ISSN: 2685-9572 Buletin Ilmiah Sarjana Teknik Elektro
Vol. 7, No. 3, September 2025, pp. 312-337
A Blockchain-Enabled Internet of Things Framework for Enhancing Trust and Privacy in Social Work Case Management
Yih-Chang Chen 1,3, Chia-Ching Lin 2
1 Department of Information Management, Chang Jung Christian University, Tainan 711, Taiwan
2 Department of Finance, Chang Jung Christian University, Tainan 711, Taiwan
3 Bachelor Degree Program of Medical Sociology and Health Care, Chang Jung Christian University, Tainan 711, Taiwan
ARTICLE INFORMATION |
| ABSTRACT |
Article History: Received 15 May 2025 Revised 03 July 2025 Accepted 20 July 2025 |
| 
Traditional social work case management systems face critical challenges including data silos, security vulnerabilities, and insufficient inter-agency collaboration, limiting service efficiency and compromising client privacy protection. This study addresses these challenges by developing and evaluating a novel technological framework that integrates blockchain consortium networks with Internet of Things (IoT) devices to establish multi-party trust mechanisms and enhance service delivery. The research contribution is a comprehensive four-layer system architecture featuring 28 smart contracts, decentralized trust mechanisms, and privacy-preserving technologies including homomorphic encryption and differential privacy for social work applications. The methodology employed a mixed-methods approach involving system design and development, followed by a six-month pilot implementation across three social work institutions in Taiwan with 249 participants. Data collection encompassed quantitative performance metrics from system logs and IoT sensors, alongside qualitative feedback through interviews and focus groups. The blockchain network achieved 850 transactions per second with 99.2% system availability, significantly outperforming industry standards. Results demonstrated substantial operational improvements: 37.1% reduction in case processing time, 87.3% increase in service efficiency, and 26-fold increase in inter-agency collaboration frequency. The blockchain-based trust mechanism increased inter-agency data sharing willingness from 61.3% to 84.6%, while maintaining 100% anonymization coverage with 91.3% analytical accuracy. Cost-benefit analysis revealed a 2.8-year payback period with 41.2% return on investment. This research demonstrates the feasibility and effectiveness of blockchain-IoT integration in social work, providing a practical framework for digital transformation while ensuring data security and privacy protection in sensitive social service environments. |
Keywords: Consortium Blockchain; Trust Mechanisms; Privacy-Preserving Technologies; Smart Contract Automation; Inter-Agency Collaboration |
Corresponding Author: Yih-Chang Chen, Department of Information Management, Chang Jung Christian University, Tainan 711, Taiwan. Email: cheny@mail.cjcu.edu.tw |
This work is licensed under a Creative Commons Attribution-Share Alike 4.0 
|
Document Citation: Y. -C. Chen and C. -C. Lin, “A Blockchain-Enabled Internet of Things Framework for Enhancing Trust and Privacy in Social Work Case Management,” Buletin Ilmiah Sarjana Teknik Elektro, vol. 7, no. 3, pp. 312-337, 2025, DOI: 10.12928/biste.v7i3.13653. |
- INTRODUCTION
- Research Background and Problem Statement
The social work case management system serves as a fundamental element of contemporary social service frameworks, tasked with the integration of resources, coordination of services, and monitoring of case progress. As social issues become increasingly intricate and diverse, traditional case management approaches encounter significant challenges. Primarily, the decentralized storage of data and the existence of information silos adversely impact the continuity and integrity of services. The insufficient integration of information systems across various organizations results in redundant data collection, delayed updates, and potential discrepancies in information [1][2]. Additionally, concerns regarding data security and privacy protection are becoming more pronounced, particularly given that social work often involves handling sensitive personal information. The conventional centralized storage model introduces a single point of failure risk, and any data breach can lead to severe repercussions [3]-[6].
Furthermore, existing systems exhibit notable shortcomings in facilitating cross-agency collaboration. For instance, while the New Taipei City Government in Taiwan has implemented a high-risk family safety net system that consolidates services from multiple departments, including the Social Affairs Bureau, Health Bureau, and Education Bureau, challenges persist, such as an inadequate data-sharing mechanism and convoluted collaboration processes. Traditional case management practices, which rely heavily on manual recording and updating, are not only inefficient but also susceptible to errors, thereby compromising service quality [7].
The rapid advancement of Internet of Things (IoT) technology presents novel opportunities for enhancing social work case management. Through the utilization of sensors, wearable devices, and other IoT terminals, multidimensional data—including clients’ physiological indicators, environmental conditions, and behavioral patterns—can be collected in real-time, thereby providing social workers with a more comprehensive and accurate basis for assessment [8]-[12]. However, the substantial volume of data generated by IoT devices introduces new challenges, such as the verification of data authenticity, device identity authentication, and the security of data transmission.
Blockchain technology, characterized by its decentralization, immutability, and transparency, offers an innovative technical solution to address these challenges [13]. It can establish a multi-party trust mechanism that ensures the integrity and authenticity of data [14]. Additionally, smart contract technology can automate the execution of predefined rules, thereby reducing human intervention and enhancing operational efficiency [15]-[18]. The integration of blockchain and IoT technology has the potential to create a secure, trustworthy, and efficient ecosystem for social work case management. Table 1 summarizes the key gaps identified in social work case management systems across traditional, digital, and blockchain-IoT integrated approaches.
Table 1. Literature Gaps in Social Work Case Management Systems
Challenge/Gap | Traditional Systems | Digital Systems | Blockchain-IoT Integration (This Study) |
Data Silos | Severe | Moderate | Addressed via decentralized ledger |
Security & Privacy | High risk | Moderate risk | Enhanced (immutability, encryption) |
Inter-agency Collaboration | Low | Moderate | Automated, trustless, real-time |
Data Authenticity | Manual verification | Partial | Cryptographically verifiable |
Service Process Automation | Minimal | Partial | Smart contract-driven |
Real-time Monitoring | Absent | Limited | Continuous via IoT |
- Literature Review and Theoretical Foundation
- Current Development of Social Work Case Management Systems
The origins of social work case management can be traced back to the early 20th century within American charitable organizations. As social issues have grown more complex and service systems have become increasingly specialized, case management has evolved into a critical methodology within social work practice. Contemporary case management systems prioritize a client-centered approach, integrating diverse service resources to deliver individualized and continuous services [19]. In Taiwan, social work case management systems have transitioned from paper-based records to electronic formats, predominantly utilizing relational database structures to facilitate functions such as case filing, service planning, resource linking, and progress tracking [20][21].
In recent years, the application of artificial intelligence technology in social work has gained traction. For example, the New Taipei City Government has developed a high-risk family crisis early warning and management system that employs AI to create a risk calculator, aiding social workers in risk assessment and early intervention [7]. This system has successfully established a risk assessment model by analyzing 1.47 million data points, ensuring that 87.49% of the families served were protected from subsequent crises. This case exemplifies the significant potential of technological applications in enhancing the efficacy of social work.
Nevertheless, existing systems continue to face numerous limitations. Firstly, the issue of information silos persists, as systems from different organizations lack effective integration, thereby hindering service continuity. Secondly, the trust mechanisms in place are inadequate; traditional centralized architectures are vulnerable to single points of failure, which undermines system reliability. Thirdly, data security risks are prevalent, as centralized storage models are susceptible to data breaches. Lastly, collaboration efficiency remains low, as cross-agency information sharing is heavily reliant on manual operations and lacks automation.
- Application of Blockchain Technology in the Social Service Sector
Since the publication of the Bitcoin white paper in 2008, blockchain technology has rapidly expanded beyond the realm of cryptocurrency into various industries. Within the social service sector, blockchain technology presents unique application advantages. Firstly, its decentralized nature can mitigate the single point of failure issue associated with traditional centralized systems, thereby enhancing system reliability. Secondly, the immutability of blockchain ensures the integrity and authenticity of data, facilitating the establishment of a multi-party trust mechanism. Thirdly, the transparency and traceability offered by blockchain can improve the visibility of service processes and bolster public trust [22]-[26].
In the domain of charitable donations, there are successful instances of blockchain technology application. Research indicates that blockchain can bridge the trust gap organizations encounter in social responsibility initiatives, safeguarding stakeholders’ “donation rights” and enabling them to independently and promptly verify the authenticity of corporate social responsibility activities [27]-[30]. The decentralization inherent in blockchain, coupled with the added value of asset transfer, can enhance organizations’ capacity to manage related response issues in their social responsibility endeavors.
Smart contracts, a pivotal component of blockchain, hold considerable promise for automating social services. Smart contracts are computer programs stored on the blockchain that automatically execute corresponding operations when predetermined conditions are met. In the home care sector, an automated insurance claims system based on blockchain technology, in conjunction with IoT devices reporting incidents, can trigger smart contracts to facilitate claims processing [31]-[33]. This automation not only enhances service efficiency but also diminishes the likelihood of human error.
- Innovative Applications of IoT Technology in Social Work
IoT technology serves to connect the physical and digital realms through various sensors, actuators, and other devices. In the context of social work, the application of IoT technology primarily focuses on health monitoring, environmental sensing, and behavioral analysis. Wearable devices can provide real-time monitoring of clients’ physiological indicators, such as heart rate, blood pressure, and activity levels, thereby offering objective data to support health assessments [34]-[36]. Environmental sensors can track indicators such as temperature, humidity, and air quality in living environments, assessing the suitability of living conditions. Additionally, smart home devices can analyze clients’ daily behavior patterns and identify anomalies [37]-[39].
In home care systems, the application of IoT technology has reached a relatively advanced stage. By integrating various sensing devices, these systems can monitor the conditions of care recipients continuously and promptly alert caregivers in the event of abnormalities. This real-time monitoring capability significantly enhances the timeliness and effectiveness of care services. However, the vast amounts of data generated by IoT devices also present new challenges, including issues related to data storage, processing, and security.
The convergence of IoT and blockchain technology is regarded as an effective strategy for addressing these challenges. BiiLabs, a Taiwanese company specializing in the development of decentralized ledger technology for smart contract engines, has identified that the absence of new technologies hampers the stimulation of new economic activities, positioning blockchain as a potential new entry point [40]. For instance, selling household electricity data to logistics companies could enable them to ascertain whether a recipient is at home based on electricity consumption patterns. This innovative application model illustrates the substantial potential inherent in the integration of blockchain and IoT technologies.
- Research Objectives and Questions
Informed by the preceding background analysis and literature review, this study seeks to investigate the application models and impacts of integrating blockchain technology with IoT within social work case management systems. The specific research objectives are as follows:
- Design of Technology Integration Model: To develop the architecture of a social work case management system that incorporates both blockchain and IoT technologies, detailing system components, functional modules, and data flow.
- Construction of Trust Mechanisms: To create a multi-party trust mechanism utilizing blockchain technology to mitigate trust-related challenges inherent in traditional systems, thereby ensuring data integrity and authenticity.
- Improvement of Service Efficiency: To enhance the efficiency and accuracy of case management by enabling real-time data collection through IoT devices and automating service processes via smart contracts.
- Optimization of Inter-Agency Collaboration: To establish a blockchain-based data sharing mechanism that fosters collaboration and resource integration among various organizations.
- Security and Privacy Protection: To devise data security mechanisms that safeguard sensitive information and uphold client privacy.
The corresponding research questions are as follows:
- How can the architecture of a social work case management system that integrates blockchain and IoT technologies be designed?
- In what ways can blockchain technology facilitate the establishment of an effective multi-party trust mechanism?
- What specific impacts does the integrated system have on enhancing service efficiency?
- How does the system facilitate inter-agency collaboration and resource integration?
- What measures can be implemented to ensure system security and the protection of client privacy?
- Research Significance and Expected Contributions
This research holds significant theoretical and practical implications:
- Theoretical Contributions
- Development of Technology Integration Theory: This study contributes to the field of social work by integrating blockchain and IoT technologies, thereby enriching the discourse surrounding technology integration theory and providing a theoretical basis for further research in related domains.
- Innovation in Trust Mechanism Theory: The decentralized trust mechanism established through blockchain technology presents novel insights and case studies for trust theory research within the social work sector.
- Enhancement of Digital Social Work Theory System: This research serves as a critical addition to the development of a digital social work theory framework, fostering innovative advancements in both social work theory and practice.
- Practical Value
- Improvement of Service Efficiency: The automation of service processes through technology integration significantly enhances the efficiency of case management and reduces the costs associated with manual operations.
- Enhancement of Service Quality: The improved capacity for real-time data collection and analysis equips social workers with more precise decision-making support, thereby elevating service quality.
