
Issue
Section
License
Copyright (c) 2024 Hamas Prasetyo, Nuril Anwar

This work is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License.
Start from 2019 issues, authors who publish with JURNAL MOBILE AND FORENSICS agree to the following terms:
- Authors retain copyright and grant the journal right of first publication with the work simultaneously licensed under a Creative Commons Attribution License (CC BY-SA 4.0) that allows others to share the work with an acknowledgment of the work's authorship and initial publication in this journal.
- Authors are able to enter into separate, additional contractual arrangements for the non-exclusive distribution of the journal's published version of the work (e.g., post it to an institutional repository or publish it in a book), with an acknowledgment of its initial publication in this journal.
- Authors are permitted and encouraged to post their work online (e.g., in institutional repositories or on their website) prior to and during the submission process, as it can lead to productive exchanges, as well as earlier and greater citation of published work.

This work is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License.












 Mobile and Forensics (MF)
Mobile and Forensics (MF)