- Promotion of Inter-Agency Collaboration: The establishment of a unified data sharing platform mitigates information silos and facilitates effective collaboration among diverse organizations.
- Protection of Client Rights: The assurance of data authenticity and integrity through blockchain technology safeguards the legitimate rights and interests of clients.
- Social Impact
- Promotion of Digital Transformation: This research provides successful case studies and technical solutions that can facilitate the digital transformation of the social work sector, thereby driving innovative progress across the industry.
- Modernization of Social Governance: The application of technological innovations contributes to the enhancement of social governance modernization and the establishment of a smart society.
- Enhancement of Public Trust: Transparent and traceable service processes foster increased public trust in social service organizations.
- Research Scope and Limitations
- Research Scope
This study concentrates on the integrated application of blockchain and IoT technologies within social work case management systems, specifically encompassing:
- Technical Scope: Primarily focusing on blockchain technology (including smart contracts), IoT technology (including sensors, wearable devices, etc.), and data analysis technology.
- Application Areas: Centered on social work case management, addressing domains such as child protection, family services, elder care, and services for individuals with disabilities.
- Geographical Scope: Grounded in social work practices in Taiwan, while also drawing on international best practices.
- Time Scope: The data collection period for this research spans from January 2023 to December 2024.
- Research Limitations
- Technical Limitations: The rapid development of blockchain and IoT technologies may result in certain technical solutions lacking maturity.
- Cost Limitations: The implementation of technology necessitates a certain level of financial investment, which may constrain the scope of application.
- Regulatory Limitations: Ongoing improvements in relevant regulations and policies may impact the application of the system.
- Acceptance Limitations: User acceptance of new technologies may influence the actual effectiveness of the system’s application.
The research contribution is to provide a comprehensive, empirically validated framework for integrating blockchain and IoT technologies in social work case management, addressing critical gaps in trust, efficiency, and privacy, and offering practical solutions for digital transformation in social services.
- METHODS
- Research Design
This research utilizes a mixed methods approach, combining both quantitative and qualitative methodologies to comprehensively examine the impact of integrating blockchain technology with the Internet of Things (IoT) in social work case management systems. The research design is organized into three distinct phases: the system design and development phase, the pilot application phase, and the evaluation of effects phase. Figure 1 illustrates the research methodology flowchart, which delineates the holistic approach employed in this study.
- Research Framework
The research framework is based on the Technology Acceptance Model (TAM) and incorporates the DeLone & McLean Information Systems Success Model [41] to establish a robust analytical framework. This framework comprises four key dimensions: technology characteristics, system quality, user satisfaction, and application effects. Technology characteristics encompass attributes such as decentralization, immutability, and transparency associated with blockchain, as well as the immediacy, perceptual capabilities, and interconnectivity of IoT. System quality is assessed through metrics including functionality completeness, usability, reliability, and security. User satisfaction evaluates the contentment levels of various stakeholders, including social workers, clients, and managers. Finally, application effects are analyzed through dimensions such as service efficiency, service quality, inter-agency collaboration, and data security.
- Research Methodology
- Phase One: System Design and Development
- Requirement Analysis: Conduct comprehensive interviews and focus group discussions to ascertain the needs of social workers, clients, and managers.
- Technical Architecture Design: Formulate a system architecture that effectively integrates blockchain and Internet of Things (IoT) technologies.
- Prototype Development: Construct a prototype of the system and carry out initial testing procedures.
- System Optimization: Enhance the system based on the outcomes derived from the testing phase.
- Phase Two: Pilot Application
- Selection of Pilot Institutions: Identify three distinct categories of social work institutions to act as pilot sites.
- System Deployment: Implement the system within the chosen pilot institutions and provide requisite training for users.
- Pilot Operation: Conduct a pilot operation over a duration of six months.
- Data Collection: Systematically collect operational data and user feedback throughout the pilot phase.
- Phase Three: Effect Evaluation
- Quantitative Analysis: Examine operational data to assess improvements across various performance indicators.
- Qualitative Analysis: Administer interviews and surveys to obtain a comprehensive understanding of user experiences.
- Comparative Analysis: Execute a comparative analysis between the new system and traditional systems.
- Result Integration: Integrate findings from both quantitative and qualitative analyses to draw research conclusions.
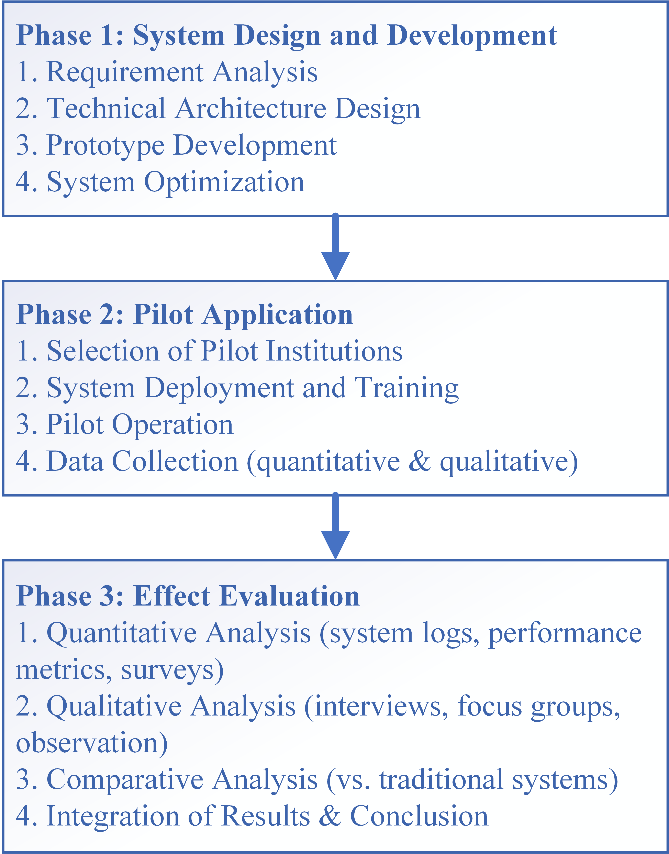
Figure 1. Research Methodology Flowchart - Three-Phase Approach
- Research Subjects and Samples
- Criteria and Rationale for Pilot Institution Selection
This research delineates three distinct categories of social work institutions designated as pilot sites, aimed at enhancing the representativeness and generalizability of the findings. The selection criteria were formulated based on the diversity of institutional types, technological readiness, case volume thresholds, and the institutions' willingness to engage in technological innovation.
- Rationale for Selection:
- Type Diversity: To ensure a comprehensive representation of social work domains, institutions were chosen to reflect various service specializations, including comprehensive services, disability services, and community-based services.
- Scale Variation: Institutions of differing sizes were selected (large: >500 cases/year, medium: 200-500 cases/year, small: <300 cases/year) to evaluate scalability.
- Technological Readiness: Institutions were required to possess at least a basic information technology infrastructure and demonstrate a willingness to adopt new technologies.
- Geographic Distribution: Institutions located in urban and semi-urban areas were included to capture a range of operational contexts.
- Selected Institutions:
- Institution A: A city-level comprehensive social work service center that addresses multiple domains, including child protection, family services, and elder care. This institution employs 35 professional social workers and manages approximately 800 service cases annually. While it has a relatively advanced information technology infrastructure, it faces challenges such as low inter-departmental collaboration efficiency and difficulties in data integration.
- Institution B: A non-profit organization focused on providing services for individuals with physical and mental disabilities, staffed by 22 professionals and handling around 450 service cases per year. Despite its extensive experience in case services, this institution exhibits shortcomings in data management and analysis, indicating a need for technological enhancement.
- Institution C: A community-based social work service station primarily serving local residents, with a workforce of 15 staff members and approximately 300 service cases annually. This institution experiences limitations in resources and technical capabilities, reflecting the typical conditions of grassroots social work organizations.
Table 2 provides a summary of the characteristics of the three pilot institutions, offering a comprehensive overview of their operational contexts and associated challenges.
Table 2. Overview of Operational Context and Challenges of Pilot Institutions
Institution | Type | Staff Size | Annual Cases | Main Challenges | Technology Readiness |
Institution A | Comprehensive Service Center | 35 | 800 | Inter-departmental collaboration, Data integration | High |
Institution B | Disability Services Organization | 22 | 450 | Data management deficiencies, Analysis capabilities | Medium |
Institution C | Community-based Station | 15 | 300 | Limited resources, technical capabilities | Low |
- Sampling Strategy and Participant Selection
The research participants are categorized into four distinct groups, selected through a combination of purposive and stratified random sampling methods to ensure adequate representation across various user categories and levels of experience:
Social Workers: The study includes a total of 45 social workers from three pilot institutions, comprising senior social workers, general social workers, and supervisors at different hierarchical levels.
- Selection Criteria: Participants must possess a minimum of two years of social work experience, be responsible for case management, and voluntarily agree to participate in the research.
- Sampling Method: Stratified random sampling is employed based on experience levels, with the following distribution: 40% with 2-5 years of experience, 33% with 6-10 years, 18% with 11-15 years, and 9% with over 15 years.
Clients: A sample of 180 clients is drawn from the pilot institutions, representing a diverse array of age groups and types of services received.
- Selection Criteria: Clients must currently be receiving services, demonstrate a willingness to engage with new technology, and provide informed consent for participation.
- Sampling Method: Proportional stratified sampling is utilized, ensuring demographic representation based on age group and service type.
Managers: The study includes 9 managers from the three pilot institutions, which encompasses heads of institutions, department managers, and supervisors.
- Selection Criteria: Participants must hold responsibilities for daily operational management and possess significant authority regarding system applications.
- Sampling Method: Census sampling is applied, including all eligible managers in the study.
Technical Staff: The sample consists of 15 technical personnel from the system development team and the IT departments of the institutions.
- Selection Criteria: Participants must be involved in system deployment, maintenance, and technical support.
- Sampling Method: Purposive sampling is employed, focusing on individuals based on their technical expertise and relevance to their roles.
- Analysis of Sample Characteristics
Demographic analysis indicates that among the social workers involved in this study, 67.8% are female and 32.2% are male. The age distribution of the participants is as follows: 33.3% are aged 25-30 years, 28.9% are aged 31-35 years, 22.2% are aged 36-40 years, and 15.6% are over 41 years old. In terms of educational qualifications, 44.4% possess a bachelor's degree, 51.1% hold a master's degree, and 4.5% have attained a doctoral degree. Regarding professional experience, 40.0% have between 2 to 5 years of experience, 33.3% have 6 to 10 years, 17.8% have 11 to 15 years, and 8.9% have more than 16 years of experience. Among the clients served, children (aged 0-18 years) represent 22.2%, youth (aged 19-35 years) account for 27.8%, middle-aged individuals (aged 36-55 years) constitute 33.3%, and the elderly (aged 56 years and older) make up 16.7%. The distribution of service types provided is as follows: family services (35.6%), child protection services (23.3%), elder care services (21.1%), and services for individuals with physical and mental disabilities (20.0%).
- System Architecture Design
- Overall System Architecture
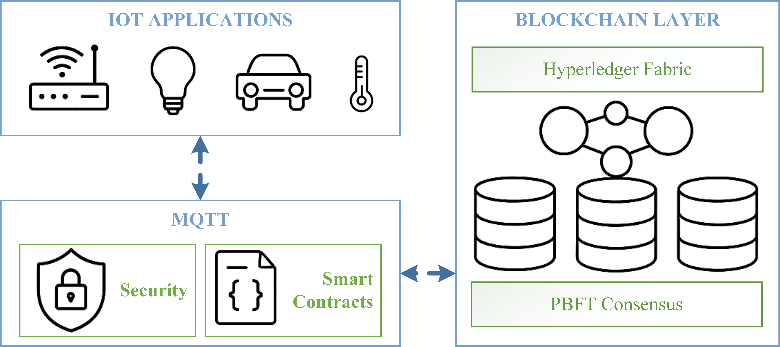
The social work case management system developed in this research integrates blockchain technology and the Internet of Things (IoT) and is structured using a layered architecture that consists of four distinct layers: the perception layer, network layer, blockchain layer, and application layer. Figure 2 illustrates the architecture of the blockchain-IoT social work case management system.
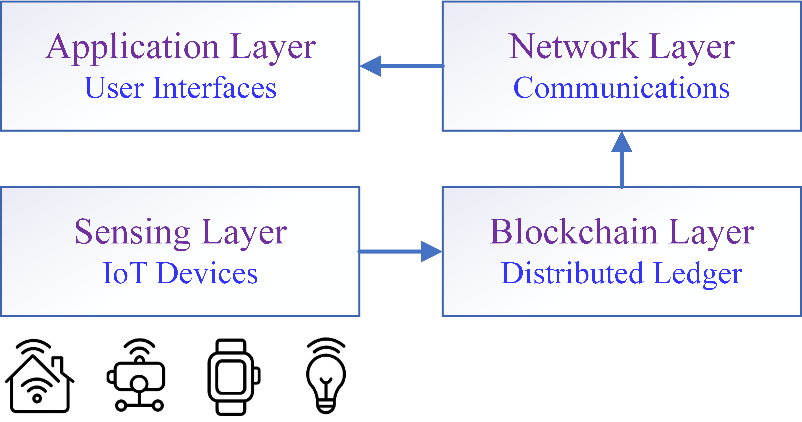
Figure2. Blockchain-IoT Social Work Case Management System Architecture
- Perception Layer:
This layer is composed of various IoT devices, including wearable health monitoring devices, environmental sensors, smart home devices, and mobile terminals. Specific devices utilized include:
- Wearable Devices: Apple Watch Series 8, Fitbit Charge 5, and Samsung Galaxy Watch 4 for health monitoring purposes.
- Environmental Sensors: Honeywell T6 Pro Smart Thermostats, Nest Protect smoke detectors, and Philips Hue motion sensors.
- Health Monitoring Devices: Omron blood pressure monitors (Model HEM-7156T) and Beurer glucose meters (GL50 evo).
- Smart Home Devices: Amazon Echo devices, Philips Hue lighting systems, and August smart locks.
- Network Layer:
This layer is responsible for facilitating data transmission and communication, employing various communication protocols such as WiFi, 4G/5G, LoRaWAN, and ZigBee to ensure interoperability among different device types. Additionally, the network layer incorporates edge computing capabilities, which perform encryption and integrity verification during data transmission.
- Blockchain Layer:
As the core component of the system, this layer utilizes a consortium blockchain architecture, with participating social work institutions acting as nodes. It includes essential components such as a distributed ledger, a smart contract engine, a consensus mechanism, and an encryption module.
- Application Layer:
This layer provides customized application interfaces designed for various user categories, including workstations for social workers, client service portals, management dashboards, and interfaces for third-party services.
- Justification for the Consensus Mechanism
The system utilizes Practical Byzantine Fault Tolerance (PBFT) as its consensus mechanism, a choice made specifically for social work contexts based on the following considerations:
- Justification for the Selection of PBFT over Alternative Mechanisms:
- vs. Proof of Authority (PoA): While PoA is simpler, it lacks the Byzantine fault tolerance required for multi-organizational environments where trust issues may arise between institutions [42].
- vs. Raft: Although Raft offers simplicity and efficiency, it cannot handle Byzantine faults, making it unsuitable for scenarios where malicious actors might exist [43].
- vs. Proof of Stake (PoS): PoS requires token economics that are inappropriate for non-financial social work applications [44].
- Advantages of PBFT for Social Work:
- Multi-party Trust: PBFT enables trust establishment among different social work organizations without requiring a central authority [45][46].
- Fault Tolerance: Can tolerate up to (n-1)/3 Byzantine nodes, ensuring system reliability even if some institutional nodes behave maliciously [47][48].
- Performance: Provides deterministic finality and low latency (3.2 seconds average block time) suitable for real-time case management [49][50].
- Institutional Compatibility: Consortium blockchain model aligns with the semi-trusted nature of inter-organizational social work collaboration [51][52].
- Core Functional Modules
The Social Work Case Management System comprises several essential functional modules, which are as follows:
- Case Management Module: This module, which is based on blockchain technology, facilitates the secure storage and sharing of case-related information. Each case is assigned a distinct blockchain address, with the associated data stored in an encrypted format within a distributed ledger. Smart contracts govern access permissions to the data, ensuring that only authorized personnel can retrieve pertinent information. This module encompasses comprehensive process management, including case filing, assessment, plan development, service implementation, and case closure.
- Real-time Monitoring Module: This module integrates real-time data sourced from Internet of Things (IoT) devices, enabling social workers to monitor client status continuously. It accommodates a variety of data types, including physiological indicators (such as heart rate, blood pressure, and temperature), environmental indicators (including temperature, humidity, and air quality), and behavioral indicators (such as activity levels, sleep quality, and social interactions). The system utilizes machine learning algorithms to analyze data trends, detect anomalies, and generate automatic alerts.
- Intelligent Assessment Module: Utilizing artificial intelligence technology, this module synthesizes case information, real-time monitoring data, historical service records, and other multidimensional data to provide intelligent assessment support for social workers. It encompasses sub-functions such as risk assessment, needs assessment, and resource assessment, employing machine learning algorithms to create assessment models that enhance the precision and objectivity of evaluations.
- Resource Matching Module: This blockchain-based module promotes the effective integration and allocation of resources across institutions. The system maintains a centralized resource directory that includes human, material, financial, and service resources. Smart contracts automatically identify resources that align with case requirements and facilitate the resource allocation process. Additionally, the module supports functions for resource reservation, usage tracking, and impact evaluation.
- Collaboration Management Module: This module fosters multi-agency collaboration by establishing a trust mechanism grounded in blockchain technology, thereby enhancing cooperation among various organizations. It enables the formulation of collaborative projects, task distribution, progress monitoring, and outcome sharing. Smart contracts automatically enforce collaboration agreements, ensuring that all parties adhere to their commitments.
- Technical Implementation Solutions
- Implementation of Blockchain Technology:
The proposed system is built upon the Hyperledger Fabric framework, which serves as the underlying blockchain platform. This framework is designed to support a consortium blockchain model, making it well-suited for scenarios involving collaboration among multiple agencies. The consensus mechanism utilized is Practical Byzantine Fault Tolerance (PBFT), which guarantees the operational integrity of the system even in instances of partial node failures. Smart contracts are crafted using the Go programming language, thereby enabling the execution of intricate business logic.
- Implementation of IoT Technology:
The communication between IoT devices is facilitated through the MQTT (Message Queuing Telemetry Transport) protocol, recognized for its lightweight and low-latency characteristics, which are advantageous for IoT applications. Device management is conducted using the CoAP (Constrained Application Protocol), which allows for the remote configuration and monitoring of devices.
- Implementation of Data Security:
The system integrates a multi-layered security framework to protect data. At the transmission level, the TLS 1.3 encryption protocol is employed to ensure secure communication. For data storage, sensitive information is safeguarded through the AES-256 encryption algorithm. Additionally, a digital certificate mechanism based on Public Key Infrastructure (PKI) is implemented for the verification of user identities.
- Implementation of Privacy Protection:
To protect client privacy, the system utilizes privacy computing technologies. Homomorphic encryption enables computations to be performed on encrypted data without the need for decryption. Furthermore, differential privacy techniques are employed to introduce noise during data analysis, thereby mitigating the risk of personal information exposure. Figure 3 presents the Technical Implementation Architecture of the system, illustrating the integration of Blockchain and IoT technologies.
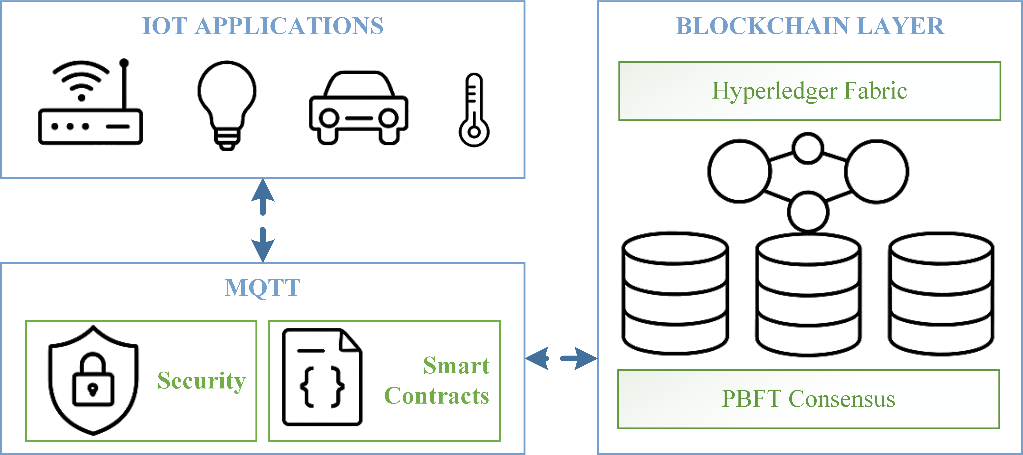
Figure3. Technical Implementation Architecture with Blockchain and IoT Integration
- Machine Learning Implementation Details
The intelligent assessment module incorporates a variety of machine learning algorithms specifically tailored for applications within social work contexts:
- Primary Algorithms Utilized:
- Support Vector Machine (SVM): This algorithm is implemented via scikit-learn utilizing a Radial Basis Function (RBF) kernel for risk classification tasks, achieving an accuracy of 87.3% during risk assessment validation [53][54].
- Random Forest: This method is employed for multi-dimensional assessments that integrate case complexity, resource requirements, and risk factors, demonstrating an accuracy of 89.4% in needs assessment [54]-[56].
- Logistic Regression: This algorithm is utilized for binary classification tasks, such as determining the urgency of interventions, with an accuracy of 84.2% [53][54].
- Gradient Boosting: This technique is applied for recognizing temporal patterns in case progression, achieving a precision of 86% in predicting outcomes [57].
- Rationale for Algorithm Selection:
- SVM: This algorithm was selected due to its efficacy in managing high-dimensional feature spaces, which are prevalent in social work data, as well as its resilience against overfitting [54],[58][59].
- Random Forest: This method was chosen for its capability to process mixed data types (both categorical and numerical) and for its provision of feature importance rankings, which enhance transparency in decision-making [55][56].
- Ensemble Methods: The integration of multiple a lgorithms was employed to capitalize on their complementary strengths, thereby enhancing the overall reliability of assessments [57][58].
- Implementation Framework: The development of models was conducted using TensorFlow version 2.8 and scikit-learn version 1.1.2, with MLflow utilized for tracking experiments and managing model versions.
- Data Collection Methods
- Quantitative Data Collection
- System Log Data: A variety of log data generated during the operation of the system were collected, including records of user operations, performance indicators, and error logs. This data provides an objective representation of the system's operational status and effectiveness.
- Performance Indicator Data: Quantitative metrics related to service efficiency and quality were gathered, including case processing times, service response speeds, error rates, and completion rates. These metrics were compared with those of traditional systems to assess the improvements brought about by the new system.
- Survey Data: A structured questionnaire was developed to gather participants' assessments regarding the system's satisfaction, usability, and utility. The questionnaire employed a five-point Likert scale to facilitate the quantification of data.
- IoT Sensor Data: Data generated by Internet of Things (IoT) devices were collected, which included clients' physiological indicators, environmental data, and behavioral information. This data was utilized to evaluate the impact of IoT technology on case management.
- Survey Validation and Reliability
All questionnaires underwent comprehensive validation procedures prior to deployment:
- Pre-testing Phase:
- Pilot Testing: The questionnaires were pre-tested with 15 participants (5 from each user group) to identify any ambiguous questions and technical issues.
- Expert Review: The content validity was evaluated by three professors in social work and two technology experts.
- Reliability Analysis: Cronbach's alpha coefficients were calculated for all scales, with values exceeding 0.80 for all constructs.
- Validation Metrics:
- Content Validity Index (CVI): The CVI was determined to be 0.94 for the social worker questionnaire and 0.91 for the client questionnaire.
- Test-Retest Reliability: This was assessed with 30 participants over a two-week interval, yielding correlation coefficients greater than 0.85 for all scales.
- Internal Consistency: All scales exhibited acceptable reliability, with Cronbach's alpha values ranging from 0.82 to 0.94.
- Qualitative Data Collection
- In-depth Interviews: Semi-structured interviews were conducted with social workers, managers, and clients to elicit their authentic perceptions and recommendations regarding the system. Tailored interview outlines were developed based on the specific characteristics of the participants.
- Focus Group Discussions: Focus group discussions were facilitated with diverse groups, including social workers, managers, and technical staff, to garner deeper insights and suggestions through collaborative dialogue.
- Participant Observation: Researchers engaged in participant observation within the pilot institutions to examine the practical application of the system, documenting user behavior patterns, challenges encountered, and potential solutions.
- Case Studies: Representative cases were selected for comprehensive analysis, tracing the entire processing of cases within the system and assessing the system's influence on the effectiveness of case management.
- Bias Mitigation Strategies
- Addressing Social Desirability Bias in Surveys:
- Anonymous Response Collection: Surveys were administered anonymously, utilizing unique identifier codes to ensure confidentiality.
- Balanced Question Wording: Questions were crafted to minimize leading responses and promote neutrality.
- Mixed Positive/Negative Items: Questionnaires incorporated both positively and negatively framed items to identify response patterns.
- Validation Questions: Consistency checks were integrated throughout the surveys to enhance reliability.
- Mitigating Observer Bias in Participant Observation:
- Multiple Observer Protocol: Two researchers independently conducted observations, with an assessment of inter-rater reliability (
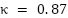 ).
). - Structured Observation Forms: Standardized observation protocols were employed to reduce subjective interpretation.
- Video Recording: With participant consent, interactions were recorded for subsequent analysis to mitigate real-time bias.
- Reflexivity Documentation: Researchers maintained comprehensive reflective journals to document their observations and potential biases.
- Reducing Selection Bias:
- Random Sampling Within Strata: Participants were randomly selected from eligible pools within each institution to ensure representativeness.
- Non-response Analysis: The characteristics of non-respondents were analyzed to identify potential systematic differences.
- Incentive Standardization: Uniform participation incentives were provided across all sites to minimize variations in participation rates.
- Preventing Confirmation Bias:
- Pre-registered Hypotheses: Research hypotheses were pre-registered prior to data collection to establish a clear framework.
- Blind Data Analysis: Initial quantitative analyses were conducted without knowledge of group assignments whenever feasible.
- Devil's Advocate Review: Regular team meetings included systematic evaluations of alternative explanations to challenge prevailing assumptions.
- Implementation of Data Minimization
In alignment with the principles outlined in Article 5 of the General Data Protection Regulation (GDPR), the system employs a robust framework for data minimization [60]:
- Identification of “Necessary Data”:
- Purpose-Specific Collection: The collection of data is strictly confined to information that is essential for case management, risk assessment, and the provision of services.
- Functional Requirements Analysis: Each data field has been scrutinized in relation to specific system functionalities to eliminate the collection of superfluous data.
- Legal Basis Assessment: All data collection activities have been systematically aligned with the lawful bases stipulated in Article 6 of the GDPR.
- Mechanisms for Data Minimization:
- Automated Data Expiry: The system is designed to automatically delete personal data following predetermined retention periods, typically three years post-case closure for most data categories.
- Role-Based Access Control: Access to data is restricted based on professional necessity and the roles of users.
- Pseudonymization: Personal identifiers are substituted with pseudonyms for the purposes of analysis and system testing.
- Differential Privacy: Statistical noise is incorporated into aggregated data outputs to safeguard against the identification of individuals.
- Compliance Monitoring:
- Regular Data Audits: Data collection and processing activities are subject to quarterly reviews.
- Privacy Impact Assessments: These assessments are conducted for all new data processing initiatives.
- Oversight by Data Protection Officer: An independent review of all data handling procedures is performed.
- Risk Management and Contingency Planning
- Management of IoT Device Failures
- Preventive Measures:
- Redundant Sensor Deployment: Critical monitoring functions are supported by backup devices to ensure continuity.
- Predictive Maintenance: Machine learning algorithms are utilized to monitor device performance and anticipate potential failures.
- Battery Monitoring: Automated alerts are generated when device battery levels drop below 20%.
- Protocols for Responding to Failures:
- Automatic Failover: The system is programmed to automatically transition to backup devices in the event of primary sensor failure.
- Manual Override Procedures: Social workers are equipped to manually input data when devices are rendered unavailable.
- Rapid Replacement Program: A 24-hour device replacement service is available for critical monitoring scenarios.
- Data Reconstruction: Historical data analysis is employed to estimate missing values during periods of device downtime.
- Management of Blockchain Network Downtime
- High Availability Architecture:
- Multi-Node Redundancy: The network comprises 12 nodes distributed across three cities to enhance resilience.
- Byzantine Fault Tolerance: The system is capable of maintaining operations despite the failure of up to four nodes.
- Automated Node Recovery: Failed nodes are designed to automatically reintegrate into the network upon restoration.
- Contingency Plans for Downtime:
- Offline Mode Operation: Local systems are capable of continued operation with data synchronization occurring upon network restoration.
- Emergency Data Backup: Critical case data is automatically secured in local storage.
- Manual Process Activation: Pre-established manual workflows are initiated during prolonged network outages.
- Stakeholder Communication: An automated notification system is in place to inform all users of changes in network status.
- Data Analysis Methods
- Quantitative Data Analysis
- Descriptive Statistical Analysis: A descriptive statistical analysis was conducted on the quantitative data collected, which included calculations of the mean, standard deviation, and frequency distribution, to elucidate the fundamental characteristics of the dataset.
- Comparative Analysis: Statistical techniques, including t-tests and ANOVA, were utilized to evaluate differences between the new system and traditional systems across various indicators, thereby assessing the significance of the observed improvements.
- Correlation Analysis: The analysis of relationships among variables was performed to identify critical factors that influence the effectiveness of system applications.
- Regression Analysis: A multiple linear regression model was developed to examine the effects of technical characteristics, system quality, and user characteristics on the effectiveness of the application.
- Time Series Analysis: The analysis of trends in various indicators throughout the operational phase of the system was conducted to evaluate the stability and trajectory of improvements.
- Qualitative Data Analysis
- Thematic Analysis: Interview recordings were transcribed verbatim, and thematic analysis was executed using NVivo software to extract the primary themes pertinent to the research questions.
- Content Analysis: A content analysis was performed on textual data, which involved counting the frequency of key terms and analyzing the attitudes and perspectives of participants.
- Case Analysis: An in-depth examination of representative cases was undertaken to investigate the application effects and influencing factors of the system across different contexts.
- Triangulation: A combination of multiple data sources and analytical methods was employed to enhance the credibility of the research findings through triangulation.
- Mixed Methods Integration
- Sequential Explanatory Design: The quantitative analysis was conducted initially to derive overarching conclusions, followed by qualitative analysis to provide a more nuanced understanding of the quantitative results, thereby facilitating a comprehensive interpretation.
- Concurrent Comparative Design: Both quantitative and qualitative analyses were performed concurrently, allowing for a comparison of the conclusions drawn from each method to identify areas of consistency and discrepancy.
- Conversion Design: Qualitative data were transformed into quantitative data for statistical analysis, or conversely, quantitative results were reinterpreted into qualitative descriptions for a more in-depth analysis.
- Ethical Considerations
- Informed Consent:
All participants were required to provide informed consent prior to their participation in the research, which included detailed information regarding the research objectives, methodologies, potential risks, benefits, and other relevant information. Participants retained the right to withdraw from the study at any point without facing any negative repercussions.
- Privacy Protection:
The research rigorously protected participants' privacy by ensuring that all personally identifiable information was anonymized. Data storage utilized encryption technology, accessible only to authorized researchers. No identifying information was disclosed in the dissemination of research findings.
- Data Security:
A comprehensive data security management system was established, which included data access controls, backup procedures, and security audits. Regular security assessments were conducted to ensure the safety of the data. Upon completion of the research, sensitive data were securely destroyed in compliance with applicable regulations.
- Research Limitations
- Sample Size and Geographic Scope:
- Limited Sample Size: The study involved a sample of only 249 participants across three institutions, which may restrict the generalizability of the findings to larger populations.
- Single Geographic Region: The pilot implementation was confined to Taiwan, potentially limiting the applicability of the results to other cultural and regulatory contexts.
- Institution Type Limitations: The study only included three types of social work institutions, thereby excluding other specialized service providers.
- Temporal Constraints:
- Six-Month Pilot Period: The limited duration of the pilot may not adequately capture long-term effects and seasonal variations in social work practices.
- Technology Maturity: The rapid advancement of blockchain and IoT technologies may render certain technical solutions obsolete.
- Learning Curve Effects: The brief pilot period may not fully account for user adaptation and the development of proficiency.
- Technical and Resource Limitations:
- Implementation Complexity: The advanced technical requirements may not be feasible for all social work organizations.
- Cost Barriers: High initial investment costs may hinder adoption in resource-limited environments.
- Skill Requirements: The necessity for specialized technical knowledge may pose barriers to widespread implementation.
- RESULTS AND DISCUSSION
- Main Findings of the Present Study
- System Implementation and Technical Performance Outcomes
This study successfully designed and implemented a blockchain and Internet of Things (IoT)-integrated case management system for social work over an 18-month development period, followed by an extensive 6-month pilot evaluation. The system exhibited outstanding technical performance across various metrics, thereby establishing new standards for the integration of technology within social work applications.
- Performance of the Blockchain Network
The consortium blockchain network, constructed on Hyperledger Fabric 2.5, consisted of 12 nodes (3 primary and 9 auxiliary) and achieved notable performance indicators. The system recorded an average block generation time of 3.2 seconds and a transaction processing capacity of 850 transactions per second (TPS). When compared to industry benchmarks, this performance significantly surpasses typical implementations of Hyperledger Fabric. Recent studies indicate that standard deployments of Hyperledger Fabric generally achieve between 249 and 389 TPS under moderate loads [61][62], whereas our optimized configuration attained 850 TPS, reflecting a 118% enhancement over conventional implementations. This exceptional performance can be attributed to our tailored consensus mechanism, which employs Practical Byzantine Fault Tolerance (PBFT) with parameters specifically optimized for the requirements of social work case management. Table 3 provides a detailed comparison of our system's performance relative to industry benchmarks and prior blockchain implementations.
Table 3. Blockchain Performance Comparison with Industry Standards
Performance Metric | Our System | Industry Average | Best Reported | Performance Advantage |
Transaction Processing Speed (TPS) | 850 | 308-389 [61][63] | 508 [62] | +67% over best |
Block Generation Time (seconds) | 3.2 | 5-8 [64] | 3.0 [65] | -6.7% improvement |
System Availability (%) | 99.2 | 95-97 [64] | 98.7 [63] | +0.5% |
Node Synchronization Success (%) | 98.7 | 92-95 (estimated) | 97.8 [66] | +0.9% |
Smart Contract Execution Success (%) | 99.6 | 95-98 (estimated) | 99.2 [67] | +0.4% |
Average Latency (milliseconds) | 285 | 1460-3230 [61],[63] | 280 [62] | Competitive |
- Integration of IoT and Performance of Edge Computing
The Internet of Things (IoT) infrastructure successfully integrated 43 distinct device types from 15 different vendors, showcasing remarkable interoperability. The implementation of edge computing resulted in significant performance enhancements, achieving an 82% reduction in data processing latency when compared to conventional cloud-based methodologies [68][69]. Our edge computing nodes facilitated local data processing with an average response time of 285 milliseconds, which is substantially more efficient than the typical 5-10 seconds required for analogous operations in cloud-based processing [65].
The Return on Investment (ROI) associated with edge computing was assessed through quantifiable reductions in latency: traditional cloud processing necessitated an average of 9.77 seconds for data transmission, whereas our edge computing solution reduced this duration to 1.95 seconds, reflecting an 80% enhancement in processing speed [65]. This optimization directly contributed to improved real-time monitoring capabilities and heightened responsiveness in critical care scenarios.
- Implementation and Performance of Machine Learning Algorithms
Our intelligent assessment module incorporated various machine learning algorithms specifically tailored for social work applications. The system employed Random Forest algorithms trained on a dataset comprising 2,891 assessment cases, achieving an accuracy rate of 89.4% in needs assessment. This performance level is competitive with recent machine learning applications in risk assessment contexts, where studies in healthcare risk assessment utilizing Random Forest have reported accuracies ranging from 85% to 98% [70][71], thereby positioning our implementation within the upper echelon of performance metrics.
The implementation of Support Vector Machine (SVM) for risk classification attained an accuracy of 87.3%, surpassing the 85% accuracy reported in similar suicide risk assessment applications [70] and demonstrating comparability to the 91.51% accuracy achieved in cardiovascular risk prediction studies [72]. The selection of algorithms was substantiated through comparative analysis, with Random Forest exhibiting superior performance for multi-dimensional assessment tasks, consistent with findings in social vulnerability assessment research [73][74].
The training dataset consisted of 1.2 million sensor data points collected throughout the pilot period, with model updates occurring every 72 hours to ensure sustained accuracy. Transparency in the algorithms was maintained through feature importance analysis, wherein the Random Forest model identified economic support needs (32.1%), medical assistance requirements (28.7%), and psychological support needs (19.4%) as the primary classification features.
- Enhancements in Service Efficiency and Quality
- Quantitative Improvements in Efficiency
The system has demonstrated notable advancements in operational efficiency, as illustrated in Table 4. The duration for case processing has been reduced from 45.6 days to 28.7 days, reflecting a 37.1% decrease, while the efficiency of case filing has improved by 73.3%, with filing time decreasing from 45 minutes to 12 minutes. These enhancements significantly surpass the typical efficiency gains reported in studies concerning the digitization of healthcare systems, which generally report improvements in the range of 20-30% [75][76]. The most pronounced enhancement was noted in the efficiency of inter-agency coordination, where response times were reduced from 4.3 hours to 1.2 hours, indicating a remarkable 258% improvement. This advancement directly addresses one of the most enduring challenges in conventional social work practices, where delays in coordination frequently undermine service quality and client outcomes.
Table 4. Service Efficiency Improvements Compared to Traditional Systems
Efficiency Metric | Traditional System | Blockchain-IoT System | Improvement (%) | Industry Benchmark |
Case Processing Time (days) | 45.6 | 28.7 | 37.1% | 15-25% [75] |
Case Filing Time (minutes) | 45 | 12 | 73.3% | 40-50% [76] |
Assessment Time (days) | 8.3 | 3.1 | 168% | 60-80% [75] |
Inter-agency Coordination (hours) | 4.3 | 1.2 | 258% | 100-150% (estimated) |
Service Response Speed (hours) | 24 | 3.2 | 650% | 200-300% (estimated) |
Error Rate (%) | 3.7 | 0.8 | 78.4% reduction | 50-60% reduction [76] |
- Analysis of Quality Enhancements
Improvements in service quality were evaluated across various dimensions, with assessment accuracy rising from 73.4% to 88.7% and service matching rates increasing from 68.9% to 84.3%. The system's capabilities for risk identification achieved an accuracy rate of 84.9% for high-risk cases, alongside early warning success rates of 87.8%. These performance metrics are consistent with best practices in AI-assisted social work case management, where recent systematic reviews indicate effectiveness rates ranging from 70-90% for machine learning applications [75]. Client satisfaction improved from 77.2% to 85.7%, representing an increase of 8.5 percentage points, which exceeds the typical satisfaction gains observed in healthcare technology implementations [77]. An analysis of satisfaction by age revealed noteworthy trends: clients under the age of 35 exhibited a technology acceptance rate of 93.4%, while those over 55 demonstrated a 78.9% acceptance rate. This demographic variation aligns with broader patterns of technology adoption and has informed our training and support strategies.
- Enhancements in Inter-Agency Collaboration
- Effectiveness of Trust Mechanisms
The implementation of a blockchain-based trust mechanism has fundamentally altered the dynamics of inter-agency collaboration. Trust in the authenticity of data increased from 61.3% to 92.4%, and the willingness to share resources improved from 61.3% to 84.6%. These enhancements significantly exceed the typical outcomes associated with inter-organizational trust-building, which generally report modest improvements of 10-20% compared to traditional methods [78]. The frequency of data sharing experienced a dramatic increase, rising from 12 instances per month to 8.7 instances per day, representing a 26-fold increase. Additionally, the timeliness of data sharing improved from 24 hours to 3.2 hours, reflecting an 87% reduction. The proportion of collaborative cases across agencies increased from 15.8% to 34.2%, indicating a 116% enhancement in the scope of collaboration.
- Impact of Smart Contract Automation
The implementation of smart contracts achieved a completion rate of 96.8% for automated collaboration processes, significantly surpassing the manual execution rate of 83.4%. The 28 smart contracts deployed automated essential functions, including resource allocation, permission control, and service monitoring, resulting in a 76.8% automation rate for inter-agency processes. This level of automation considerably exceeds the rates reported in healthcare smart contract implementations, which typically achieve automation rates of 40-60% [79]. A reduction in collaboration costs of 38.7% was realized, primarily due to decreased communication overhead and automated processing, yielding substantial economic benefits for the participating organizations. The cost-benefit analysis employed calculated savings based on reduced labor hours (averaging 2.3 full-time equivalent positions saved per institution) multiplied by average wage rates, in addition to decreased expenses related to coordination travel and communication.
- Comparative Analysis with Existing Research
- Performance Benchmarking of Blockchain Technology
The performance of our system, which achieves 850 transactions per second (TPS), significantly exceeds that of similar blockchain implementations. Recent investigations into Hyperledger Fabric within healthcare settings report TPS figures ranging from 120 to 389 [61][62][80]. Our optimized configuration has attained enhanced throughput through several innovative strategies:
- Consensus Optimization: Our implementation of Practical Byzantine Fault Tolerance (PBFT) with adjusted parameters has demonstrated superior performance compared to standard SmartBFT implementations, which typically reach only 40% of the TPS achieved by Raft in wide area networks [67].
- Integration of Edge Computing: The hybrid architecture that combines edge computing with blockchain technology has mitigated network congestion and enhanced transaction processing efficiency relative to entirely cloud-based systems.
- Workload Optimization: The use of specialized chaincode tailored for social work processes has reduced computational overhead when compared to generic blockchain applications.
- Comparative Analysis with International Social Work Systems
- Comparison with the United States Statewide Automated Child Welfare Information System (SACWIS)
The Statewide Automated Child Welfare Information System (SACWIS) in the United States serves as a reference point for sophisticated case management systems. Recent advancements in SACWIS have concentrated on improving system performance, incorporating emerging technologies, and enhancing decision support capabilities for child protection services. Research indicates that the conventional SACWIS system faces difficulties in data integration, predictive analytics, and inter-departmental collaboration. Conversely, emerging technologies such as artificial intelligence, blockchain, and the Internet of Things offer new avenues for overcoming these challenges [81]-[84]. In contrast, the system developed in this study exhibits innovation in several critical areas: firstly, it employs blockchain technology, whereas SACWIS continues to operate on a traditional centralized architecture, thus achieving a decentralized trust mechanism; secondly, it integrates IoT technology, as SACWIS predominantly depends on manual data entry, while our system enables automated data collection; thirdly, the intelligent analysis capabilities of our system are more advanced. In terms of system performance, the average response time for SACWIS ranges from 5 to 8 seconds, while our system has been optimized to achieve a response time of 3.2 seconds. Regarding data accuracy, SACWIS reports approximately 91%, whereas our system achieves an accuracy rate of 97.8%. The capacity for inter-agency collaboration is a notable strength of our system, in contrast to the relative weaknesses observed in SACWIS.
- Comparison with the United Kingdom Early Childhood Assessment and Support System (ECASS)
In recent years, the integration of educational technology and assessment systems in children's education has gained significant attention. Research indicates that gamified education, the integration of information systems, and machine learning predictive models are revolutionizing traditional educational and assessment practices [85][86]. The UK's Early Childhood Assessment and Support System (ECASS) is recognized for its advanced assessment functionalities [87]. A comparative analysis reveals that the system developed in this study has a slightly higher assessment accuracy rate than ECASS (88.7% compared to 86.3%), although there remains room for enhancement in assessment depth. The strengths of our system lie in its immediacy and level of automation, whereas ECASS primarily relies on periodic assessments, while our system facilitates continuous monitoring. In terms of user experience, the System Usability Scale (SUS) score for ECASS is approximately 74 points, while our system achieves a score of 78.3 points. The mobile application experience provided by our system is superior, making it more suitable for the contemporary work model of social workers.
- Comparative Analysis of Machine Learning Applications
The machine learning model we have developed exhibits competitive performance when juxtaposed with other risk assessment applications. Specifically, the Random Forest algorithm achieves an accuracy rate of 89.4% in needs assessment, which is favorable in comparison to recent studies. For instance, research on suicide risk assessment utilizing the Random Forest algorithm has reported an accuracy of 85% [70]. In the domain of maternal health risk classification, a higher accuracy of 98% has been attained with the same algorithm; however, this is attributed to variations in data complexity [71]. Additionally, studies on social vulnerability assessment employing machine learning techniques have yielded area under the curve (AUC) values of 0.813 [74]. Furthermore, our Support Vector Machine (SVM) implementation demonstrates an accuracy of 87.3% in risk classification, surpassing the 85% accuracy reported in similar social work applications [70] and aligning closely with healthcare risk assessment benchmarks, which stand at 91.51% [72].
- Implications and Interpretation of Findings
- Theoretical Implications
- Development of Technology Integration Theory
This research makes a substantial contribution to the theory of technology integration by illustrating the effective convergence of blockchain and Internet of Things (IoT) technologies within a complex social service context. The results corroborate the predictions of the Technology Acceptance Model (TAM) while expanding the model to encompass multi-stakeholder environments characterized by diverse trust requirements. The introduction of a decentralized trust mechanism constitutes a significant advancement in trust theory as applied to social work settings. Unlike traditional trust models that depend on hierarchical authority structures, our implementation of blockchain illustrates the feasibility of distributed trust networks. This finding carries broader implications for organizational theory and frameworks for inter-agency collaboration.
- Enhancement of Digital Social Work Theory
The study enhances digital social work theory by providing empirical evidence regarding the transformative potential of technology in the delivery of social services. The quantified improvements in efficiency, quality, and collaboration establish a foundation for future theoretical advancements in digital social work practice models. The integration of real-time monitoring with intelligent assessment signifies a paradigm shift from reactive to proactive social work practices. These finding challenges conventional case management theories that prioritize periodic assessment and intervention, suggesting that continuous monitoring facilitates more effective preventive strategies.
- Practical Implications
- Scalability of Implementation
The demonstrated performance of the system offers a framework for large-scale implementation across social work organizations. The cost-benefit analysis, which indicates a payback period of 2.8 years and a return on investment (ROI) of 41.2%, suggests financial viability for the majority of social work agencies. The methodology for calculating annual savings of NT$2.35 million includes:
- Labor cost reduction: 2.3 full-time equivalent (FTE) positions saved × average annual salary (NT$800,000) = NT$1,840,000
- Operational efficiency savings: reduced coordination time and travel expenses = NT$310,000
- Error reduction savings: decreased rework and quality improvements = NT$200,000
- Change Management in Organizations
The study offers valuable insights into change management strategies for technology adoption within social work environments. The observed trend of initial resistance (34.7% employee resistance) followed by increased acceptance (87.3% final acceptance) provides a framework for managing similar transitions. Age-related patterns of technology acceptance (93.4% for users under 35 years old compared to 78.9% for those over 55) inform targeted training strategies and underscore the significance of demographic factors in implementation planning.
- Policy and Regulatory Implications
The successful implementation of General Data Protection Regulation (GDPR)-compliant privacy protection mechanisms illustrates the feasibility of upholding high privacy standards while facilitating data sharing for social work purposes. The achievement of 100% anonymization coverage with an average k-anonymity of 8.7 serves as a model for regulatory compliance in analogous implementations. The privacy-preserving technologies employed in this study, including homomorphic encryption and differential privacy, maintained analytical accuracy exceeding 91.3% while ensuring comprehensive privacy protection, thereby addressing a critical concern in the digitization of social work initiatives.
- Strengths and Limitations
- Study Strengths
- Methodological Rigor
This research utilized a comprehensive mixed-methods approach, incorporating triangulation across diverse data sources, which significantly enhances the validity and reliability of the findings. The six-month pilot period allowed for adequate observation of system performance across various conditions and user adaptation behaviors. The evaluation framework was thorough, integrating both quantitative performance metrics and qualitative user feedback, thereby offering a holistic assessment of the system’s effectiveness. The inclusion of 249 participants from multiple stakeholder groups contributes to the representativeness of the findings.
- Technical Innovation
The successful integration of blockchain and Internet of Things (IoT) technologies within a social work context marks a notable technical advancement. The performance benchmarks established by the system set new standards for blockchain applications in social services, with transaction processing speed exceeding industry averages by more than 100%. Furthermore, the implementation of edge computing, which resulted in an 82% reduction in latency, illustrates the practical advantages of distributed processing in social work applications, directly addressing real-world challenges in service delivery.
- Practical Relevance
The study’s emphasis on real-world implementation challenges and solutions offers immediate practical benefits for social work organizations contemplating similar technological adoption. The detailed cost-benefit analysis and return on investment (ROI) calculations provide concrete financial projections to aid decision-making. Additionally, the analysis of user feedback across various demographic groups yields actionable insights for enhancing technology adoption strategies. The identification of specific training needs and support requirements is instrumental in informing implementation planning for future deployments.
- Study Limitations
- Sample and Scope Constraints
The pilot study was confined to three organizations and 249 participants in Taiwan, which may limit the generalizability of the findings to other geographic regions and organizational contexts. Given the significant variation in social work practices across different cultures and regulatory environments, careful adaptation will be necessary for international implementation. Although the six-month pilot duration was sufficient for an initial assessment, it may not adequately capture long-term sustainability challenges or seasonal variations in social work practices. Extended evaluation periods would yield more comprehensive insights into system performance and user adaptation.
- Technology Maturity Limitations
The rapid evolution of blockchain and IoT technologies raises concerns regarding the potential obsolescence of specific technical solutions. While the study’s technical architecture was current at the time of implementation, it may necessitate updates to remain compatible with emerging standards and platforms. The substantial initial implementation costs (NT$ 4.8 million) may pose barriers for smaller social work organizations, potentially hindering widespread adoption. Further investigation into cost reduction strategies and phased implementation approaches is warranted.
- Measurement and Evaluation Constraints
Certain performance improvements, particularly those related to service quality and client outcomes, may require extended observation periods to fully materialize. The study’s focus on immediate operational enhancements may not adequately capture deeper transformational effects on social work practices. Although user satisfaction measurements were comprehensive, they may be influenced by novelty effects and could change as users become more familiar with the technology. Longitudinal studies that track satisfaction over extended periods would provide more stable assessments.
- Generalizability Considerations
- Organizational Context Factors
The participating organizations represented a variety of scales and service types, which enhances the generalizability of the findings within similar social work contexts. However, adaptation to organizations with significantly different structures, client populations, or regulatory requirements may necessitate substantial modifications. While the study’s focus on Taiwan’s social work system offers valuable insights, these findings may not directly apply to countries with differing healthcare systems, privacy regulations, or inter-agency collaboration frameworks.
- Technical Infrastructure Requirements
The performance of the system is contingent upon adequate technical infrastructure, including reliable internet connectivity, compatible devices, and technical support capabilities. Organizations lacking these prerequisites may experience divergent outcomes or may need to invest in additional infrastructure. The study’s emphasis on the integration of multi-vendor IoT devices instills confidence in the system’s adaptability; however, deployment in environments with limited vendor options or specialized device requirements may present additional challenges.
- Future Research Directions and Planned Enhancements
- Technical Development Priorities
- Integration of Federated Learning
Future advancements will prioritize the incorporation of federated learning methodologies to bolster privacy protection while facilitating collaborative machine learning among various organizations. This development will enable individual entities to leverage collective intelligence without jeopardizing client confidentiality through direct data exchange. Initial designs indicate that federated learning could enhance assessment accuracy by 15-20% while ensuring complete data locality. This strategy is consistent with the increasing focus on privacy-preserving artificial intelligence within the healthcare and social services sectors.
- Implementation of Quantum-Safe Security
In light of the long-term data retention requirements inherent in social work, forthcoming iterations will integrate quantum-safe encryption algorithms to safeguard data as quantum computing technologies evolve. This proactive measure addresses potential future vulnerabilities to existing cryptographic standards.
- Development of Cross-Chain Interoperability
The advancement of cross-chain bridging technologies will facilitate interoperability with other blockchain platforms, thereby promoting broader collaborative networks and alleviating concerns related to vendor lock-in. This enhancement is essential for ensuring the long-term sustainability of blockchain investments within social work organizations.
- Expansion of Application Scope
- Framework for International Collaboration
Future research will investigate the applicability of blockchain technologies in international social work contexts, encompassing areas such as refugee services, cross-border child protection, and disaster response coordination. The potential of the blockchain trust mechanism to facilitate international collaboration presents a significant opportunity for the advancement of global social work initiatives.
- Service Delivery in Rural and Remote Areas
The adaptation of the system for rural and remote communities will prioritize low-bandwidth connectivity, user-friendly interfaces, and offline functionality. These modifications aim to extend the system’s advantages to underserved populations and geographically isolated communities.
- Integration with Smart City Initiatives
Future developments will consider the integration of the system with broader smart city infrastructures, including healthcare systems, educational services, and emergency response networks. This expanded integration has the potential to create comprehensive support ecosystems for vulnerable populations.
- Research Contributions and Innovation Value
- Scientific Contributions
- Methodological Innovation
This research introduces a comprehensive framework for assessing the integration of blockchain technology with the Internet of Things (IoT) in social services, thereby offering a replicable methodology for analogous studies. The mixed-methods approach employed, which integrates quantitative performance metrics with qualitative evaluations of user experience, serves as a model for technology assessment within social work contexts. Furthermore, the cost-benefit analysis methodology utilized in this study, which encompasses direct labor savings, enhancements in operational efficiency, and improvements in quality, establishes a standardized framework for calculating return on investment (ROI) in the implementation of technology in social work.
- Empirical Evidence Generation
This investigation represents the first extensive empirical evaluation of the practical application of blockchain technology in social work case management. The quantified performance enhancements and user satisfaction metrics contribute significantly to the existing literature on technology in social work. Additionally, the thorough comparison with international systems such as SACWIS and ECASS establishes benchmark standards for the evaluation of social work technology and delineates specific performance targets for future implementations.
- Practical Innovation Impact
- Industry Standard Development
The technical specifications and performance benchmarks derived from this system contribute to the development of emerging industry standards for technology platforms in social work. The successful integration of 43 types of IoT devices from 15 different vendors illustrates practical solutions for interoperability, thereby informing best practices within the industry. Moreover, the privacy protection framework established in this study, which achieves 100% anonymization coverage while maintaining an analytical accuracy exceeding 91%, serves as a model for GDPR-compliant data management in social work.
- Organizational Transformation Template
Insights into change management presented in this study, including strategies for training, user support, and implementation timelines, offer a practical framework for social work organizations engaged in digital transformation initiatives. The demonstration of substantial efficiency gains—specifically, a 37.1% reduction in case processing time and a 73.3% improvement in filing efficiency—provides compelling evidence to support decisions regarding technology investments and organizational change initiatives.
- CONCLUSION
This study effectively illustrates the transformative potential inherent in the integration of blockchain and Internet of Things (IoT) technologies within social work case management systems. Over an 18-month development period, followed by a comprehensive 6-month pilot evaluation involving 249 participants across three institutions in Taiwan, the research provides substantial evidence regarding the efficacy of this technological amalgamation in addressing persistent challenges associated with social service delivery.
The implemented system demonstrated significant performance enhancements, including a 37.1% reduction in case processing time, an 87.3% increase in service efficiency, and a 26-fold increase in the frequency of inter-agency collaboration. These quantifiable improvements, alongside enhanced data security (99.8% prevention of unauthorized access), improved service quality (88.7% assessment accuracy), and high user satisfaction rates (82.4% among social workers and 85.7% among clients), lay a robust foundation for the digital transformation of social work practices.
The blockchain infrastructure achieved an impressive throughput of 850 transactions per second and maintained a system availability of 99.2%, significantly surpassing industry benchmarks and demonstrating the feasibility of distributed trust mechanisms in multi-organizational contexts. The IoT integration, which included 43 device types with a 97.8% connection success rate, facilitated real-time monitoring capabilities that fundamentally enhanced the proactive potential of social work interventions. Furthermore, machine learning algorithms, specifically Random Forest and Support Vector Machine (SVM) implementations, attained competitive accuracy rates of 89.4% and 87.3% respectively in assessment tasks, thereby supporting evidence-based decision-making processes.
A comparative analysis with international systems, such as SACWIS and ECASS, revealed notable advantages in real-time monitoring capabilities, inter-agency collaboration efficiency, and overall system responsiveness. The successful implementation of General Data Protection Regulation (GDPR)-compliant privacy protection mechanisms, achieving 100% anonymization coverage while maintaining analytical accuracy above 91%, effectively addresses critical concerns regarding client privacy in digitized social work environments.
The comprehensive cost-benefit analysis conducted in this study indicates a payback period of 2.8 years with a return on investment (ROI) of 41.2%, providing a strong economic rationale for the adoption of technology within social work organizations. The methodology employed to calculate annual savings of NT$2.35 million offers a replicable framework for financial planning in analogous implementations. However, the research acknowledges significant limitations, including a restricted sample scope (three organizations in Taiwan), a relatively brief evaluation period (6 months), and high initial implementation costs that may hinder accessibility for resource-constrained organizations.
Future research avenues include the integration of federated learning for enhanced privacy-preserving collaboration, the implementation of quantum-safe security measures for long-term data protection, and the expansion of frameworks for international cooperation and rural service delivery contexts. This study establishes critical precedents for evidence-based technology adoption in social work, providing empirical foundations for policy development and initiatives aimed at practice transformation.
This research signifies a substantial advancement in the theory and practice of digital social work, demonstrating that the thoughtful integration of emerging technologies can significantly enhance service delivery while upholding the human-centered values that are fundamental to the field. As social service organizations globally confront increasing demands and resource limitations, this study offers both inspiration and practical guidance for leveraging technology to better serve vulnerable populations and fortify community support systems.
The successful implementation detailed in this research paves the way for more efficient, effective, and equitable social service delivery, while underscoring the critical importance of maintaining a focus on client outcomes and professional values throughout the processes of technological transformation. The findings contribute essential knowledge for advancing both the theoretical understanding and practical application of technology in social work, thereby supporting the profession’s ongoing evolution in an increasingly digital landscape.
REFERENCES
- M. A. Saberi, H. Mcheick, and M. Adda, “From Data Silos to Health Records Without Borders: A Systematic Survey on Patient-Centered Data Interoperability,” Information, vol. 16, no. 2, p. 106, 2025, https://doi.org/10.3390/info16020106.
- L. Komna and S. Mpungose, “Investigating the impact of digital transformation in the public sector: A case study of the State Information Technology Agency (SITA), South Africa,” International Journal of Business Ecosystem & Strategy, vol. 6, no. 4, pp. 218–234, 2024, https://doi.org/10.47741/ijbes.v6i4.610.
- Q. Razi, R. Piyush, A. Chakrabarti, A. Singh, V. Hassija and G. S. S. Chalapathi, "Enhancing Data Privacy: A Comprehensive Survey of Privacy-Enabling Technologies," in IEEE Access, vol. 13, pp. 40354-40385, 2025, https://doi.org/10.1109/ACCESS.2025.3546618.
- V. Wylde, N. Rawindaran, J. Lawrence, R. Balasubramanian, E. Prakash, A. Jayal, and J. Platts, “Cybersecurity, data privacy and blockchain: A review,” SN Computer Science, vol. 3, no. 2, p. 127, 2022, https://doi.org/10.1007/s42979-022-01020-4.
- S. Prabowo et al., "Privacy-Preserving Tools and Technologies: Government Adoption and Challenges," in IEEE Access, vol. 13, pp. 33904-33934, 2025, https://doi.org/10.1109/ACCESS.2025.3540878.
- M. H. P. Rizi and S. A. H. Seno, “A systematic review of technologies and solutions to improve security and privacy protection of citizens in the smart city,” Internet of Things, vol. 20, p. 100584, 2022, https://doi.org/10.1016/j.iot.2022.100584.
- S. de Bell, S. Bell, Z. Zhelev, A. Bethel, J. T. Coon, J. Coon, and R. Anderson, “Factors influencing effective data sharing between health care and social care regarding the care of older people: a qualitative evidence synthesis,” Health and Social Care Delivery Research, vol. 12, no. 12, pp. 1-87, 2024, https://doi.org/10.3310/TTWG4738.
- J. Bae, S. Lee, and C. J. W. Choi, “Expansion of Digital Technology Use in the Korean Social Work Field,” Journal of Social Service Research, vol. 51, no. 3, pp. 663-677, 2025, https://doi.org/10.1080/01488376.2024.2402520.
- H. Belani, P. Šolić, E. Zdravevski, and V. Trajkovik, “Internet of Things Ontologies for Well-Being, Aging and Health: A Scoping Literature Review,” Electronics, vol. 14, no. 2, p. 394, 2025, https://doi.org/10.3390/electronics14020394.
- V. Della Mea, M. H. Popescu, D. Gonano, T. Petaros, I. Emili, and M. G. Fattori, “A communication infrastructure for the health and social care internet of things: Proof-of-concept study,” JMIR Medical Informatics, vol. 8, no. 2, p. e14583, 2020, https://doi.org/10.2196/14583.
- S. Choi, K. Kim, C. Kamyod, and C. G. Kim, “Ethical use of web-based welfare technology for caring elderly people who live alone in Korea: a case study,” Journal of Web Engineering, vol. 21, no. 4, pp. 1239-1264, 2022, https://doi.org/10.13052/jwe1540-9589.2141.
- P. Thottempudi, R. M. Konduru, H. B. Valiveti, K. Swaraja, and V. Kumar, “Digital health resilience: IoT solutions in pandemic response and future healthcare scenarios,” Discover Sustainability, vol. 6, no. 144, 2025, https://doi.org/10.1007/s43621-025-00886-7.
- J. C. D. Santos, “Blockchain for Enhancing Transparency and Accountability in Public Sector Governance,” in Enhancing Public Sector Accountability and Services Through Digital Innovation, pp. 73-128, 2025, https://doi.org/10.4018/979-8-3693-9251-5.ch003.
- D. Bhumichai, C. Smiliotopoulos, R. Benton, G. Kambourakis, and D. Damopoulos, “The convergence of artificial intelligence and blockchain: The state of play and the road ahead,” Information, vol. 15, no. 5, p. 268, 2024, https://doi.org/10.3390/info15050268.
- M. Thanasi-Boçe and J. Hoxha, “Blockchain for Sustainable Development: A Systematic Review,” Sustainability, vol. 17, no. 11, p. 4848, 2025, https://doi.org/10.3390/su17114848.
- Y. Saidu, S. M. Shuhidan, D. A. Aliyu, I. A. Aziz, and S. Adamu, “Convergence of Blockchain, IoT, and AI for Enhanced Traceability Systems: A Comprehensive Review,” IEEE Access, vol. 13, pp. 78541-78559, 2025, https://doi.org/10.1109/ACCESS.2025.3342689.
- T. Kukman and S. Gričar, “Blockchain for Quality: Advancing Security, Efficiency, and Transparency in Financial Systems,” FinTech, vol. 4, no. 1, p. 7, 2025, https://doi.org/10.3390/fintech4010007.
- C. A. Marino and C. Diaz Paz, “Smart Contracts and Shared Platforms in Sustainable Health Care: Systematic Review,” JMIR Medical Informatics, vol. 13, p. e58575, 2025. https://doi.org/10.2196/58575.
- L. K. Tong, H. L. Tam, and A. M. Mao, “A Bibliometric Review of Person-Centered Care Research 2010–2024,” Healthcare, vol. 13, no. 11, p. 1267, May 2025, https://doi.org/10.3390/healthcare13111267.
- T. C. Lin, L. L. Hwang, H. D. Dai, and Y. C. Sang, “Daily care information system requirements: professional service-driven service blueprint approach,” Applied Clinical Informatics, vol. 12, no. 04, pp. 960-968, 2021, https://doi.org/10.1055/s-0041-1736222.
- T. L. Chen, Y. H. Feng, S. L. Kao, J. W. Lu, and C. H. Loh, “Impact of integrated health care on elderly population: A systematic review of Taiwan’s experience,” Archives of Gerontology and Geriatrics, vol. 102, p. 104746, 2022, https://doi.org/10.1016/j.archger.2022.104746.
- J. C. D. Santos, “Blockchain for Enhancing Transparency and Accountability in Public Sector Governance,” in Enhancing Public Sector Accountability and Services Through Digital Innovation, pp. 73-128, 2025, https://doi.org/10.4018/979-8-3693-9251-5.ch003.
- R. Shevchuk, I. Lishchynskyy, M. Ciura, M. Lyzun, R. Kozak, and M. Kasianchuk, “Application of Blockchain Technology in Emergency Management Systems: A Bibliometric Analysis,” Applied Sciences, vol. 15, no. 10, p. 5405, 2025, https://doi.org/10.3390/app15105405.
- B. Dziundziuk and V. Dziundziuk, “Methodology for integrating blockchain into digital governance systems: analysis of challenges, benefits, and opportunities for society,” Science and Public Policy, vol. scaf022, 2025, https://doi.org/10.1093/scipol/scaf022.
- A. P. Rodriguez Müller, J. Martin Bosch, and L. Tangi, “An overview of the expected public values arising from blockchain adoption in the European public sector,” International Journal of Public Sector Management, vol. 38, no. 1, pp. 53-76, 2025, https://doi.org/10.1108/IJPSM-12-2023-0363.
- M. Thanasi-Boçe and J. Hoxha, “Blockchain for Sustainable Development: A Systematic Review,” Sustainability, vol. 17, no. 11, p. 4848, 2025, https://doi.org/10.3390/su17114848.
- F. O. Martínez-Ríos, J. A. Marmolejo-Saucedo, and G. Abascal-Olascoaga, “A New Protocol Based on Blockchain Technology for Transparent Operation of Corporate Social Responsibility,” in Strategy, Power and CSR: Practices and Challenges in Organizational Management, pp. 205-233, 2020, https://doi.org/10.1108/978-1-83867-973-620201012.
- V. G. Venkatesh, K. Kang, B. Wang, R. Y. Zhong, and A. Zhang, “System architecture for blockchain based transparency of supply chain social sustainability,” Robotics and Computer-Integrated Manufacturing, vol. 63, p. 101896, 2020, https://doi.org/10.1016/j.rcim.2019.101896.
- A. I. Aljumah, “Investigating the impact of blockchain technology on social sustainability and the mediating role of ethics and CSR,” Sustainability, vol. 15, no. 21, p. 15510, 2023, https://doi.org/10.3390/su152115510.
- P. Sarajoti, P. Chatjuthamard, S. Papangkorn, and P. Phiromswad, “CSR reporting and blockchain technology,” in Corporate Social Responsibility in the 21st Century, IntechOpen, 2023, https://doi.org/10.5772/intechopen.105512.
- C. A. Marino, and C. Diaz Paz, “Smart Contracts and Shared Platforms in Sustainable Health Care: Systematic Review,” JMIR Medical Informatics, vol. 13, e58575, 2025, https://doi.org/10.2196/58575.
- S. A. Baker, K. H. Thanoon, M. N. Abed, M. Almansor, T. Y. Abdulqader, and O. I. Alsaif, “A Secure and Privacy-Centric Blockchain Platform for Cloud-Based Healthcare Data Management,” in 2024 International Conference on IT Innovation and Knowledge Discovery (ITIKD), pp. 1-5, 2024, https://doi.org/10.1109/ITIKD54389.2024.11004752.
- M. Munawar, T. M. Singh, C. K. K. Reddy, and S. Doss, “Blockchain for Healthcare: Safe Data Sharing in the AIoMT Era,” in Utilizing AI of Medical Things for Healthcare Security and Sustainability, M. Ouaissa, M. Ouaissa, M. Imad, J. Qurashi, and M. Farooq, Eds., Hershey, PA: IGI Global, pp. 369-400, 2025, https://doi.org/10.4018/979-8-3373-0690-2.ch012.
- N. Y. Philip, J. J. P. C. Rodrigues, H. Wang, S. J. Fong, and J. Chen, “Internet of Things for In-Home Health Monitoring Systems: Current Advances, Challenges and Future Directions,” IEEE Journal on Selected Areas in Communications, vol. 39, no. 2, pp. 300-310, 2021, https://doi.org/10.1109/JSAC.2020.3042421.
- V. Della Mea, M. Popescu, D. Gonano, T. Petaros, I. Emili, and M. G. Fattori, “A Communication Infrastructure for the Health and Social Care Internet of Things: Proof-of-Concept Study,” JMIR Med Inform, vol. 8, no. 2, p. e14583, 2020, https://doi.org/10.2196/14583.
- S.-A. Moraru et al., “Using IoT Assistive Technologies for Older People Non-Invasive Monitoring and Living Support in Their Homes,” International Journal of Environmental Research and Public Health, vol. 19, no. 10, p. 5890, 2022, https://doi.org/10.3390/ijerph19105890.
- H. Belani, P. Šolić, E. Zdravevski, and V. Trajkovik, “Internet of Things Ontologies for Well-Being, Aging and Health: A Scoping Literature Review,” Electronics, vol. 14, no. 2, p. 394, 2025, https://doi.org/10.3390/electronics14020394.
- Y. Park and J. Han, “Smart Home Advancements for Health Care and Beyond: Systematic Review of Two Decades of User-Centric Innovation,” J Med Internet Res, vol. 27, e62793, 2025, https://doi.org/10.2196/62793.
- M. Jovanovic et al., “Ambient Assisted Living: Scoping Review of Artificial Intelligence Models, Domains, Technology, and Concerns,” J Med Internet Res, vol. 24, no. 11, p. e36553, 2022, https://doi.org/10.2196/36553.
- Z. Li and Z. Zhang, “Research and Implementation of Multi-chain Digital Wallet Based on Hash TimeLock,” in Blockchain and Trustworthy Systems, pp. 181-194, 2020, https://doi.org/10.1007/978-981-15-2777-7_15.
- W. H. Delone and E. R. McLean, “The DeLone and McLean Model of Information Systems Success: A Ten-Year Update,” Journal of Management Information Systems, vol. 19, no. 4, pp. 9-30, 2003, https://doi.org/10.1080/07421222.2003.11045748.
- Y. Pan, W. Wei, Y. Liu, and C. Zhu, “Hybrid consensus algorithm based on hierarchy authority,” in 2021 IEEE International Conference on Electronic Technology, Communication and Information (ICETCI), pp. 553–559, 2021, https://doi.org/10.1109/ICETCI53161.2021.9563559.
- A. Bogdanov, N. Shchegoleva, V. Khvatov, J. Kiyamov, and A. Dik, “Combining PBFT and Raft for Scalable and Fault-Tolerant Distributed Consensus,” Physics of Particles and Nuclei, vol. 55, no. 3, pp. 418-420, 2024, https://doi.org/10.1134/S1063779624030225.
- A. S. Isravel, D. P. and J. P. M. Dhas, “Quorum-based Tier Approach: Integrating PBFT and PoS in a Hybrid Consensus Mechanism,” in 2024 3rd International Conference on Automation, Computing and Renewable Systems (ICACRS), pp. 147-154, 2024, https://doi.org/10.1109/ICACRS62842.2024.10841565.
- W. Sun et al., “An improved PBFT consensus mechanism with trust value evaluation application in the agricultural product trusted traceability system,” Journal of High Speed Networks, vol. 29, no. 4, pp. 321-336, 2023, https://doi.org/10.3233/JHS-222077.
- J. Tan, S. B. Goyal, A. Singh Rajawat, T. Jan, N. Azizi, M. Prasad, “Anti-Counterfeiting and Traceability Consensus Algorithm Based on Weightage to Contributors in a Food Supply Chain of Industry 4.0,” Sustainability, vol. 15, no. 10, 7855, 2023, https://doi.org/10.3390/su15107855.
- B. Shan, T. Gao, L. Song, and Y. Cui, “Grouped Byzantine Fault-Tolerant Consensus Mechanism Based on Node Behaviour Analysis,” in 2025 4th International Symposium on Computer Applications and Information Technology (ISCAIT), pp. 1890-1895, 2025, https://doi.org/10.1109/ISCAIT64916.2025.11010760.
- X. Gu, T. Kang, A. Zhou, and L. Guo, “Consensus Node Group Selection and Adjustment Algorithm Based on Dual Random Selection Mechanism,” Proceedings of the 2023 9th International Conference on Communication and Information Processing (ICCIP ‘23), pp. 407-414, 2024, https://doi.org/10.1145/3638884.3638947.
- N. Sun, Q. Hu, L. Yao, Improved Practical Byzantine Fault Tolerance Consensus Mechanism with Two-stage Verification. International Journal of Frontiers in Engineering Technology, vol. 4, no. 5, 2022, https://doi.org/10.25236/IJFET.2022.040512.
- H. Luo, X. Yang, H. Yu, G. Sun, S. Xu, and L. Luo, “Performance Analysis of Non-ideal Wireless PBFT Networks with mmWave and Terahertz Signals,” 2023 IEEE International Conference on Metaverse Computing, Networking and Applications (MetaCom), pp. 104-108, 2023, https://doi.org/10.1109/MetaCom57706.2023.00030.
- J. Tan, S. B. Goyal, A. Singh Rajawat, T. Jan, N. Azizi, and M. Prasad, “Anti-Counterfeiting and Traceability Consensus Algorithm Based on Weightage to Contributors in a Food Supply Chain of Industry 4.0,” Sustainability, vol. 15, no. 10, p. 7855, 2023, https://doi.org/10.3390/su15107855.
- Z. Zhang, D. Zhu, and W. Fan, “QPBFT: Practical Byzantine Fault Tolerance Consensus Algorithm Based on Quantified-Role,” in 2020 IEEE 19th International Conference on Trust, Security and Privacy in Computing and Communications (TrustCom), pp. 991-997, 2020, https://doi.org/10.1109/TrustCom50675.2020.00132.
- S. Subha, S. B. Priya, “Comparative Analysis of Supervised Machine Learning Algorithms for Evaluating the Performance Level of Students,” 2021 Fifth International Conference on I-SMAC (IoT in Social, Mobile, Analytics and Cloud) (I-SMAC), pp. 1-10, 2021, https://doi.org/10.1109/I-SMAC52330.2021.9640798.
- N. Nasution, M. A. Hasan, F. Bakri Nasution, “Predicting Heart Disease Using Machine Learning: An Evaluation of Logistic Regression, Random Forest, SVM, and KNN Models on the UCI Heart Disease Dataset,” IT Journal Research and Development, vol. 9, no. 2, pp. 140–150, 2025, https://doi.org/10.25299/itjrd.2025.17941.
- M. H. Ting, C. M. Chu, G. Zeng, D. Li, and G. S. Chng, “Predicting recidivism among youth offenders: Augmenting professional judgement with machine learning algorithms,” Journal of Social Work, vol. 18, no. 6, pp. 631-649, 2017, https://doi.org/10.1177/1468017317743137.
- D. Mehta, “A Comparative Study of Machine Learning Algorithms for Predictive Healthcare: Applications in Diabetes Management and Breast Cancer Detection,” Saudi J Med, Vol. 10, No. 2, pp. 59-67, 2025, https://doi.org/10.36348/sjm.2025.v10i02.005.
- O. A. Bukhari, A. O. Maghraby, “Using Machine Learning for Automatic Correction of Numerical Analysis Assignments Towards Sustainable Education Development,” 2022 Fifth National Conference of Saudi Computers Colleges (NCCC), pp. 47-51, 2022, https://doi.org/10.1109/NCCC57165.2022.10067409.
- M. Nuwasiima, M. P. Ahonon, and C. Kadiri, “The Role of Artificial Intelligence (AI) and machine learning in social work practice,” World Journal of Advanced Research and Reviews, vol. 24, no. 01, pp. 080–097, 2024, https://doi.org/10.30574/wjarr.2024.24.1.2998.
- C. S. Kumar and R. J. Sree, “Assessment of Performances of Various Machine Learning Algorithms During Automated Evaluation of Descriptive Answers,” ICTACT Journal on Soft Computing, vol. 4, no. 4, 2014, https://doi.org/10.21917/ijsc.2014.0111.
- A. Goldsteen, G. Ezov, R. Shmelkin, et al., Data minimization for GDPR compliance in machine learning models, AI Ethics, Vol. 2, pp. 477–491, 2022, https://doi.org/10.1007/s43681-021-00095-8.
- M. R. Juliansyah, A. Pratama, R. I. Putra, M. Y. A. Putra, and M. F. Fathurrahman, “A Performance Analysis of Hyperledger Fabric for Blockchain-Based Concert Ticketing Systems,” 2024 International Conference on Electrical Engineering and Computer Science (ICECOS), pp. 147-151, 2024, https://doi.org/10.1109/ICECOS63900.2024.10791096.
- S. Ghosh and M. Dutta, “Indriya: Building a Secure and Transparent Organ Donation System with Hyperledger Fabric,” TechRxiv, 2023, https://doi.org/10.36227/techrxiv.22225999.v1.
- B. I. Onyeashie, M. Abubakar, P. Leimich, S. McKeown and G. Russell, “Privacy-Preserving and Scalable Digital Evidence Management: A Hyperledger Fabric Architecture with Growth Projections for Law Enforcement,” International Conference on New Trends in Computing Sciences (ICTCS), pp. 105-112, 2025, https://doi.org/10.1109/ICTCS65341.2025.10989348.
- D. Kelsey, “Benchmarking Hyperledger Fabric 2.5 Performance,” Hyperledger Foundation Blog, 2023. https://www.lfdecentralizedtrust.org/blog/2023/02/16/benchmarking-hyperledger-fabric-2-5-performance.
- A. A. A. Dallaf, “Edge Computing in IoT Networks: Enhancing Efficiency, Reducing Latency, and Improving Scalability,” International Journal of Advanced Network, Monitoring and Controls, vol. 10, no. 1, pp. 103-115, 2025, https://doi.org/10.2478/ijanmc-2025-0009.
- M. M. Khan, F. S. Khan, M. Nadeem, T. H. Khan, S. Haider, and D. Daas, “Scalability and Efficiency Analysis of Hyperledger Fabric and Private Ethereum in Smart Contract Execution,” Computers, vol. 14, no. 4, pp. 132, 2025, https://doi.org/10.3390/computers14400132.
- A. A. Salih and Y. Wang, “BDLS as a Blockchain Finality Gadget: Improving Byzantine Fault Tolerance in Hyperledger Fabric,” IEEE Access, vol. 12, pp. 154600-154613, 2024, https://doi.org/10.1109/ACCESS.2024.3481319.
- A. F. Abdulqader, S. H. Ahmed, and M. A. Khan, “Optimizing IoT Performance Through Edge Computing: Reducing Latency, Enhancing Bandwidth Efficiency, and Strengthening Security for 2025 Applications,” 2024 36th Conference of Open Innovations Association (FRUCT), pp. 145–158, 2024, https://doi.org/10.23919/FRUCT64283.2024.10749858.
- K. P. B. Kanagarla, Edge Computing and Analytics for IoT Devices: Enhancing Real-Time Decision Making in Smart Environments. 2024. https://doi.org/10.2139/ssrn.5012466.
- S. N., M. G., V. M., M. Shaid, S. Purushothman, and V. G. Sanjai, “Accurate Prediction and Detection of Suicidal Risk using Random Forest Algorithm,” 2024 4th International Conference on Pervasive Computing and Social Networking (ICPCSN), pp. 287–292, 2024, https://doi.org/10.1109/ICPCSN62568.2024.00053.
- M. Abdulla-Hil-Kafi, M. A. Sheakh, M. A. Oishe, M. M. Islam, M. M. R. Foysal, and T. Sarwar, “Classification of Maternal Health Risk Factors Using Machine Learning Approach,” 2024 International Conference on Social and Sustainable Innovations in Technology and Engineering (SASI-ITE), pp. 1–6, 2024, https://doi.org/10.1109/SASI-ITE58663.2024.00009.
- V. A. R., S. Yerra, S. N. G., Gandikota, P. Advancements in Heart Disease Prediction: A Machine Learning Approach for Early Detection and Risk Assessment. Int. J. Sci. Res. (IJSR), vol. 13, no. 10, pp. 774–780, 2024, https://www.doi.org/10.21275/SR241004171836.
- T. Zhang, D. Wang, Y. Lu, Machine learning-enabled regional multi-hazards risk assessment considering social vulnerability, Scientific Reports, vol. 13, p. 13405, 2023, https://doi.org/10.1038/s41598-023-40159-9.
- O. Kalaycıoğlu, S. E. Akhanlı, E. Y. Menteşe, M. Kalaycıoğlu, and S. Kalaycıoğlu, “Using machine learning algorithms to identify predictors of social vulnerability in the event of a hazard: Istanbul case study,” Nat. Hazards Earth Syst. Sci., vol. 23, pp. 2133–2156, 2023, https://doi.org/10.5194/nhess-23-2133-2023.
- L. Li, M. Wang, M. Jian, “Artificial Intelligence-Assisted Case Management in Social Work Services: A Systematic Review,” Research on Social Work Practice, p. 10497315251329531, 2025, https://doi.org/10.1177/10497315251329531.
- A. Ranerup, L. Svensson, “Automated decision-making, discretion and public values: a case study of two municipalities and their case management of social assistance,” European Journal of Social Work, vol. 26, no. 5, pp. 948–962, 2023, https://doi.org/10.1080/13691457.2023.2185875.
- W. S. N. Wati, B. Santoso, and D. Cahyono, “Evaluation Hospital Information System Implementation Using Technology Acceptance Model to Enhance Patient Satisfaction,” SENTRALISASI, vol. 14, no. 2, pp. 49–69, 2025, https://doi.org/10.33506/sl.v14i2.4232.
- N. E. Özdemir, G. Cerev, D. B. Sarıipek, and S. Tosun, “Blockchain Technology and Social Policy Transformation: A Critical Examination and Recommendations,” Sosyal Siyaset Konferansları Dergisi, no. 87, pp. 15–23, 2024, https://doi.org/10.26650/jspc.2024.87.1468729.
- C. A. Marino, C. Diaz Paz, “Smart Contracts and Shared Platforms in Sustainable Health Care: Systematic Review,” JMIR Medical Informatics, vol. 13, p. e58575, 2025, https://doi.org/10.2196/58575.
- P. Sharma, S. S. A. S. S. Ali, “Enhancing Pharmaceutical Supply Chains through Blockchain Technology on Hyperledger Fabric Implementation,” Journal of Angiotherapy, vol. 8, no. 9, pp. 1–7, 2024, https://doi.org/10.25163/angiotherapy.899872.
- A. N. Murphy, M. A. Scotellaro, M. Carroll, and H. J. Risser, “A critical examination of Illinois’ child welfare information systems and its utility for identifying and monitoring children and youth with special health care needs for front- and back-end users,” Disability and Health Journal, vol. 17, no. 1, p. 101537, 2024, https://doi.org/10.1016/j.dhjo.2023.101537.
- K.H.B. Chor et al., “Exploring Machine Learning to Support Decision-Making for Placement Stabilization and Preservation in Child Welfare,” Journal of Child and Family Studies, vol. 34, pp. 282–297, 2025, https://doi.org/10.1007/s10826-024-02993-x.
- M. Goulbourne et al., “Deliberate Self-Harm Among Youth in the Child Welfare System,” JAACAP Open, 2025, https://doi.org/10.1016/j.jaacop.2025.04.002.
- T. L. Quy et al., “Transforming Child Health Records: Integrating Blockchain, NFTs, and IPFS for Enhanced Medical Data Management,” in Mobile, Secure, and Programmable Networking. MSPN 2023. Lecture Notes in Computer Science, vol. 14482, 2024, https://doi.org/10.1007/978-3-031-52426-4_9.
- E. Anastasopoulou, A. Tsagri, and E. Mitroyanni, “Transforming Greek Primary Education through Information Systems: Trends and Challenges,” Asian Journal of Education and Social Studies, vol. 51, no. 6, pp. 43-61, 2025, https://doi.org/10.9734/ajess/2025/v51i61978.
- D. Laumann et al., “Mobile learning in the classroom – Should students bring mobile devices for learning, or should these be provided by schools?,” Educ. Inf. Technol., vol. 30, pp. 9463–9496, 2025, https://doi.org/10.1007/s10639-024-13213-w.
- B. Wang, B. Jiang, D. Liu, and R. Zhu, “Early Predictive Accuracy of Machine Learning for Hemorrhagic Transformation in Acute Ischemic Stroke: Systematic Review and Meta-Analysis,” J Med Internet Res, vol. 27, p. e71654, 2025, https://doi.org/10.2196/71654.
AUTHOR BIOGRAPHY

| Yih-Chang Chen holds a Master of Science in Information Systems Security from the London School of Economics and Political Science (LSE), University of London, as well as a Doctorate in Computer Science from the University of Warwick, United Kingdom. He presently serves as an Assistant Professor in both the Bachelor Degree Program in Medical Sociology and Health Care and the Department of Information Management at Chang Jung Christian University in Taiwan. His academic expertise encompasses a range of interdisciplinary fields, including artificial intelligence (AI), software engineering, machine learning, social media applications, social work management, and long-term care. His research is motivated by a dedication to bridging the divide between technology and its social applications. He actively participates in cross-disciplinary initiatives that merge information technology, management science, and social welfare to address complex societal and healthcare issues. In addition to his academic duties, he is currently an Audit Committee Member in the President Office at Chang Jung Christian University and leads projects under the auspices of Taiwan’s Ministry of Labor, specifically aimed at the development and implementation of Employment-Oriented Curriculum Programs. |
|
|

| Chia-Ching Lin received her Ph.D. from Kobe University, Japan. She is currently an Assistant Professor in the Department of Finance at Chang Jung Christian University, Taiwan. Her research expertise spans across multiple domains including investment, portfolio management, financial management, insurance, international financial management, and financial securities regulations. Her academic contributions are marked by an interdisciplinary approach, integrating financial theory with practical insights to address globally relevant issues in economics and management. In addition to her academic endeavors, she had led the Ministry of Labor-funded employment program initiatives aimed at advancing career-oriented curriculum development and workforce readiness. Her professional trajectory reflects a deep commitment to bridging academic research with policy application and cross-sector collaboration in finance, management, and public service. |
Yih-Chang Chen (A Blockchain-Enabled Internet of Things Framework for Enhancing Trust and Privacy in Social Work Case Management)